- Cisco Community
- Technology and Support
- Security
- Network Security
- How to Permit traffic from Outside to DMZ on ASA 8.4
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to Permit traffic from Outside to DMZ on ASA 8.4
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2013 01:58 PM - edited 03-11-2019 05:51 PM
Hello, everyone, i am writing you for help me.
I Have this Topology:
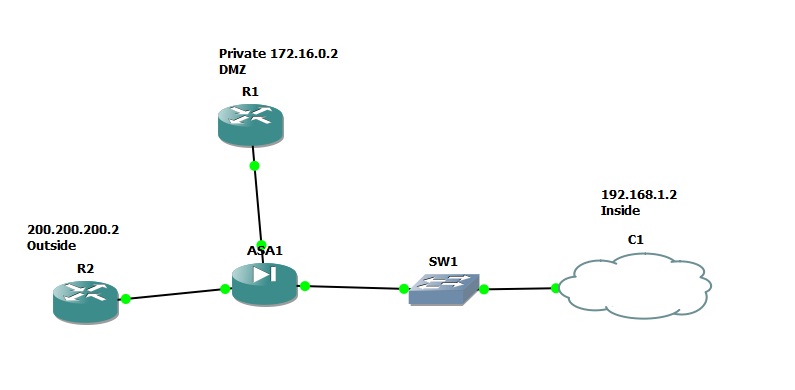
R1 is as server and i want to public that server in INTERNET using public IP 7.7.7.7, but i can not do that. I tried to do a NAT but it just translate from DMZ to Outside, however i can not to ping to 7.7.7.7 from Outside (R2).
I have a route in R2
7.7.7.7 [1/0] via 200.200.200.1
On R2 i can´t ping to 7.7.7.7
On R2 i can´t ping to 172.16.0.2
On R1 i can ping to 200.200.200.2
On Inside i can ping to 172.16.0.2
when i try to ping from DMZ to Outside (200.200.200.2) the debug, and show nat details, show me:
ciscoasa(config)# nat: translation - dmz:172.16.0.2/26 to outside:7.7.7.7/26
nat: untranslation - outside:7.7.7.7/26 to dmz:172.16.0.2/26
nat: untranslation - outside:7.7.7.7/26 to dmz:172.16.0.2/26
nat: untranslation - outside:7.7.7.7/26 to dmz:172.16.0.2/26
ciscoasa(config)#
ciscoasa(config)# sh nat detail
Auto NAT Policies (Section 2)
1 (dmz) to (outside) source static obj-172.16.0.2 7.7.7.7
translate_hits = 2, untranslate_hits = 2
Source - Origin: 172.16.0.2/32, Translated: 7.7.7.7/32
When i try to ping from Outside to DMZ using public IP (7.7.7.7) the debug and show nat detail, show me:
ciscoasa(config)# nat: untranslation - outside:7.7.7.7/0 to dmz:172.16.0.2/0
nat: untranslation - outside:7.7.7.7/0 to dmz:172.16.0.2/0
nat: untranslation - outside:7.7.7.7/0 to dmz:172.16.0.2/0
nat: untranslation - outside:7.7.7.7/0 to dmz:172.16.0.2/0
nat: untranslation - outside:7.7.7.7/0 to dmz:172.16.0.2/0
nat: untranslation - outside:7.7.7.7/0 to dmz:172.16.0.2/0
nat: untranslation - outside:7.7.7.7/0 to dmz:172.16.0.2/0
nat: untranslation - outside:7.7.7.7/0 to dmz:172.16.0.2/0
nat: untranslation - outside:7.7.7.7/0 to dmz:172.16.0.2/0
nat: untranslation - outside:7.7.7.7/0 to dmz:172.16.0.2/0
ciscoasa(config)# sh nat det
Auto NAT Policies (Section 2)
1 (dmz) to (outside) source static obj-172.16.0.2 7.7.7.7
translate_hits = 2, untranslate_hits = 7
Source - Origin: 172.16.0.2/32, Translated: 7.7.7.7/32
In ASA my configuration is this:
ASA Version 8.4(2)
!
hostname ciscoasa
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface GigabitEthernet0
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface GigabitEthernet1
nameif dmz
security-level 50
ip address 172.16.0.1 255.255.255.0
!
interface GigabitEthernet2
nameif outside
security-level 0
ip address 200.200.200.1 255.255.255.0
!
interface GigabitEthernet3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet5
shutdown
no nameif
no security-level
no ip address
!
ftp mode passive
object network obj-172.16.0.2
host 172.16.0.2
access-list pingc extended permit icmp any any echo-reply
access-list pingc extended permit icmp any any unreachable
access-list pingc extended permit tcp any host 200.200.200.2 eq www
access-list pingc extended permit icmp any host 200.200.200.2
access-list pingc extended deny ip any any
access-list webicmp extended permit tcp 192.168.1.0 255.255.255.0 host 172.16.0.2 eq www
access-list webicmp extended permit icmp 192.168.1.0 255.255.255.0 host 172.16.0.2
access-list webicmp extended deny ip any any
access-list public extended permit tcp any host 7.7.7.7 eq www
access-list public extended permit icmp any host 7.7.7.7
access-list public extended permit icmp any any echo-reply
access-list public extended permit icmp any any unreachable
access-list public extended deny ip any any
pager lines 24
mtu inside 1500
mtu dmz 1500
mtu outside 1500
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
!
object network obj-172.16.0.2
nat (dmz,outside) static 7.7.7.7
access-group webicmp in interface inside
access-group pingc in interface dmz
access-group public in interface outside
route dmz 7.7.7.7 255.255.255.255 172.16.0.2 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect ip-options
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
crashinfo save disable
Cryptochecksum:5d5522548310b4842b3b21003cc3470a
: end
Thanks a lot, I hope that you help me.
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2013 02:08 PM
Hi,
Change your "public" ACL to use the DMZ R1 actual IP address instead of the NAT IP address
- In ASA software 8.2 and ealier you use the NAT IP address in the ACL statements
- In ASA software 8.3 and after you use the Actual/Local IP address in the ACL statements
In other words replace 7.7.7.7 in the ACL with 172.16.0.2 and you should be able to ping R1 from outside
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2013 08:02 AM
Hello, thank you so much for answer!!!!!!!!!!!!!
I changed that, and it worked.
R2#ping 7.7.7.7
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 7.7.7.7, timeout is 2 seconds:
!!!!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2013 08:09 AM
Glad to know its working
Please rate any answers you have found helpfull
And as Karsten stated earlier. The "inspect icmp" is good to have on the firewall so you dont have to allow ICMP return traffic on an ACL because the inspect handles that automatically.
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2013 08:22 AM
OK, i already did that. All pings works. Now my access lists are:
access-list pingc extended permit icmp any any unreachable
access-list pingc extended permit tcp any host 200.200.200.2 eq www
access-list pingc extended permit icmp any host 200.200.200.2
access-list pingc extended deny ip any any
access-list webicmp extended permit tcp 192.168.1.0 255.255.255.0 host 172.16.0.2 eq www
access-list webicmp extended permit icmp 192.168.1.0 255.255.255.0 host 172.16.0.2
access-list webicmp extended deny ip any any
access-list public extended permit tcp any host 172.16.0.2 eq www
access-list public extended permit icmp any host 172.16.0.2
access-list public extended permit icmp any any unreachable
access-list public extended deny ip any any
Is already everything ok?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2013 08:32 AM
Hi,
I guess if the ICMP is going through now then your original problem has been solved.
Is there something else thats not working?
I assume you are running this ASA Configuration on GNS3 (Though I havent really used it myself)
Some usual configuration that you are missing are
- Default PAT configuration
- Default route
And the route for "dmz" is not needed.
But if you are just testing things the above dont really matter.
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2013 10:50 PM
And in addition to the ACL-change that Jouni told you, you should also enable ICMP-inspection:
policy-map global_policy
class inspection_default
inspect icmp
With that you don't need to allow the echo-reply statically in your ACLs.
Sent from Cisco Technical Support iPad App
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:




