- Cisco Community
- Technology and Support
- Security
- Network Security
- I realized this right after I
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2014 12:00 PM - edited 03-11-2019 09:49 PM
We have Trustwave for PCI Compliance Scanner. Recently they scanned us and came up with this error "SSL Certificate Public Key to small" Says it is currently 1024 and needs to be 2048. It shows our public IP on port 443 for what it is trying to talk to. I have no Idea if it is trying to talk to the firewall or a server or anything that goes out our public address. I honestly just have no clue about Certificates.
Any Ideas on how I can track down what it is talking to? I looked at the firewall and nothing under Certificate Management is configured. We have an ASA 5510
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2014 01:04 PM
An SSL certificate on an ASA firewall is most commonly used for one of two things:
- ASDM access (which uses https / ssl as its transport)
- Remote access SSL VPN using AnyConnect Essentials or Premium (aka clientless).
There are some other uses but those cover probably 90%+ of the ASAs I've seen.
In any case, if you have management access enabled on your public-facing interface or a working SSL VPN you will have a certificate. Even if you don't have a persistent one, the ASA will generate one dynamically whenever it boots up so that you can at least use ASDM to manage it.
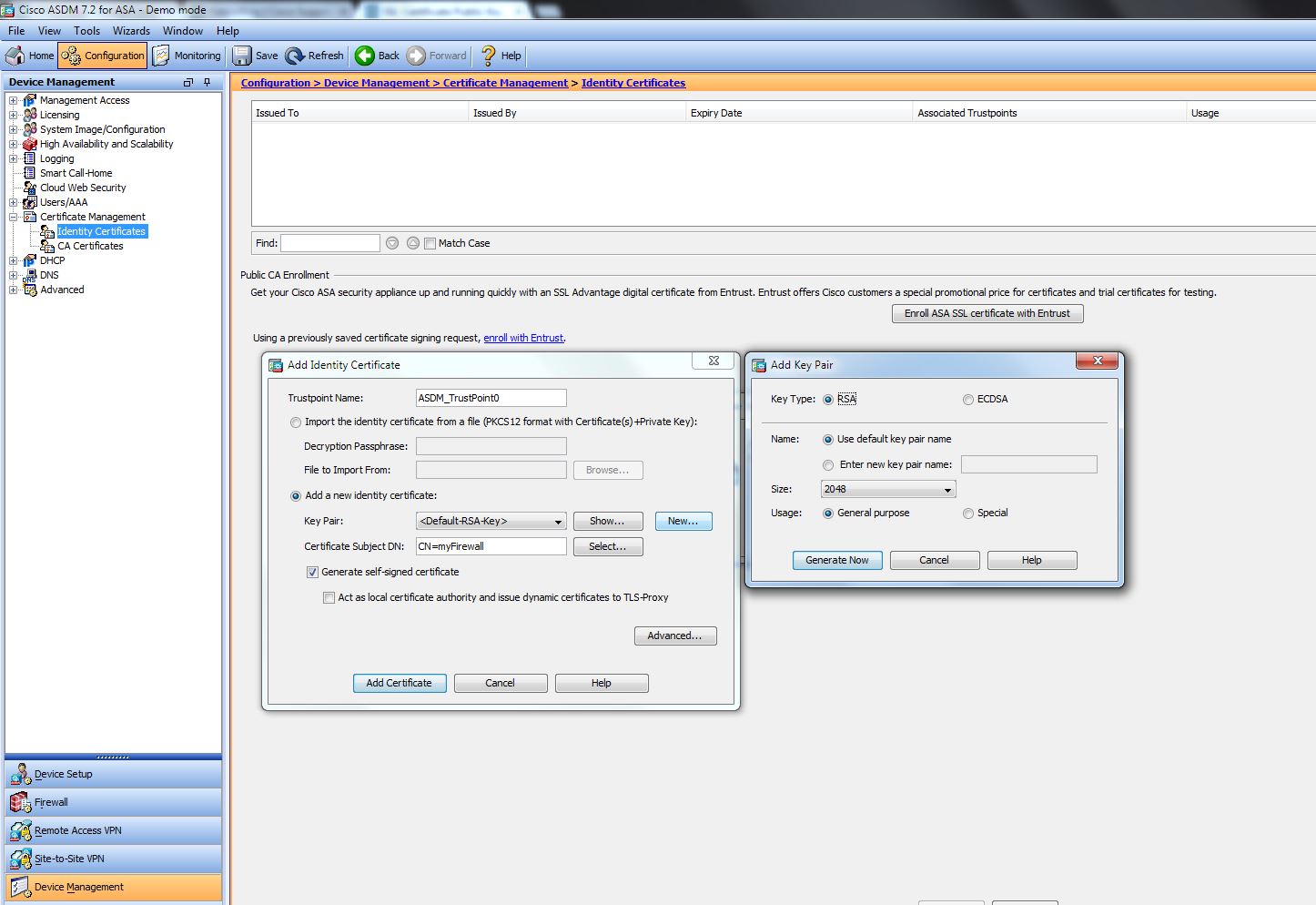
It's not too hard to recreate a self-signed one using a 2048-bit RSA key. The important bit is to first generate a new key and specify the key length as 2048 bits. That key is used to sign a self-signed certificate. You can do it all via ASDM as shown in the screenshot below. The commands for cli are:
crypto key generate rsa label <Default-RSA-Key> modulus 2048 noconfirm
crypto ca trustpoint ASDM_TrustPoint0
revocation-check none
id-usage ssl-ipsec
no fqdn
subject-name CN=myFirewall
enrollment self
crypto ca enroll ASDM_TrustPoint0 noconfirm
You can opt to name the key and trustpoint to something more illustrative for your purposes.
(If you should happen to be using a certificate issued by a 3rd party certificate authority (CA) like entrust, GoDaddy, Verisign etc. you'd need to get a new one. That's unlikely though since most public CAs have only been offering 2048-bit SSL certificates for several years now.)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2014 08:41 AM
Once you've created the 2048-bit key and used it to sign the new self-signed certificate you can check it via Configuration > Device Management > Certificate Management > Identity Certificates. Select the new certificate and then "Show Details".
You also need to make sure to bind that certificate to your interface. Configuration > Device Management > Advanced > SSL Settings
In the config that looks something like:
ssl trust-point <new certificate name>
(replacing the bracketed section with your new certificate name).
Once you have the certificate created and bound you can always browse to your management-enabled interface and use your browser to inspect the certificate by clicking on the lock icon in the URL bar.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2014 01:04 PM
An SSL certificate on an ASA firewall is most commonly used for one of two things:
- ASDM access (which uses https / ssl as its transport)
- Remote access SSL VPN using AnyConnect Essentials or Premium (aka clientless).
There are some other uses but those cover probably 90%+ of the ASAs I've seen.
In any case, if you have management access enabled on your public-facing interface or a working SSL VPN you will have a certificate. Even if you don't have a persistent one, the ASA will generate one dynamically whenever it boots up so that you can at least use ASDM to manage it.
It's not too hard to recreate a self-signed one using a 2048-bit RSA key. The important bit is to first generate a new key and specify the key length as 2048 bits. That key is used to sign a self-signed certificate. You can do it all via ASDM as shown in the screenshot below. The commands for cli are:
crypto key generate rsa label <Default-RSA-Key> modulus 2048 noconfirm
crypto ca trustpoint ASDM_TrustPoint0
revocation-check none
id-usage ssl-ipsec
no fqdn
subject-name CN=myFirewall
enrollment self
crypto ca enroll ASDM_TrustPoint0 noconfirm
You can opt to name the key and trustpoint to something more illustrative for your purposes.
(If you should happen to be using a certificate issued by a 3rd party certificate authority (CA) like entrust, GoDaddy, Verisign etc. you'd need to get a new one. That's unlikely though since most public CAs have only been offering 2048-bit SSL certificates for several years now.)

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2014 06:30 AM
When I try this in the GUI it says "Default key pair already exists"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2014 06:51 AM
Just click the radio button for "Enter new key pair name" and give it a new name. I typically use something like "2048-bit RSA key" so it's immediately apparent what it is.
You will then select that newly-created key pair in the parent dialog box for "Add Identity Certificate" .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2014 08:18 AM
Did the scan with Trustwave and still got the same error.
How can I verify that the new 2048-bit key took the defaults place?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2014 08:41 AM
Once you've created the 2048-bit key and used it to sign the new self-signed certificate you can check it via Configuration > Device Management > Certificate Management > Identity Certificates. Select the new certificate and then "Show Details".
You also need to make sure to bind that certificate to your interface. Configuration > Device Management > Advanced > SSL Settings
In the config that looks something like:
ssl trust-point <new certificate name>
(replacing the bracketed section with your new certificate name).
Once you have the certificate created and bound you can always browse to your management-enabled interface and use your browser to inspect the certificate by clicking on the lock icon in the URL bar.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2014 10:24 AM
I realized this right after I replied to you. The Trustwave scan passed successfully. Thanks for the help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2015 10:21 AM
Hello Mr. Rhoads,
I have the similar problem with a Trustwave Scan Failure...
A. SSL Certificate Public Key Too Small
Also, another Failure...
B. OpenSSL ChangeCipherSpec Man in the Middle Vulnerability
We have a Cisco RV042 router and according to Trustwave it is the router itself that has the vulnerablity; they pointed to the RV042 MAC address in the report.
In case A they suggest "Install a server certificate signed with a public key length of at least 2048 bits."
In case B the suggest "This issue was fixed in OpenSSL versions 0.9.8za, 1.0.0m, and 1.0.1h. It is strongly recommended to install the newest, stable version of OpenSSL."
However, we do not have any "hosts" on our private LAN to update.
Question. Is this related to the RV042 -> Firewall -> General -> Remote Managment or HTTPS: Enabled/Disabled functions?
Thanks in advanced.
LP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2015 12:06 PM
Sorry da-aw-001 but I've never worked with the small business routers such as the RV042.
You can try the "small business routers" forum and might find some folks there with specific knowledge on those products.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2015 01:55 PM
Mr Rhoads, thanks for the tip. I wil try the other forum.
LP
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:


