- Cisco Community
- Technology and Support
- Security
- Network Security
- Subinterface doesn't respond to pings - NP Identity ifc
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Subinterface doesn't respond to pings - NP Identity ifc
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2012 04:29 PM - edited 03-11-2019 03:51 PM
I'm trying to set up an 802.1 q trunk between my layer 3 switch and ASA5520. I understand I need to create a subinterface to accomplish this and have done so. However, the subinterface does not respond to pings, and when I attempt to run the packet tracer on the firewall itself, I get a message saying Flow is denied by configured rule. But the strange thing is it shows the output interface as "np identity ifc":
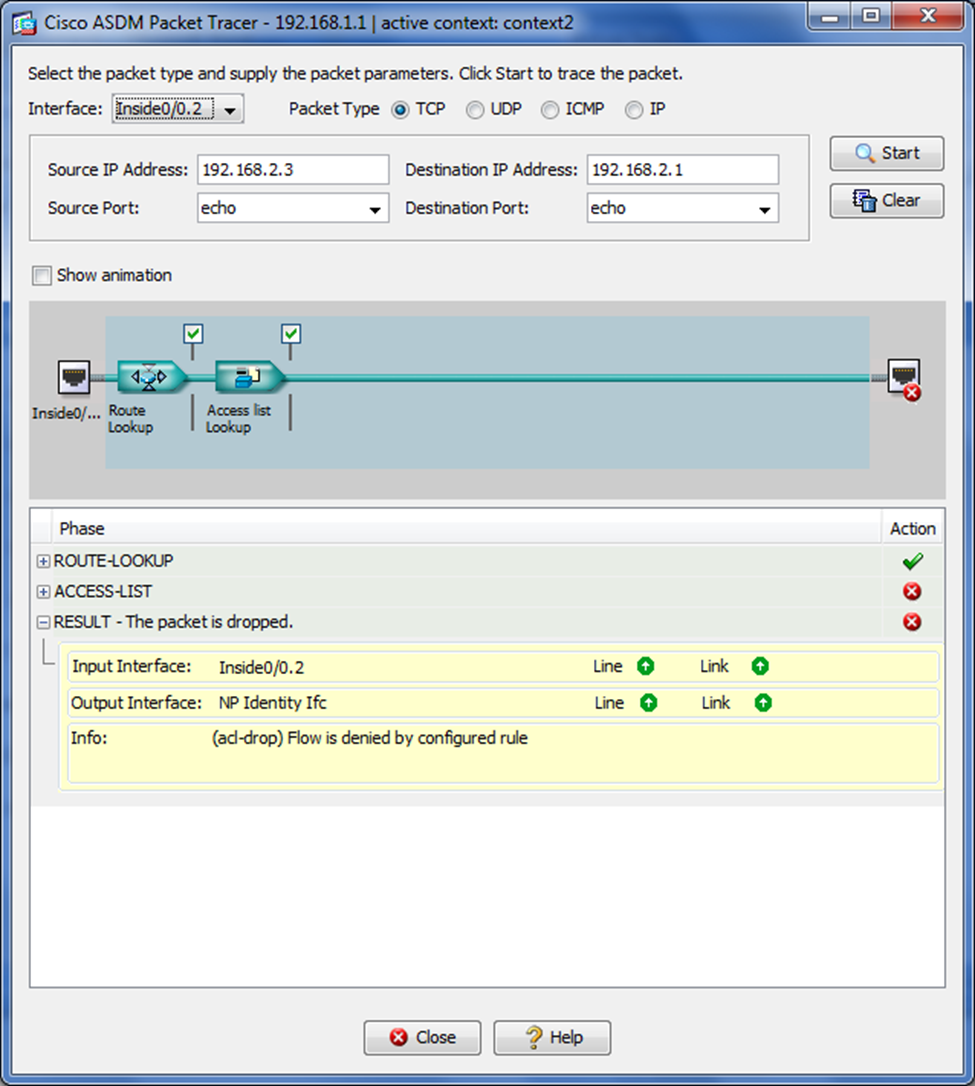
(The VLAN in question is VLAN2 192.168.2.3 is the VLAN2 address on the switch). The ASA config is as follows:
:
ASA Version 8.2(5) <context>
!
hostname context2
names
!
interface GigabitEthernet0/0.2
nameif Inside0/0.2
security-level 20
ip address 192.168.2.1 255.255.255.0 standby 192.168.2.2
!
interface Outside
nameif Outside
security-level 40
ip address 157.142.246.132 255.255.255.0 standby x.x.246.134
!
interface Management
nameif Management
security-level 100
ip address 192.168.4.2 255.255.255.0 standby 192.168.4.4
management-only
!
interface GigabitEthernet0/0
no nameif
no security-level
no ip address
!
pager lines 24
mtu Outside 1500
mtu Management 1500
mtu Inside0/0.2 1500
no monitor-interface Outside
no monitor-interface Management
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
route Outside 0.0.0.0 0.0.0.0 x.x.246.1 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
http server enable
http 192.168.0.0 255.255.0.0 Management
http 192.168.0.0 255.255.0.0 Inside0/0.2
no snmp-server location
no snmp-server contact
telnet 192.168.0.0 255.255.0.0 Management
telnet 192.168.0.0 255.255.0.0 Inside0/0.2
telnet timeout 5
ssh timeout 5
no threat-detection statistics tcp-intercept
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect ip-options
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
!
service-policy global_policy global
: end
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2012 06:09 AM
The sub-interface needs a vlan id, something like:
interface GigabitEthernet0/0.2
vlan 2
nameif Inside0/0.2
security-level 20
ip address 192.168.2.1 255.255.255.0 standby 192.168.2.2
!
Also on the switch dont forget to create vlan 2, than double check that it is allowed to cross the trunk.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2012 08:32 AM
Thanks for the reply.
A bit more info - the ASA is part of an active/active pair, and from what I understand, the VLAN can only be set at the system level. I have done this for int gigabitethernet0/0.2 in the system config (VLAN2), but for some reason when I show the config at the context level it does not show the VLAN.
Also, I have confirmed the switchport is set for 802.1q trunking and VLAN 2 is allowed.
Is there something else I need to do to make sure the VLAN assignment is applied at the context level on the ASA? Also, would this prevent the packet tracer from pinging the interface from the same subnet?
A little stumped here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2012 10:42 PM
Bump...Any resolution? I have the exact same issue.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
