- Cisco Community
- Technology and Support
- Security
- Network Security
- Solved: VPN S2S/L2L between 2 ASA 5505 Packet tracer
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2018 01:39 AM - edited 02-21-2020 07:21 AM
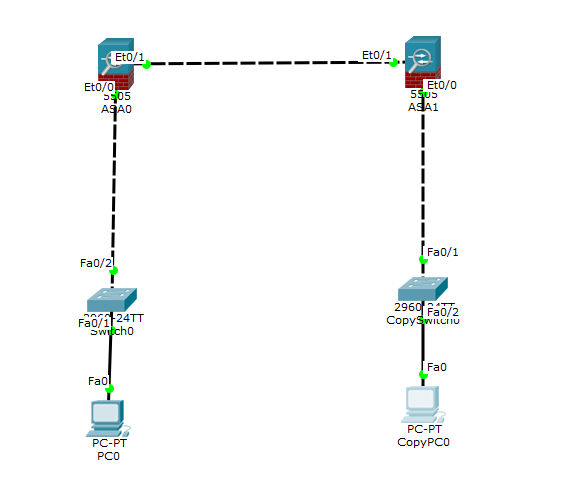
Hello, I'm new in the community of packet tracer.
I am trying to create a VPN between 2 Cisco ASA 5505 (Site to site) via packet tracer.
I would like my PC from my Site 1 (192.168.1.1) to ping my 2nd PC from my Site 2 (192.168.2.1)
Unfortunately if I send a ping from my PC 1 (192.168.1.1) the ASA 5505 site 2 (10.10.10.2) blocks my package
I tried to follow different tutorial found on the net but none gives a positive result.
regards.
ASA0 configuration
ASA Version 8.4(2) ! hostname ASAVevey names ! interface Ethernet0/0 ! interface Ethernet0/1 switchport access vlan 2 ! interface Vlan1 nameif inside security-level 100 ip address 192.168.1.2 255.255.255.0 ! interface Vlan2 nameif outside security-level 0 ip address 10.10.10.1 255.255.255.0 ! object network LAN-inside subnet 192.168.1.0 255.255.255.0 ! route outside 192.168.2.0 255.255.255.0 10.10.10.2 1 ! access-list ACL1 extended permit ip 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0 access-list outside extended permit icmp any any ! ! access-group outside out interface outside object network LAN-inside nat (inside,outside) dynamic interface ! class-map inspection_default match default-inspection-traffic ! policy-map global_policy class inspection_default inspect icmp ! ! telnet timeout 5 ssh timeout 5 ! dhcpd auto_config outside ! dhcpd enable inside ! crypto ipsec ikev1 transform-set myset esp-aes esp-sha-hmac ! crypto map cmap 1 match address ACL1 crypto map cmap 1 set peer 10.10.10.2 crypto map cmap 1 set ikev1 transform-set myset crypto map cmap interface outside crypto ikev1 enable outside crypto ikev1 policy 1 encr aes authentication pre-share group 2 ! tunnel-group 10.10.10.2 type ipsec-l2l tunnel-group 10.10.10.2 ipsec-attributes ikev1 pre-shared-key cisco123
ASA1 configuration
ASA Version 8.4(2) ! hostname ASALausanne names ! interface Ethernet0/0 ! interface Ethernet0/1 switchport access vlan 2 ! interface Vlan1 nameif inside security-level 100 ip address 192.168.2.2 255.255.255.0 ! interface Vlan2 nameif outside security-level 0 ip address 10.10.10.2 255.255.255.0 ! object network LAN-inside subnet 192.168.2.0 255.255.255.0 ! route outside 192.168.1.0 255.255.255.0 10.10.10.1 1 ! access-list ACL2 extended permit ip 192.168.2.0 255.255.255.0 192.168.1.0 255.255.255.0 access-list outside extended permit icmp any any ! access-group outside out interface outside object network LAN-inside nat (inside,outside) dynamic interface ! class-map inspection_default match default-inspection-traffic ! policy-map global_policy class inspection_default inspect icmp ! telnet timeout 5 ssh timeout 5 ! dhcpd auto_config outside ! dhcpd enable inside ! crypto ipsec ikev1 transform-set myset esp-aes esp-sha-hmac ! crypto map cmap 1 match address ACL2 crypto map cmap 1 set peer 10.10.10.1 crypto map cmap 1 set ikev1 transform-set myset crypto map cmap interface outside crypto ikev1 enable outside crypto ikev1 policy 1 encr aes authentication pre-share group 2 ! tunnel-group 10.10.10.1 type ipsec-l2l tunnel-group 10.10.10.1 ipsec-attributes ikev1 pre-shared-key cisco123 !
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2018 07:41 AM
Hello @MrEtho53,
There is no alternative in Packet-Tracer that´s what you get, nothing else. I would suggest using GNS3 or EVE-NG (better option) for your labs.
Unfortunately, Packet-tracer is very limited in Firewalling.
HTH
Gio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2018 03:35 AM
It seems you are nating the vpn packets, that will cause not to match the crypto-acl.
In order to avoid that you can configure identity nat for the vpn traffic. Should be something like:
ASA0 configuration:
object network LAN-remote
subnet 192.168.2.0 255.255.255.0
!
nat (inside,outside) source static LAN-inside LAN-inside destination static LAN-remote LAN-remote no-proxy-arp route-lookup
ASA1 configuration:
object network LAN-remote
subnet 192.168.1.0 255.255.255.0
!
nat (inside,outside) source static LAN-inside LAN-inside destination static LAN-remote LAN-remote no-proxy-arp route-lookup
HTH
Bogdan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2018 04:26 AM
Thank you very much for your answer, unfortunately in packet tracer my Firewall ASA 5505 doesn't have the nat command in "(config) #".
So what can I do in alternative?
See it below:
A big thanks.
ASAVevey(config)#?
aaa Enable, disable, or view user authentication, authorization
and accounting
access-group Bind an access-list to an interface to filter traffic
access-list Configure an access control element
boot Set system boot parameters
class-map Configure MPF Class Map
clock Configure time-of-day clock
configure Configure using various methods
crypto Configure IPSec, ISAKMP, Certification, authority, key
dhcpd Configure DHCP Server
domain-name Change domain name
enable Configure password for the enable command
end Exit from configure mode
exit Exit from configure mode
group-policy Configure or remove a group policy
hostname Change host name of the system
http Configure http server and https related commands
interface Select an interface to configure
ipv6 Global IPv6 configuration commands
name Associate a name with an IP address
names Enable/Disable IP address to name mapping
no Negate a command or set its defaults
ntp Configure NTP
object Configure an object
object-group Create an object group for use in 'access-list', etc
passwd Change Telnet console access password
policy-map Configure MPF Parameter Map
route Configure a static route for an interface
service-policy Configure MPF service policy
setup Pre-configure the system
ssh Configure SSH options
telnet Add telnet access to system console or set idle timeout
tunnel-group Create and manage the database of connection specific records
for IPSec connections
username Configure user authentication local database
webvpn Configure the WebVPN service
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2018 07:41 AM
Hello @MrEtho53,
There is no alternative in Packet-Tracer that´s what you get, nothing else. I would suggest using GNS3 or EVE-NG (better option) for your labs.
Unfortunately, Packet-tracer is very limited in Firewalling.
HTH
Gio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2018 05:05 AM
Considering it is a lab and you want to test the vpn, you could remove the nat config.
object network LAN-inside no nat (inside,outside) dynamic interface
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide