- Cisco Community
- Technology and Support
- Security
- Network Security
- ISR4331/K9-Zone based firewall configuration.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2019 02:51 PM - edited 02-21-2020 08:49 AM
Hello All,
Cisco ISR4331/K9 Router, Cisco IOS XE Software, Version 03.16.04b.S - Extended Support Release
Cisco IOS Software, ISR Software (X86_64_LINUX_IOSD-UNIVERSALK9-M), Version 15.5(3)S4b, RELEASE SOFTWARE (fc1).
The router is configured with Zone-Based Firewall configuration to handle all my customer traffic. I have created extended access-lists and associated the class-map to it, Everything is working fine but I am not able to see any hits my ACL logs. Can someone please advise.
Router Configuration:
class-map type inspect match-any E_FW_OUTSIDE_TO_SLF_98_CLASS_MAP
match access-group name E_FW_OUTSIDE_TO_SLF_ACL_04
class-map type inspect match-any E_FW_SLF_TO_OUTSIDE_98_CLASS_MAP
match access-group name E_FW_SLF_TO_OUTSIDE_ACL_06
class-map type inspect match-all E_FW_INSIDE_TO_OUTSIDE_CLASS_MAP
match access-group name E_FW_INSIDE_TO_OUTSIDE_ACL_01
class-map type inspect match-any E_FW_OUTSIDE_TO_INSIDE_CLASS_MAP
match access-group name E_FW_OUTSIDE_TO_INSIDE_ACL_03
class-map type inspect match-any E_FW_INSIDE_TO_SLF_98_CLASS_MAP
match access-group name E_FW_INSIDE_TO_SLF_ACL_02
class-map type inspect match-any E_FW_SLF_TO_INSIDE_98_CLASS_MAP
match access-group name E_FW_SLF_TO_INSIDE_ACL_05
policy-map type inspect E_FW_OUTSIDE_TO_INSIDE_POLICY_MAP
class type inspect E_FW_OUTSIDE_TO_INSIDE_CLASS_MAP
inspect E_FW_GLOBAL_PARAMETER_MAP
class class-default
drop log
policy-map type inspect E_FW_INSIDE_TO_SLF_POLICY_MAP
class type inspect E_FW_INSIDE_TO_SLF_98_CLASS_MAP
pass
class class-default
drop log
policy-map type inspect E_FW_INSIDE_TO_OUTSIDE_POLICY_MAP
class type inspect E_FW_INSIDE_TO_OUTSIDE_CLASS_MAP
inspect E_FW_GLOBAL_PARAMETER_MAP
class class-default
drop log
policy-map type inspect E_FW_SLF_TO_OUTSIDE_POLICY_MAP
class type inspect E_FW_SLF_TO_OUTSIDE_98_CLASS_MAP
pass
class class-default
drop log
policy-map type inspect E_FW_OUTSIDE_TO_SLF_POLICY_MAP
class type inspect E_FW_OUTSIDE_TO_SLF_98_CLASS_MAP
pass
class class-default
drop log
policy-map type inspect E_FW_SLF_TO_INSIDE_POLICY_MAP
class type inspect E_FW_SLF_TO_INSIDE_98_CLASS_MAP
pass
class class-default
drop log
zone security E_FW_INSIDE_ZONE
description --- CUSTOMER_ZONE_ACCESS_SECURITY_ZONE
zone security E_FW_OUTSIDE_ZONE
description --- OUTSIDE ZONE_ACCESS_SECURITY_ZONE
description --- CUSTOMER_ZONE_INTERNET_ACCESS_ZONE_PAIRING
service-policy type inspect E_FW_INSIDE_TO_OUTSIDE_POLICY_MAP
zone-pair security E_FW_ZON_PAIR_INSIDE_TO_SLF source E_FW_INSIDE_ZONE destination self
description --- Customer LAN to Router originated traffic
service-policy type inspect E_FW_INSIDE_TO_SLF_POLICY_MAP
zone-pair security E_FW_ZON_PAIR_OUTSIDE_TO_INSIDE source E_FW_OUTSIDE_ZONE destination E_FW_INSIDE_ZONE
description --- OUTSIDE ZONE_INTERNET_ACCESS_ZONE_PAIRING
service-policy type inspect E_FW_OUTSIDE_TO_INSIDE_POLICY_MAP
zone-pair security E_FW_ZON_PAIR_OUTSIDE_TO_SLF source E_FW_OUTSIDE_ZONE destination self
description --- Public internet to router originated traffic
service-policy type inspect E_FW_OUTSIDE_TO_SLF_POLICY_MAP
zone-pair security E_FW_ZON_PAIR_SLF_TO_INSIDE source self destination E_FW_INSIDE_ZONE
description --- Router originated traffic to customer LAN
service-policy type inspect E_FW_SLF_TO_INSIDE_POLICY_MAP
zone-pair security E_FW_ZON_PAIR_SLF_TO_OUTSIDE source self destination E_FW_OUTSIDE_ZONE
description --- Router to IPSN
service-policy type inspect E_FW_SLF_TO_OUTSIDE_POLICY_MAP
Thanks in advance.
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2019 09:22 AM
Perhaps it's this command on your version:- show policy-map type inspect zone-pair
From there you should be able to determine matches against your class-maps
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2019 12:32 PM - edited 02-20-2019 12:47 PM
Hi,
You haven't uploaded the full configuration but you do have the zone defined on each of the interfaces?
When using ZBFW if using an ACL inconjuction with a class-map you should be able to determine "hits" when using the command "show ip access-list", however you cannot use the log command on an ACE to get a log entry. For which traffic are you expecting to see logs for?
Instead of checking the ACL for hit counts you can use the command "show policy-firewall stats zone-pair YOUR_ZONE_NAME" which should will indicate if packets match the class-map.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2019 02:48 PM - edited 02-21-2019 07:05 AM
This is my Full Config and I wasn't able to determine any hits if do "show IP access-list" no hits at all. I tried the command you mentioned but no luck. Please advise after you going through the config if anything needs to be changed.
Thanks in advance.
show config
Using 29302 out of 33554432 bytes
version 15.5
service timestamps debug datetime msec localtime
service timestamps log datetime msec localtime
service password-encryption
service sequence-numbers
no platform punt-keepalive disable-kernel-core
!
hostname Bluetide_Orange_Atlanta
!
boot-start-marker
boot-end-marker
!
!
vrf definition Mgmt-intf
!
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
no aaa new-model
clock timezone central -6 0
clock summer-time CDT recurring
!
!
!
!
!
!
!
!
!
!
!
ip name-server 204.59.152.208 57.67.127.192 57.73.127.195
ip domain name equant.net
!
!
!
login delay 10
login quiet-mode access-class 199
!
!
!
!
!
!
!
--More-- subscriber templating
!
parameter-map type inspect E_FW_GLOBAL_PARAMETER_MAP
max-incomplete low 20000000
max-incomplete high 20000000
one-minute low 100000000
one-minute high 100000000
tcp max-incomplete host 100000 block-time 0
multilink bundle-name authenticated
!
!
!
!
cts logging verbose
license udi pid ISR4331/K9 sn FDO2146149C
!
spanning-tree extend system-id
!
redundancy
mode none
!
!
!
!
!
vlan internal allocation policy ascending
!
track 20 ip sla 20 reachability
!
track 25 ip sla 25 reachability
!
track 99 list boolean and
object 20
object 25
!
!
class-map type inspect match-any E_FW_OUTSIDE_TO_SLF_98_CLASS_MAP
match access-group name E_FW_OUTSIDE_TO_SLF_ACL_04
class-map type inspect match-any E_FW_SLF_TO_OUTSIDE_98_CLASS_MAP
match access-group name E_FW_SLF_TO_OUTSIDE_ACL_06
class-map type inspect match-all E_FW_INSIDE_TO_OUTSIDE_CLASS_MAP
match access-group name E_FW_INSIDE_TO_OUTSIDE_ACL_01
class-map type inspect match-any E_FW_OUTSIDE_TO_INSIDE_CLASS_MAP
match access-group name E_FW_OUTSIDE_TO_INSIDE_ACL_03
class-map type inspect match-any E_FW_INSIDE_TO_SLF_98_CLASS_MAP
match access-group name E_FW_INSIDE_TO_SLF_ACL_02
class-map type inspect match-any E_FW_SLF_TO_INSIDE_98_CLASS_MAP
match access-group name E_FW_SLF_TO_INSIDE_ACL_05
!
policy-map type inspect E_FW_OUTSIDE_TO_INSIDE_POLICY_MAP
class type inspect E_FW_OUTSIDE_TO_INSIDE_CLASS_MAP
inspect E_FW_GLOBAL_PARAMETER_MAP
class class-default
drop log
policy-map type inspect E_FW_INSIDE_TO_SLF_POLICY_MAP
class type inspect E_FW_INSIDE_TO_SLF_98_CLASS_MAP
pass
class class-default
drop log
--More-- policy-map type inspect E_FW_INSIDE_TO_OUTSIDE_POLICY_MAP
class type inspect E_FW_INSIDE_TO_OUTSIDE_CLASS_MAP
inspect E_FW_GLOBAL_PARAMETER_MAP
class class-default
drop log
policy-map type inspect E_FW_SLF_TO_OUTSIDE_POLICY_MAP
class type inspect E_FW_SLF_TO_OUTSIDE_98_CLASS_MAP
pass
class class-default
drop log
policy-map type inspect E_FW_OUTSIDE_TO_SLF_POLICY_MAP
class type inspect E_FW_OUTSIDE_TO_SLF_98_CLASS_MAP
pass
class class-default
drop log
policy-map type inspect E_FW_SLF_TO_INSIDE_POLICY_MAP
class type inspect E_FW_SLF_TO_INSIDE_98_CLASS_MAP
pass
class class-default
drop log
!
zone security E_FW_INSIDE_ZONE
description --- CUSTOMER_ZONE_ACCESS_SECURITY_ZONE
zone security E_FW_OUTSIDE_ZONE
description --- OUTSIDE ZONE_ACCESS_SECURITY_ZONE
zone-pair security E_FW_ZON_PAIR_INSIDE_TO_OUTSIDE source E_FW_INSIDE_ZONE destination E_FW_OUTSIDE_ZONE
description --- CUSTOMER_ZONE_INTERNET_ACCESS_ZONE_PAIRING
service-policy type inspect E_FW_INSIDE_TO_OUTSIDE_POLICY_MAP
zone-pair security E_FW_ZON_PAIR_INSIDE_TO_SLF source E_FW_INSIDE_ZONE destination self
description --- Customer LAN to Router originated traffic
service-policy type inspect E_FW_INSIDE_TO_SLF_POLICY_MAP
zone-pair security E_FW_ZON_PAIR_OUTSIDE_TO_INSIDE source E_FW_OUTSIDE_ZONE destination E_FW_INSIDE_ZONE
description --- OUTSIDE ZONE_INTERNET_ACCESS_ZONE_PAIRING
service-policy type inspect E_FW_OUTSIDE_TO_INSIDE_POLICY_MAP
zone-pair security E_FW_ZON_PAIR_OUTSIDE_TO_SLF source E_FW_OUTSIDE_ZONE destination self
description --- Public internet to router originated traffic
service-policy type inspect E_FW_OUTSIDE_TO_SLF_POLICY_MAP
zone-pair security E_FW_ZON_PAIR_SLF_TO_INSIDE source self destination E_FW_INSIDE_ZONE
description --- Router originated traffic to customer LAN
service-policy type inspect E_FW_SLF_TO_INSIDE_POLICY_MAP
zone-pair security E_FW_ZON_PAIR_SLF_TO_OUTSIDE source self destination E_FW_OUTSIDE_ZONE
description --- Router to IPSN
service-policy type inspect E_FW_SLF_TO_OUTSIDE_POLICY_MAP
!
!
!
!
!
!
crypto isakmp policy 20
encr aes 256
hash sha256
authentication pre-share
group 14
crypto isakmp key MRSKvpnBTCenc117 address X.X.X.X
crypto isakmp key MRSKvpnBTCenc117 address 0.0.0.0
crypto isakmp invalid-spi-recovery
crypto isakmp keepalive 10 5 periodic
!
crypto ipsec security-association replay window-size 1024
!
crypto ipsec transform-set BTC_MRSK_ESP esp-aes esp-md5-hmac
--More-- mode tunnel
!
crypto ipsec profile BTCcisco20
set security-association lifetime seconds 43200
set transform-set BTC_MRSK_ESP
set pfs group14
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface Loopback1
ip address 10.100.100.1 255.255.255.255
zone-member security E_FW_INSIDE_ZONE
!
interface Tunnel0
ip address X.X.1.1 255.255.255.0
zone-member security E_FW_INSIDE_ZONE
ip ospf network point-to-point
ip ospf mtu-ignore
tunnel source X.X.90.1
tunnel destination X.X.X.X
tunnel protection ipsec profile BTCcisco20
!
interface Tunnel7
description BTC_Maersk_Seay_VPN_IPsec
ip address X.X.7.1 255.255.255.0
ip mtu 1436
zone-member security E_FW_INSIDE_ZONE
ip ospf network point-to-point
ip ospf dead-interval 40
ip ospf retransmit-interval 10
ip ospf transmit-delay 10
ip ospf mtu-ignore
keepalive 3600 3
tunnel source GigabitEthernet0/0/1
tunnel mode ipsec ipv4
tunnel destination X.X.22.34
tunnel protection ipsec profile BTCcisco20
!
interface Tunnel8
description BTC_Maersk_Pililaau_VPN_IPsec
ip address X.X.8.1 255.255.255.0
ip mtu 1436
zone-member security E_FW_INSIDE_ZONE
ip ospf network point-to-point
ip ospf dead-interval 40
ip ospf retransmit-interval 10
ip ospf transmit-delay 10
ip ospf mtu-ignore
keepalive 3600 3
tunnel source GigabitEthernet0/0/1
tunnel mode ipsec ipv4
--More-- tunnel destination X.X.20.22
tunnel protection ipsec profile BTCcisco20
!
interface GigabitEthernet0/0/0
description Management_Interface
no ip address
ip nbar protocol-discovery
zone-member security E_FW_INSIDE_ZONE
negotiation auto
!
interface GigabitEthernet0/0/1
description Orange_MPLS_10.10
ip address 10.10.2.4 255.255.255.240
ip nat inside
zone-member security E_FW_INSIDE_ZONE
negotiation auto
vrrp 10 description MPLS_VRRP_MASTER
vrrp 10 ip 10.10.2.2
vrrp 10 timers advertise msec 300
vrrp 10 preempt delay minimum 10
vrrp 10 priority 110
vrrp 10 track 99 decrement 20
ip virtual-reassembly
!
interface GigabitEthernet0/0/2
no ip address
zone-member security E_FW_OUTSIDE_ZONE
negotiation auto
ip virtual-reassembly
!
interface GigabitEthernet0/0/2.700
encapsulation dot1Q 700 native
ip address X.X.90.4 255.255.255.240
ip nat outside
zone-member security E_FW_OUTSIDE_ZONE
vrrp 15 description INTERNET_VRRP_MASTER
vrrp 15 ip X.X.90.1
vrrp 15 timers advertise msec 300
vrrp 15 preempt delay minimum 10
vrrp 15 priority 110
vrrp 15 track 99 decrement 20
ip virtual-reassembly
!
interface GigabitEthernet0
vrf forwarding Mgmt-intf
no ip address
shutdown
negotiation auto
!
interface Vlan1
no ip address
shutdown
!
router ospf 1881
network X.X.7.0 0.0.0.255 area 0
network X.X.8.0 0.0.0.255 area 0
network X.X.1.0 0.0.0.255 area 0
!
ip nat inside source static tcp X.X.20.114 443 X.X.90.18 443 extendable
ip nat inside source static tcp X.X.20.114 514 X.X.90.18 514 extendable
ip nat inside source static udp X.X.20.114 514 X.X.90.18 514 extendable
ip nat inside source static tcp X.X.20.118 443 X.X.90.19 443 extendable
--More-- ip nat inside source static tcp X.X.20.118 514 X.X.90.19 514 extendable
ip nat inside source static udp X.X.20.118 514 X.X.90.19 514 extendable
ip nat inside source static tcp X.X.20.122 443 X.X.90.20 443 extendable
ip nat inside source static tcp X.X.20.122 514 X.X.90.20 514 extendable
ip nat inside source static udp X.X.20.122 514 X.X.90.20 514 extendable
ip nat inside source static tcp X.X.20.126 443 X.X.90.21 443 extendable
ip nat inside source static tcp X.X.20.126 514 X.X.90.21 514 extendable
ip nat inside source static udp X.X.20.126 514 X.X.90.21 514 extendable
ip nat inside source static tcp X.X.22.66 554 X.X.90.22 554 extendable
ip nat inside source static tcp X.X.22.66 9200 X.X.90.22 9200 extendable
ip nat inside source static tcp X.X.22.66 9201 X.X.90.22 9201 extendable
ip nat inside source static tcp X.X.22.50 443 X.X.90.23 443 extendable
ip nat inside source static tcp X.X.22.50 514 X.X.90.23 514 extendable
ip nat inside source static udp X.X.22.50 514 X.X.90.23 514 extendable
ip nat inside source static tcp X.X.20.42 443 X.X.90.24 443 extendable
ip nat inside source static tcp X.X.20.42 514 X.X.90.24 514 extendable
ip nat inside source static udp X.X.20.42 514 X.X.90.24 514 extendable
ip nat inside source static tcp X.X.20.62 443 X.X.90.25 443 extendable
ip nat inside source static tcp X.X.20.62 514 X.X.90.25 514 extendable
ip nat inside source static udp X.X.20.62 514 X.X.90.25 514 extendable
ip nat inside source static tcp X.X.20.98 554 X.X.90.26 554 extendable
ip nat inside source static tcp X.X.20.98 9200 X.X.90.26 9200 extendable
ip nat inside source static tcp X.X.20.98 22609 X.X.90.26 22609 extendable
ip nat inside source static udp X.X.20.98 22609 X.X.90.26 22609 extendable
ip nat inside source static tcp X.X.20.74 554 X.X.90.27 554 extendable
ip nat inside source static tcp X.X.20.74 9200 X.X.90.27 9200 extendable
ip nat inside source static tcp X.X.20.74 22609 X.X.90.27 22609 extendable
ip nat inside source static udp X.X.20.74 22609 X.X.90.27 22609 extendable
ip nat inside source static tcp X.X.20.82 554 X.X.90.28 554 extendable
ip nat inside source static tcp X.X.20.82 9200 X.X.90.28 9200 extendable
ip nat inside source static tcp X.X.20.82 22609 X.X.90.28 22609 extendable
ip nat inside source static udp X.X.20.82 22609 X.X.90.28 22609 extendable
ip nat inside source static tcp X.X.22.78 22609 X.X.90.29 443 extendable
ip nat inside source static tcp X.X.22.78 554 X.X.90.29 554 extendable
ip nat inside source static tcp X.X.22.78 9200 X.X.90.29 9200 extendable
ip nat inside source static tcp X.X.22.78 22609 X.X.90.29 22609 extendable
ip nat inside source static udp X.X.22.78 22609 X.X.90.29 22609 extendable
ip nat inside source static tcp X.X.20.26 554 X.X.90.30 554 extendable
ip nat inside source static tcp X.X.20.26 9200 X.X.90.30 9200 extendable
ip nat inside source static tcp X.X.20.26 22609 X.X.90.30 22609 extendable
ip nat inside source static udp X.X.20.26 22609 X.X.90.30 22609 extendable
ip nat inside source static tcp X.X.21.206 443 X.X.90.31 443 extendable
ip nat inside source static tcp X.X.21.206 514 X.X.90.31 514 extendable
ip nat inside source static udp X.X.21.206 514 X.X.90.31 514 extendable
ip nat inside source static tcp X.X.20.158 443 X.X.90.32 443 extendable
ip nat inside source static tcp X.X.20.158 514 X.X.90.32 514 extendable
ip nat inside source static udp X.X.20.158 514 X.X.90.32 514 extendable
ip nat inside source static tcp X.X.20.58 443 X.X.90.33 443 extendable
ip nat inside source static tcp X.X.20.58 514 X.X.90.33 514 extendable
ip nat inside source static udp X.X.20.58 514 X.X.90.33 514 extendable
ip nat inside source static tcp X.X.21.102 554 X.X.90.34 554 extendable
ip nat inside source static tcp X.X.21.102 9200 X.X.90.34 9200 extendable
ip nat inside source static tcp X.X.21.102 22609 X.X.90.34 22609 extendable
ip nat inside source static udp X.X.21.102 22609 X.X.90.34 22609 extendable
ip nat inside source static tcp X.X.20.70 554 X.X.90.35 554 extendable
ip nat inside source static tcp X.X.20.70 9200 X.X.90.35 9200 extendable
ip nat inside source static tcp X.X.20.70 22609 X.X.90.35 22609 extendable
ip nat inside source static udp X.X.20.70 22609 X.X.90.35 22609 extendable
ip nat inside source static tcp X.X.20.142 554 X.X.90.36 554 extendable
ip nat inside source static tcp X.X.20.142 9200 X.X.90.36 9200 extendable
ip nat inside source static tcp X.X.20.142 22609 X.X.90.36 22609 extendable
ip nat inside source static udp X.X.20.142 22609 X.X.90.36 22609 extendable
--More-- ip nat inside source static tcp X.X.20.138 554 X.X.90.37 554 extendable
ip nat inside source static tcp X.X.20.138 9200 X.X.90.37 9200 extendable
ip nat inside source static tcp X.X.20.138 22609 X.X.90.37 22609 extendable
ip nat inside source static udp X.X.20.138 22609 X.X.90.37 22609 extendable
ip nat inside source static tcp X.X.20.90 554 X.X.90.38 554 extendable
ip nat inside source static tcp X.X.20.90 9200 X.X.90.38 9200 extendable
ip nat inside source static tcp X.X.20.90 22609 X.X.90.38 22609 extendable
ip nat inside source static udp X.X.20.90 22609 X.X.90.38 22609 extendable
ip nat inside source static tcp X.X.20.106 554 X.X.90.39 554 extendable
ip nat inside source static tcp X.X.20.106 9200 X.X.90.39 9200 extendable
ip nat inside source static tcp X.X.20.106 22609 X.X.90.39 22609 extendable
ip nat inside source static udp X.X.20.106 22609 X.X.90.39 22609 extendable
ip nat inside source static tcp X.X.20.110 554 X.X.90.40 554 extendable
ip nat inside source static tcp X.X.20.110 9200 X.X.90.40 9200 extendable
ip nat inside source static tcp X.X.20.110 22609 X.X.90.40 22609 extendable
ip nat inside source static udp X.X.20.110 22609 X.X.90.40 22609 extendable
ip nat inside source static tcp X.X.21.222 554 X.X.90.41 554 extendable
ip nat inside source static tcp X.X.21.222 9200 X.X.90.41 9200 extendable
ip nat inside source static tcp X.X.21.222 22609 X.X.90.41 22609 extendable
ip nat inside source static udp X.X.21.222 22609 X.X.90.41 22609 extendable
ip nat inside source static tcp X.X.20.102 554 X.X.90.42 554 extendable
ip nat inside source static tcp X.X.20.102 9200 X.X.90.42 9200 extendable
ip nat inside source static tcp X.X.20.102 22609 X.X.90.42 22609 extendable
ip nat inside source static udp X.X.20.102 22609 X.X.90.42 22609 extendable
ip nat inside source static tcp X.X.20.94 554 X.X.90.43 554 extendable
ip nat inside source static tcp X.X.20.94 9200 X.X.90.43 9200 extendable
ip nat inside source static tcp X.X.20.94 22609 X.X.90.43 22609 extendable
ip nat inside source static udp X.X.20.94 22609 X.X.90.43 22609 extendable
ip nat inside source static tcp X.X.20.86 554 X.X.90.44 554 extendable
ip nat inside source static tcp X.X.20.86 9200 X.X.90.44 9200 extendable
ip nat inside source static tcp X.X.20.86 22609 X.X.90.44 22609 extendable
ip nat inside source static udp X.X.20.86 22609 X.X.90.44 22609 extendable
ip nat inside source static tcp X.X.21.242 554 X.X.90.50 554 extendable
ip nat inside source static tcp X.X.21.242 9200 X.X.90.50 9200 extendable
ip nat inside source static tcp X.X.21.242 22609 X.X.90.50 22609 extendable
ip nat inside source static udp X.X.21.242 22609 X.X.90.50 22609 extendable
ip nat inside source static tcp X.X.22.26 1610 X.X.90.51 1610 extendable
ip nat inside source static udp X.X.22.26 1610 X.X.90.51 1610 extendable
ip nat inside source static tcp X.X.22.26 1611 X.X.90.51 1611 extendable
ip nat inside source static udp X.X.22.26 1611 X.X.90.51 1611 extendable
ip nat inside source static tcp X.X.22.22 1610 X.X.90.52 1610 extendable
ip nat inside source static udp X.X.22.22 1610 X.X.90.52 1610 extendable
ip nat inside source static tcp X.X.22.22 1611 X.X.90.52 1611 extendable
ip nat inside source static udp X.X.22.22 1611 X.X.90.52 1611 extendable
ip nat inside source static tcp X.X.22.58 1610 X.X.90.53 1610 extendable
ip nat inside source static udp X.X.22.58 1610 X.X.90.53 1610 extendable
ip nat inside source static tcp X.X.22.58 1611 X.X.90.53 1611 extendable
ip nat inside source static udp X.X.22.58 1611 X.X.90.53 1611 extendable
ip nat inside source static tcp X.X.22.18 1610 X.X.90.54 1610 extendable
ip nat inside source static udp X.X.22.18 1610 X.X.90.54 1610 extendable
ip nat inside source static tcp X.X.22.18 1611 X.X.90.54 1611 extendable
ip nat inside source static udp X.X.22.18 1611 X.X.90.54 1611 extendable
ip nat inside source static tcp X.X.22.54 1610 X.X.90.55 1610 extendable
ip nat inside source static udp X.X.22.54 1610 X.X.90.55 1610 extendable
ip nat inside source static tcp X.X.22.54 1611 X.X.90.55 1611 extendable
ip nat inside source static udp X.X.22.54 1611 X.X.90.55 1611 extendable
ip nat inside source static tcp X.X.20.78 554 X.X.90.56 554 extendable
ip nat inside source static tcp X.X.20.78 9200 X.X.90.56 9200 extendable
ip nat inside source static tcp X.X.20.78 22609 X.X.90.56 22609 extendable
ip nat inside source static udp X.X.20.78 22609 X.X.90.56 22609 extendable
ip nat inside source static tcp X.X.22.122 554 X.X.90.57 554 extendable
ip nat inside source static tcp X.X.22.122 9200 X.X.90.57 9200 extendable
--More-- ip nat inside source static tcp X.X.22.122 22609 X.X.90.57 22609 extendable
ip nat inside source static udp X.X.22.122 22609 X.X.90.57 22609 extendable
ip nat inside source static tcp X.X.22.126 554 X.X.90.58 554 extendable
ip nat inside source static tcp X.X.22.126 9200 X.X.90.58 9200 extendable
ip nat inside source static tcp X.X.22.126 22609 X.X.90.58 22609 extendable
ip nat inside source static udp X.X.22.126 22609 X.X.90.58 22609 extendable
ip nat inside source static tcp X.X.22.134 554 X.X.90.59 554 extendable
ip nat inside source static tcp X.X.22.134 9200 X.X.90.59 9200 extendable
ip nat inside source static tcp X.X.22.134 22609 X.X.90.59 22609 extendable
ip nat inside source static udp X.X.22.134 22609 X.X.90.59 22609 extendable
ip nat inside source static tcp X.X.22.98 443 X.X.90.60 443 extendable
ip nat inside source static tcp X.X.22.98 514 X.X.90.60 514 extendable
ip nat inside source static udp X.X.22.98 514 X.X.90.60 514 extendable
ip nat inside source static tcp X.X.22.130 554 X.X.90.61 554 extendable
ip nat inside source static tcp X.X.22.130 9200 X.X.90.61 9200 extendable
ip nat inside source static tcp X.X.22.130 22609 X.X.90.61 22609 extendable
ip nat inside source static udp X.X.22.130 22609 X.X.90.61 22609 extendable
ip nat inside source static tcp X.X.21.142 554 X.X.90.62 554 extendable
ip nat inside source static tcp X.X.21.142 9200 X.X.90.62 9200 extendable
ip nat inside source static tcp X.X.21.142 22609 X.X.90.62 22609 extendable
ip nat inside source static udp X.X.21.142 22609 X.X.90.62 22609 extendable
ip nat inside source static tcp X.X.21.142 37777 X.X.90.62 37777 extendable
ip nat inside source static tcp X.X.21.142 37778 X.X.90.62 37778 extendable
ip nat inside source static udp X.X.21.142 37778 X.X.90.62 37778 extendable
ip nat inside source list NAT_ACL interface GigabitEthernet0/0/2.700 overload
ip forward-protocol nd
no ip http server
no ip http secure-server
ip route 0.0.0.0 0.0.0.0 X.X.90.2
ip route 10.10.2.0 255.255.255.240 10.10.2.1
ip route 10.40.1.0 255.255.255.0 10.10.2.1
ip route 10.96.1.0 255.255.255.0 10.10.2.1
ip route X.X.90.16 255.255.255.240 10.10.2.1
ip route X.X.90.32 255.255.255.240 10.10.2.1
ip route X.X.90.48 255.255.255.240 10.10.2.1
ip route X.X.90.64 255.255.255.240 10.10.2.1
ip route X.X.20.0 255.255.255.0 10.10.2.1
ip route X.X.21.0 255.255.255.0 10.10.2.1
ip route X.X.22.0 255.255.255.0 10.10.2.1
ip ssh port 2222 rotary 1
ip ssh version 2
!
!
ip access-list extended E_FW_INSIDE_TO_OUTSIDE_ACL_01
permit ip X.X.20.0 0.0.0.255 any log
permit ip X.X.21.0 0.0.0.255 any
permit ip X.X.22.0 0.0.0.255 any
permit ip X.X.90.16 0.0.0.15 any
permit ip X.X.90.32 0.0.0.15 any
permit ip X.X.90.48 0.0.0.15 any
permit ip X.X.90.64 0.0.0.15 any
deny udp any any eq 10001 log
ip access-list extended E_FW_INSIDE_TO_SLF_ACL_02
permit tcp any eq 2222 any
permit tcp any eq 22609 any
permit udp host 10.10.2.2 any
permit udp host 10.10.2.4 any
permit ip host 10.40.1.250 any
permit icmp host 57.216.254.148 any
permit icmp host 57.216.254.145 any
permit icmp host 57.209.227.205 any
permit icmp host 57.209.227.206 any
--More-- permit icmp host 10.10.2.1 any
permit icmp X.X.20.0 0.0.0.255 any
permit icmp X.X.21.0 0.0.0.255 any
permit icmp X.X.22.0 0.0.0.255 any
permit udp X.X.20.0 0.0.0.255 any
permit udp X.X.21.0 0.0.0.255 any
permit udp X.X.22.0 0.0.0.255 any
permit udp X.X.1.0 0.0.0.255 any
permit tcp X.X.1.0 0.0.0.255 any
permit ospf host X.X.8.2 host X.X.8.1
permit icmp host X.X.8.2 host X.X.8.1
permit icmp host X.X.8.2 10.10.7.0 0.0.0.255
permit udp X.X.8.0 0.0.0.255 any
permit esp host X.X.20.22 host 10.10.2.2
permit icmp X.X.90.16 0.0.0.15 any
permit icmp X.X.90.32 0.0.0.15 any
permit icmp X.X.90.48 0.0.0.15 any
permit icmp X.X.90.64 0.0.0.15 any
permit udp X.X.90.16 0.0.0.15 any
permit udp X.X.90.32 0.0.0.15 any
permit udp X.X.90.48 0.0.0.15 any
permit udp X.X.90.64 0.0.0.15 any
permit ip host 10.10.2.1 any
permit ospf host X.X.7.2 host X.X.7.1
permit icmp host X.X.7.2 host X.X.7.1
permit icmp host X.X.7.2 10.10.7.0 0.0.0.255
permit udp X.X.7.0 0.0.0.255 any
permit esp host X.X.22.34 host 10.10.2.2
permit icmp host X.X.1.2 host X.X.1.1
permit icmp 10.10.5.0 0.0.0.255 any
ip access-list extended E_FW_OUTSIDE_TO_INSIDE_ACL_03
permit tcp any eq 5060 any
permit udp any eq 5060 any
permit udp any range 1000 1100 any
permit tcp any eq 465 any
permit icmp host X.X.90.2 any
permit ip host 206.16.60.70 X.X.20.0 0.0.0.255
permit ip host 206.16.60.70 X.X.21.0 0.0.0.255
permit ip host 206.16.60.70 X.X.22.0 0.0.0.255
permit tcp host 54.84.182.84 X.X.20.0 0.0.0.255
permit tcp host 54.84.182.84 X.X.21.0 0.0.0.255
permit tcp host 54.84.182.84 X.X.22.0 0.0.0.255
permit icmp host 72.198.133.5 any
permit ip host 70.186.254.52 any
permit ip host 50.58.27.183 any
permit tcp host 72.215.150.212 X.X.22.0 0.0.0.255
permit icmp host 72.215.150.212 any
permit ip host 72.215.150.212 X.X.22.0 0.0.0.255
permit udp any range 10002 20000 any
permit ip host 12.109.9.58 X.X.21.0 0.0.0.255
permit ip host 209.163.240.162 X.X.21.0 0.0.0.255
permit ip host 166.166.130.13 X.X.21.0 0.0.0.255
permit ip host 98.198.144.47 X.X.21.0 0.0.0.255
permit ip host 12.35.94.3 X.X.21.0 0.0.0.255
permit tcp host 12.109.9.58 X.X.21.0 0.0.0.255
permit tcp host 209.163.240.162 X.X.21.0 0.0.0.255
permit tcp host 166.166.130.13 X.X.21.0 0.0.0.255
permit tcp host 98.198.144.47 X.X.21.0 0.0.0.255
permit tcp host 12.35.94.3 X.X.21.0 0.0.0.255
permit udp host 12.109.9.58 X.X.21.0 0.0.0.255 eq 37778
permit udp host 209.163.240.162 X.X.21.0 0.0.0.255 eq 37778
permit udp host 166.166.130.13 X.X.21.0 0.0.0.255 eq 37778
--More-- permit udp host 98.198.144.47 X.X.21.0 0.0.0.255 eq 37778
permit udp host 12.35.94.3 X.X.21.0 0.0.0.255 eq 37778
permit tcp any range 37777 37778 any
permit tcp host 12.109.9.58 X.X.21.0 0.0.0.255 eq www
permit tcp host 209.163.240.162 X.X.21.0 0.0.0.255 eq www
permit tcp host 166.166.130.13 X.X.21.0 0.0.0.255 eq www
permit tcp host 98.198.144.47 X.X.21.0 0.0.0.255 eq www
permit tcp host 12.35.94.3 X.X.21.0 0.0.0.255 eq www
ip access-list extended E_FW_OUTSIDE_TO_SLF_ACL_04
permit ip host 70.186.254.52 any
permit udp host 98.188.216.148 any
permit udp host X.X.X.X eq isakmp any
permit udp host 50.58.27.183 eq 5060 any
permit tcp host 98.188.216.149 eq 8880 any
permit tcp host 72.198.133.5 eq 8880 any
permit tcp host 206.16.60.70 any
permit ip host X.X.X.X any log
permit icmp 70.188.92.0 0.0.0.255 any
deny ip X.X.20.0 0.0.0.255 any
deny ip X.X.21.0 0.0.0.255 any
deny ip X.X.22.0 0.0.0.255 any
deny ip X.X.90.16 0.0.0.15 any
deny ip X.X.90.32 0.0.0.15 any
deny ip X.X.90.48 0.0.0.15 any
deny ip X.X.90.64 0.0.0.15 any
deny ip 10.96.1.0 0.0.0.255 any
deny ip 10.0.0.0 0.255.255.255 any
deny ip 192.168.0.0 0.0.255.255 any
deny ip 224.0.0.0 31.255.255.255 any
deny ip 127.0.0.0 0.255.255.255 any
deny ip 169.254.0.0 0.0.255.255 any
deny ip 77.0.0.0 0.255.255.255 any
permit ip host X.X.90.3 any
permit ip host X.X.90.2 any
deny ip X.X.0.0 0.15.255.255 any
ip access-list extended E_FW_SLF_TO_INSIDE_ACL_05
permit tcp any eq 2222 any
permit ip host 10.10.2.2 any
permit ip host 10.10.2.4 any
permit icmp host X.X.8.1 10.10.4.0 0.0.0.255
permit ip host 10.10.2.2 host X.X.20.22
permit ip host X.X.90.1 any
permit ip host X.X.90.4 any
permit ip host X.X.1.1 host X.X.1.2
permit icmp host X.X.7.1 10.10.5.0 0.0.0.255
ip access-list extended E_FW_SLF_TO_OUTSIDE_ACL_06
permit tcp any eq 2222 any
permit udp any eq snmp any
permit ip host X.X.90.1 any
permit ip host X.X.90.4 any
permit icmp host 10.10.2.2 host 50.58.27.183
permit icmp host 10.10.2.2 host 54.84.182.84
permit icmp host 10.10.2.2 host 70.186.254.52
permit icmp host 10.10.2.4 host 50.58.27.183
permit icmp host 10.10.2.4 host 54.84.182.84
permit icmp host 10.10.2.4 host 70.186.254.52
permit icmp host 10.10.2.4 host 72.215.150.212
deny udp any any eq 10001
ip access-list extended NAT_ACL
permit ip X.X.90.16 0.0.0.15 any
permit ip X.X.90.32 0.0.0.15 any
permit ip X.X.90.48 0.0.0.15 any
--More-- permit ip X.X.90.64 0.0.0.15 any
permit ip X.X.20.0 0.0.0.255 any
permit ip X.X.21.0 0.0.0.255 any
permit ip X.X.22.0 0.0.0.255 any
!
ip sla 20
icmp-echo 10.10.2.1
ip sla schedule 20 life forever start-time now
ip sla 25
icmp-echo X.X.90.2
ip sla schedule 25 life forever start-time now
logging history alerts
logging source-interface GigabitEthernet0/0/2.700
access-list 199 deny tcp any any eq telnet
access-list 199 deny tcp any any eq www log
access-list 199 deny tcp any any eq 22
access-list 199 permit ip any any
access-list 199 remark -- ACL restricting 22/23, redirect to ssh port 2222
!
snmp-server community !BTC RO
snmp-server community BTC117 RW
snmp-server enable traps snmp authentication linkdown linkup coldstart warmstart
snmp-server enable traps vrrp
snmp-server enable traps call-home message-send-fail server-fail
snmp-server enable traps tty
snmp-server enable traps ospf state-change
snmp-server enable traps ospf errors
snmp-server enable traps ospf retransmit
snmp-server enable traps ospf lsa
snmp-server enable traps ospf cisco-specific state-change nssa-trans-change
snmp-server enable traps ospf cisco-specific state-change shamlink interface
snmp-server enable traps ospf cisco-specific state-change shamlink neighbor
snmp-server enable traps ospf cisco-specific errors
snmp-server enable traps ospf cisco-specific retransmit
snmp-server enable traps ospf cisco-specific lsa
snmp-server enable traps config-copy
snmp-server enable traps config
snmp-server enable traps config-ctid
snmp-server enable traps fru-ctrl
snmp-server enable traps entity
snmp-server enable traps event-manager
snmp-server enable traps ipmulticast
snmp-server enable traps mvpn
snmp-server enable traps trustsec-sxp conn-srcaddr-err msg-parse-err conn-config-err binding-err conn-up conn-down binding-expn-fail oper-nodeid-change binding-conflict
snmp-server enable traps c3g
snmp-server enable traps bulkstat collection transfer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2019 02:56 PM
Try just "show policy-firewall stats zone-pair" this should display the output for all zone-pairs, please upload the output for review.
You should edit the configuration above, to remove your passwords - level 7 passwords are easily cracked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2019 07:12 AM
Hi,
The command didn't work at all.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2019 07:15 AM
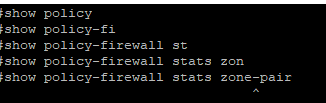
What license do you have?
Perhaps the command has change on your version, please show me the output of:-
show policy-firewall stats ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2019 09:13 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2019 09:22 AM
Perhaps it's this command on your version:- show policy-map type inspect zone-pair
From there you should be able to determine matches against your class-maps
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2019 09:53 AM
Perfect that worked, I can see all the matches against my class-maps.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 12:51 PM
Hi, @Rob Ingram
we were thinking to get rid of this IOS XE and replace it with a new Cisco IOS Router what would be the best replacement? considering the 4331 specifications and configuration?
Thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 02:03 PM
Do you require additional features? Perhaps a firewall might be more appropriate.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: