- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: My Auto NAT is not showing up as auto
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
My Auto NAT is not showing up as auto
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2019 01:00 PM - edited 02-21-2020 09:35 AM
object network VPN_NET subnet 192.168.10.0 255.255.255.0 object-group network LAN network-object 175.2.100.0 255.255.255.0 network-object 175.3.100.0 255.255.255.0 Auto NAT(or PAT) NAT (INSIDE,OUTSIDE) source dynamic LAN interface Twice NAT or Identity NAT NAT (INSIDE,OUTSIDE) source static LAN LAN destination static VPN_NET VPN_NET
1st question)
LAN object is my local lan on ASA inside interface, they are trying to have access both to the internet and ANYconnect clients on VPN_NET.
Because I used the object group I can't put my NAT command under that object to be shown up as AUTO NAT.
So right now I have to statically manage the order of operations, I don't like that
see the output of show
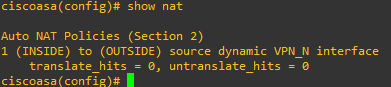
ciscoasa# show nat
Manual NAT Policies (Section 1)
1 (INSIDE) to (OUTSIDE) source static LAN LAN destination static VPN_NET VPN_NET
translate_hits = 33, untranslate_hits = 33
2 (INSIDE) to (OUTSIDE) source dynamic LAN interface
translate_hits = 89, untranslate_hits = 36
ciscoasa#
2nd Question)
as you can see I used twice nat for my SSL VPN, Should I use NAT exempt or Twice Nat? I used Twice nat and it worked(I was able to bypass the traffic through the tunnel.
3rd Question) in the same scenario
there is a l3 switch down the line that is connected to inside of my ASA, who provides those object LAN networks, so it has a 0.0.0/0 route to ASA, we want to limit the internet traffic that is coming from that l3 switch only to those subnets under object LAN, and right now because I am just natting object LAN traffic to the internet, they are limited already, but I think it's not efficient in a way, that unwanted traffic is being traveled through that link to ASA and not being Natted and probably go to the internet, and discarded down the road(I am not even sure where it's being discarded and that's an another question onto itself),
so what is the best practice in this circumstance? should I put an ACL on the L3 switch? another question I have is L3 switches first analyze access lists and then analyze routing options?(which one comes first)
fyi: my ASA also has a 0.0.0/0 route to the outside(internet).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2019 03:01 PM
1st question)
I didnt see a question here. I am not sure I understand what you mean when you say "Because I used the object group I can't put my NAT command under that object to be shown up as AUTO NAT." Do you already have a NAT statement created for it or you are using it in an ACL or somewhere else? You should still be able to configure NAT for it even though it is used somewhere else. But if you are worried it will mess something up, you could always create another object group matching the same subnets and create an auto NAT for that instead.
2nd Question)
NAT exempt is the old method for exempting traffic from being NATed. The term is still used as old habits die hard. Twice NAT is the correct method to use for exempting traffic from being NATed now.
3rd Question)
Best practice would be to apply access list as close to the source of the traffic as possible. However, this isn't always an easy or scalable thing to do as there could be tens or hundreds of switches involved. Also, it is a good practice to let switches do switching and firewalls do traffic filtering. I would suggest putting specific ACLs on the ASA to only allow the traffic you want to pass through the ASA.
another question I have is L3 switches first analyze access lists and then analyze routing options?(which one comes first)
Access list is checked first, then routing
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2019 04:53 PM - edited 10-14-2019 06:14 AM
1st question)
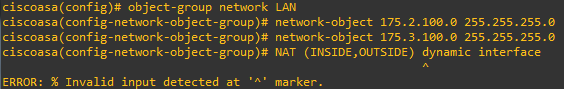
No!!, I don't have a nat statement created nor an ACL,
again because I am using object-group instead of object, syntax won't go through and give me an error, and It basically asks me to put the source keyword again.
So the nat command can't be nested under object-group network lan, and I don't even care but the outcome is different, this one does not give you an auto nat.
and in case you are wondering what auto-nat is,
and it's always automatically placed after manual nat
3rd question)
can I ask what will happen to a packet that's being routed because of 0.0.0.0/0 to the next router, and in the next router there is another 0.0.0.0/0 on the routing table to the outside interface, and there is no nat statement for that specific packet.
what will happen to that packet?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2019 11:42 AM
1st question)
in this case use place the NAT statement in after-auto manual NAT that way it will be matched after manual NAT (section 1) and auto NAT (section 2). Also, FYI, I know very well what auto NAT is.
3rd question)
If the next hop router is has a public IP, the packet will just be dropped on the ASA as the private IP range is not routable out on the internet. If the next hop router has a private IP, it will route the traffic back to the ASA and the ASA will drop it as the packet will not match any existing connection.
Please remember to select a correct answer and rate helpful posts
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: