- Cisco Community
- Technology and Support
- Security
- Network Security
- NAT issue in ASA 5510
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2012 04:43 AM - edited 03-11-2019 05:07 PM
HI experts,
i am using
Cisco Adaptive Security Appliance Software Version 8.0(4)
Device Manager Version 6.4(9)
i configure Nat but when i use packet tracer in firewall to see packet flow i found my inside packet is not able to reach to outside interface.what is the problem i don't understand. should i create access rule for the or anything else.
please healpe..
regards
Suhas
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2012 05:11 AM
Hi,
Could you provide the packet-tracer output either in the command line (CLI) format or as a screen capture if you are using ASDM
Can't really say anything since you havent provided any configurations you have or information about what connection you are testing.
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2012 03:07 AM
Hi,
I don't see anything in the configuration that would now prevent you from taking connections from inside to outside. To my understanding the problem you had was related to PING/ICMP not going through and its now working.
Seems you havent made any separate access-lists to your interfaces on the ASA so the "security-level" determines where your hosts can connect through the firewall.
And since you only have 2 interface with other inside having a value of 100 and outside a value of 0 it means that hosts behind inside interface can initiate connections to hosts behind outside interface. Hosts behind outside interface however cant connect to inside. (Natually since you dont have any Static NAT or NAT0 configuration they wouldnt be able to connect anyway)
If there is something that aint working, please clarify what is not working.
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2012 05:11 AM
Hi,
Could you provide the packet-tracer output either in the command line (CLI) format or as a screen capture if you are using ASDM
Can't really say anything since you havent provided any configurations you have or information about what connection you are testing.
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2012 07:24 AM
Hi Jouniforss,
Thank you for reply. right now i am give yoy limited configuration which i had configured on firewall. that include only interface & nat configuration.
interface Ethernet0/0
nameif outside
security-level 0
ip address 172.16.30.2 255.255.255.0
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 192.168.68.1 255.255.255.0
!
nat (inside) 1 192.168.1.0 255.255.255.0
suhas
global (outside) 1 interface interface Ethernet0/0- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2012 10:37 PM
Hi,
Pease find the whole configuration & packet tracer screen shot..
ASA Version 8.0(4)
!
hostname ciscoasa
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
name 172.16.30.0 outside
!
interface Ethernet0/0
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Ethernet0/1
nameif outside
security-level 0
ip address 172.16.30.2 255.255.255.0
!
interface Ethernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
nameif management
security-level 0
ip address 10.10.10.1 255.255.255.0
!
boot system disk0:/
boot system disk0:/asa825-33-k8.bin
ftp mode passive
pager lines 24
logging enable
logging asdm informational
mtu inside 1500
mtu outside 1500
mtu management 1500
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-649-103.bin
no asdm history enable
arp timeout 14400
nat-control
global (outside) 1 interface
nat (inside) 1 192.168.1.0 255.255.255.0
route outside 0.0.0.0 0.0.0.0 172.16.30.1 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 192.168.1.10 255.255.255.255 inside
http 10.10.10.2 255.255.255.255 management
no snmp-server location
no snmp-server contact
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
telnet 192.168.1.10 255.255.255.255 inside
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
username cisco password 3USUcOPFUiMCO4Jk encrypted
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
message-length maximum client auto
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:0fbad53e0533429878e448f1f87415fc
: end
ciscoasa(config)#
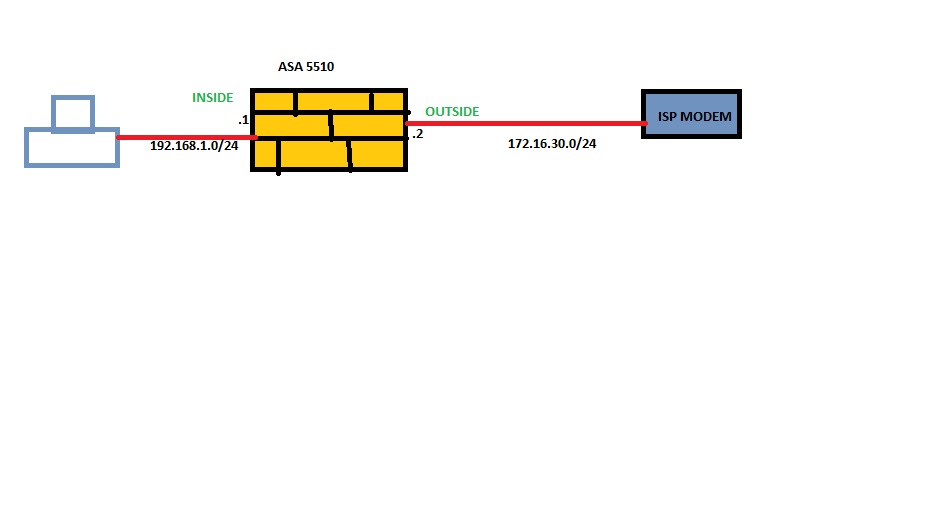
This image for INSIDE HOST TO INSIDE INTERFACE

This image for INSIDE HOST TO OUTSIDE INTERFACE

This image for INSIDE HOST TO OUTSIDE NEXT HOP INTERFACE

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2012 11:24 PM
Hi,
Couple of things.
If you are trying to PING/ICMP from the LAN network to the outside interface IP address of the ASA I think the ASA always blocks that. More specifically it should block PING/ICMP from a network behind ASA to interface IP address which isnt "owned" by the source network.
I'm not exactly sure why it would say in the last picture that after the NAT rule the packet is dropped
I do however notice that you have not added "inspect icmp" in your configuration.
Can you add this configuration to the ASA and try PING/ICMP through the ASA again
policy-map global_policy
class inspection_default
inspect icmp
You can do this from the CLI or if you use the ASDM you can choose the Tools drop down menu in the ASDM window and choose Command Line Interface which opens the below window

Choose the multiple line option and copy/paste the configuration I mentioned in the text field and send the command.
The "inspect icmp" setting can also be found through the ASDM but without checking it on ASDM I can't remember exactly where it was located.
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2012 02:57 AM
Hi Jouni,
It is done.Now i can pin my inside host to outside next hop interface i have exicute that command which you have given to me. it there any configuration should be done or it is ok..
Regards
Suhas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2012 03:07 AM
Hi,
I don't see anything in the configuration that would now prevent you from taking connections from inside to outside. To my understanding the problem you had was related to PING/ICMP not going through and its now working.
Seems you havent made any separate access-lists to your interfaces on the ASA so the "security-level" determines where your hosts can connect through the firewall.
And since you only have 2 interface with other inside having a value of 100 and outside a value of 0 it means that hosts behind inside interface can initiate connections to hosts behind outside interface. Hosts behind outside interface however cant connect to inside. (Natually since you dont have any Static NAT or NAT0 configuration they wouldnt be able to connect anyway)
If there is something that aint working, please clarify what is not working.
- Jouni
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


