- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: [PROBLEM]: VPN S2S/L2L between 2 ASA 5506-X
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2018 11:26 PM - edited 02-21-2020 07:27 AM
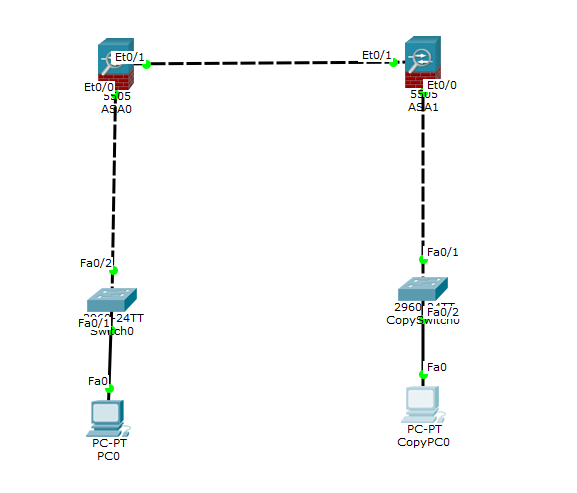
Hello everyone, I have a problem to create a VPN L2L between 2 ASA 5506-X (see the pictures bellow).
I configure my 2 firewall inspired by the majority of tutorials found on the NET.
I correctly place client PCs in each LAN, but when I try to ping from Site 1 to Site 2 (or vice versa) it does not work.
You can see below my firewall configuration and the network map.
Network map:
ASA0:
ASA Version 9.6(1) ! hostname FW2 enable password 8Ry2YjIyt7RRXU24 encrypted names ! interface GigabitEthernet1/1 shutdown no nameif no security-level no ip address ! interface GigabitEthernet1/2 shutdown no nameif no security-level no ip address ! interface GigabitEthernet1/3 shutdown no nameif no security-level no ip address ! interface GigabitEthernet1/4 shutdown no nameif no security-level no ip address ! interface GigabitEthernet1/5 shutdown no nameif no security-level no ip address ! interface GigabitEthernet1/6 nameif inside security-level 100 ip address 172.22.7.1 255.255.255.0 ! interface GigabitEthernet1/7 nameif DMZ security-level 50 ip address 172.22.8.1 255.255.255.0 ! interface GigabitEthernet1/8 nameif WAN security-level 0 ip address 172.30.1.20 255.255.255.0 ! interface Management1/1 management-only no nameif no security-level no ip address ! ftp mode passive object network obj_any subnet 0.0.0.0 0.0.0.0 object network LAN-inside subnet 172.22.7.0 255.255.255.0 object network LAN-remote subnet 172.21.7.0 255.255.255.0 access-list 1 extended permit ip 172.22.7.0 255.255.255.0 172.21.7.0 255.255.255.0 pager lines 24 logging asdm informational mtu inside 1500 mtu DMZ 1500 mtu WAN 1500 icmp unreachable rate-limit 1 burst-size 1 no asdm history enable arp timeout 14400 no arp permit-nonconnected nat (inside,WAN) source dynamic any interface nat (inside,WAN) source static LAN-inside LAN-inside destination static LAN-remote LAN-remote no-proxy-arp route-lookup router ospf 1 network 172.22.7.0 255.255.255.0 area 2 network 172.22.8.0 255.255.255.0 area 2 network 172.30.1.0 255.255.255.0 area 0 log-adj-changes ! route WAN 0.0.0.0 0.0.0.0 172.30.1.1 1 timeout xlate 3:00:00 timeout pat-xlate 0:00:30 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute timeout tcp-proxy-reassembly 0:01:00 timeout floating-conn 0:00:00 user-identity default-domain LOCAL aaa authentication ssh console LOCAL http server enable no snmp-server location no snmp-server contact service sw-reset-button crypto ipsec ikev1 transform-set ipsec-vpn esp-aes esp-sha-hmac crypto ipsec security-association pmtu-aging infinite crypto map Vevey 10 match address 1 crypto map Vevey 10 set peer 172.30.1.10 crypto map Vevey 10 set ikev1 transform-set ipsec-vpn crypto map Vevey interface inside crypto ca trustpool policy crypto ikev1 enable inside crypto ikev1 policy 2 authentication pre-share encryption aes hash sha group 2 lifetime 86400 telnet timeout 5 no ssh stricthostkeycheck ssh 172.0.0.0 255.255.255.0 inside ssh timeout 5 ssh version 2 ssh key-exchange group dh-group1-sha1 console timeout 0 dhcpd auto_config inside ! ntp server 172.30.1.1 dynamic-access-policy-record DfltAccessPolicy username admin password f3UhLvUj1QsXsuK7 encrypted privilege 15 tunnel-group 172.30.1.10 type ipsec-l2l tunnel-group 172.30.1.10 ipsec-attributes ikev1 pre-shared-key ***** ! class-map inspection_default match default-inspection-traffic ! ! policy-map type inspect dns preset_dns_map parameters message-length maximum client auto message-length maximum 512 policy-map global_policy class inspection_default inspect dns preset_dns_map inspect ftp inspect h323 h225 inspect h323 ras inspect rsh inspect rtsp inspect esmtp inspect sqlnet inspect skinny inspect sunrpc inspect xdmcp inspect sip inspect netbios inspect tftp inspect ip-options inspect icmp ! service-policy global_policy global prompt hostname context call-home reporting anonymous prompt 2 Cryptochecksum:ec1455b1dc514a6b64959311a95494c8 : end
ASA1:
ASA Version 9.6(1) ! hostname FW1 enable password 8Ry2YjIyt7RRXU24 encrypted names ! interface GigabitEthernet1/1 shutdown no nameif no security-level no ip address ! interface GigabitEthernet1/2 shutdown no nameif no security-level no ip address ! interface GigabitEthernet1/3 shutdown no nameif no security-level no ip address ! interface GigabitEthernet1/4 shutdown no nameif no security-level no ip address ! interface GigabitEthernet1/5 shutdown no nameif no security-level no ip address ! interface GigabitEthernet1/6 nameif inside security-level 100 ip address 172.21.7.1 255.255.255.0 ! interface GigabitEthernet1/7 nameif DMZ security-level 50 ip address 172.21.8.1 255.255.255.0 ! interface GigabitEthernet1/8 nameif WAN security-level 0 ip address 172.30.1.10 255.255.255.0 ! interface Management1/1 management-only no nameif no security-level no ip address ! ftp mode passive object network obj_any subnet 0.0.0.0 0.0.0.0 object network LAN-inside subnet 172.21.7.0 255.255.255.0 object network LAN-remote subnet 172.22.7.0 255.255.255.0 access-list 1 extended permit ip 172.21.7.0 255.255.255.0 172.22.7.0 255.255.255.0 pager lines 24 logging asdm informational mtu inside 1500 mtu DMZ 1500 mtu WAN 1500 icmp unreachable rate-limit 1 burst-size 1 no asdm history enable arp timeout 14400 no arp permit-nonconnected nat (inside,WAN) source static LAN-inside LAN-inside destination static LAN-remote LAN-remote no-proxy-arp route-lookup router ospf 1 network 172.21.7.0 255.255.255.0 area 1 network 172.21.8.0 255.255.255.0 area 1 network 172.30.1.0 255.255.255.0 area 0 log-adj-changes ! route WAN 0.0.0.0 0.0.0.0 172.30.1.1 1 timeout xlate 3:00:00 timeout pat-xlate 0:00:30 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute timeout tcp-proxy-reassembly 0:01:00 timeout floating-conn 0:00:00 user-identity default-domain LOCAL aaa authentication ssh console LOCAL http server enable no snmp-server location no snmp-server contact service sw-reset-button crypto ipsec ikev1 transform-set ipsec-vpn esp-aes esp-sha-hmac crypto ipsec security-association pmtu-aging infinite crypto map Lausanne 10 match address 1 crypto map Lausanne 10 set peer 172.30.1.20 crypto map Lausanne 10 set ikev1 transform-set ipsec-vpn crypto map Lausanne interface inside crypto ca trustpool policy crypto ikev1 enable inside crypto ikev1 policy 2 authentication pre-share encryption aes hash sha group 2 lifetime 86400 telnet timeout 5 no ssh stricthostkeycheck ssh 172.0.0.0 255.255.255.0 inside ssh timeout 5 ssh version 2 ssh key-exchange group dh-group1-sha1 console timeout 0 dhcpd auto_config inside ! ntp server 172.30.1.1 dynamic-access-policy-record DfltAccessPolicy username admin password f3UhLvUj1QsXsuK7 encrypted privilege 15 tunnel-group 172.30.1.30 type ipsec-l2l tunnel-group 172.30.1.30 ipsec-attributes ikev1 pre-shared-key ***** ! class-map inspection_default match default-inspection-traffic ! ! policy-map type inspect dns preset_dns_map parameters message-length maximum client auto message-length maximum 512 policy-map global_policy class inspection_default inspect dns preset_dns_map inspect ftp inspect h323 h225 inspect h323 ras inspect rsh inspect rtsp inspect esmtp inspect sqlnet inspect skinny inspect sunrpc inspect xdmcp inspect sip inspect netbios inspect tftp inspect ip-options inspect icmp ! service-policy global_policy global prompt hostname context call-home reporting anonymous prompt 2 Cryptochecksum:47c8cbbb9a05fbeae874207339690a65 : end
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2018 11:32 PM - edited 03-04-2018 11:23 PM
Then IP SLA is another way.
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2018 01:32 AM
Hi,
Can you share the some outputs:
1. debug crypto isakmp 127
2. sho crypto ipsec sa
3. debug crypto isakmp
4. sho route
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2018 02:09 AM
ASA 0
FW2# debug crypto isakmp 127
FW2# sh crypto ipsec sa
There are no ipsec sas
FW2# debug crypto isakmp
FW2# sh route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
Gateway of last resort is 172.30.1.1 to network 0.0.0.0
S* 0.0.0.0 0.0.0.0 [1/0] via 172.30.1.1, WAN
C 172.22.7.0 255.255.255.0 is directly connected, inside
L 172.22.7.1 255.255.255.255 is directly connected, inside
C 172.30.1.0 255.255.255.0 is directly connected, WAN
L 172.30.1.20 255.255.255.255 is directly connected, WAN
FW2#
ASA 1
FW1# debug crypto isakmp 127
FW1# sh crypto ipsec sa
There are no ipsec sas
FW1# debug crypto isakmp
FW1# sh route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
Gateway of last resort is 172.30.1.1 to network 0.0.0.0
S* 0.0.0.0 0.0.0.0 [1/0] via 172.30.1.1, WAN
O IA 172.22.7.0 255.255.255.0 [110/20] via 172.30.1.20, 00:12:41, WAN
C 172.30.1.0 255.255.255.0 is directly connected, WAN
L 172.30.1.10 255.255.255.255 is directly connected, WAN
FW1#
Thank you very much.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2018 03:32 AM
Hi,
You made some issues in routing side:
1. Why LAN subnet from both ASA are in routing configuration
router ospf 1network 172.21.7.0 255.255.255.0 area 1network 172.21.8.0 255.255.255.0 area 1network 172.30.1.0 255.255.255.0 area 0
router ospf 1network 172.22.7.0 255.255.255.0 area 2network 172.22.8.0 255.255.255.0 area 2network 172.30.1.0 255.255.255.0 area 0
Remove the local LAN subnets from OSPF routing and DMZ if not required.
Here I can see that you have default route toward wan and OSPF. You can keep only one.
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2018 04:01 AM
Thank you.
I can not delete them because if I do, my PC
from site 1 can not even ping the FW from site 2 (and vice versa).
What can I do to make the VPN work?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2018 04:55 AM
for configuration the VPN we need only WAN must be reachable not a lan site. Right now your traffic is not going through VPN tunnel and routing is pushing him out.
You must generate the traffic for VPN. otherwise, it will not come up.
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2018 05:20 AM - edited 03-01-2018 10:57 PM
Thanks.
But what can I use to generate the traffic for the VPN if ping doesn't work?
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2018 11:32 PM - edited 03-04-2018 11:23 PM
Then IP SLA is another way.
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: