- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Secure connection Firewall to Firewall accross LAN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Secure connection Firewall to Firewall accross LAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2019 01:23 AM - edited 02-21-2020 08:44 AM
Hi All
This maybe a bit of a strange request but I'm looking for the best way to create a link from one internal firewall to another internal firewall to pass specific traffic (Only ports and protocol for Mail). The only other traffic we have at present flows through virtual appliances, thus comes in on one VLAN/vSwitch/NIC onto the vAppliance (for example an RODC) then exits via a different NIC/vSwitch/VLAN onto the second firewall. We do NOT have any direct connections or pass-through links from firewall to firewall. In the past we have done the same thing using a mail relay but I think that was only to pass email alerts outbound.
I's there a secure way to connect the two firewalls together such as a VPN tunnel or is this simply a waist of time? I'm trying to avoid the two firewalls being connected together using the same VLAN.
Any help would be much appreciated indeed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2019 03:16 AM
And you would like to create a secured channel between two separated network domains without connecting them directly. For example, building a VPN tunnel between the separated network domains over server? I think there is no such solution..
And I think the current topology is designed by purpose to separate both firewalls. (e.g. make iDMZ is not routable to eDMZ)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2019 03:28 AM
Yes that is correct, in the past we have added a separate VLAN to connect Firewall to Firewall (physical CAT6 Cable) and passed traffic via static route but it's go's against out security policy. I was asking the question to see if a VPN from Firewall to Firewall would give me any more security features If I have to go down this route again?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2019 06:45 AM - edited 02-04-2019 06:47 AM
Hi,
You have to review your security policy to see why was it violated. Is it because of the traffic no encrypted? (I believe not.)
Or is it because of your action has make the one of the security zone on Firewall A routable to another security zone on Firewall B?
If so, I think VPN tunnel would not help in this case.
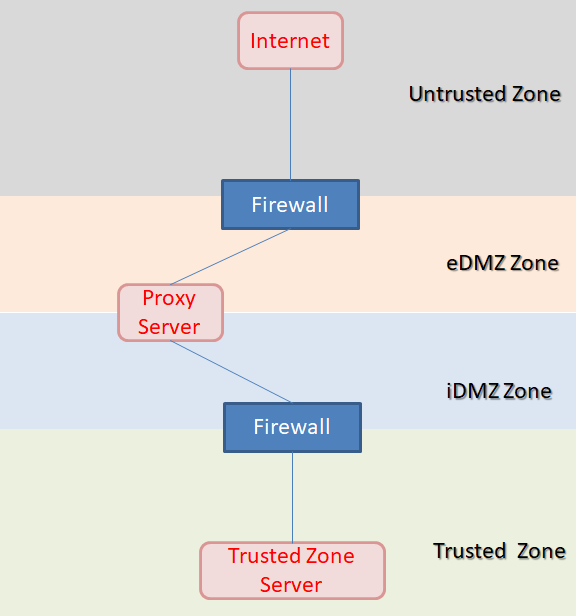
For example, the diagram as shown in below. If you created a 'link' between firewalls (no matter it is encrypted / un-encrypted), your action would cause the Trusted Zone accessible to Untrusted Zone (which bypassing the proxy server). That would be considered as security violation for some company.
If you must go ahead to build the connection between the firewalls. What you should do is to strictly limit the traffic from Trusted Zone --> eDMZ Zone / Untrusted Zone. Strictly
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide