- Cisco Community
- Technology and Support
- Security
- Network Security
- Trouble reaching webserver on inside interface from guest
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2013 04:45 AM - edited 03-11-2019 08:00 PM
I have a problem once again
I am trying to reach a webserver which is located on the inside interface 192.168.190.27 from the Guest Interface which has 10.10.10.0
See the diagram: 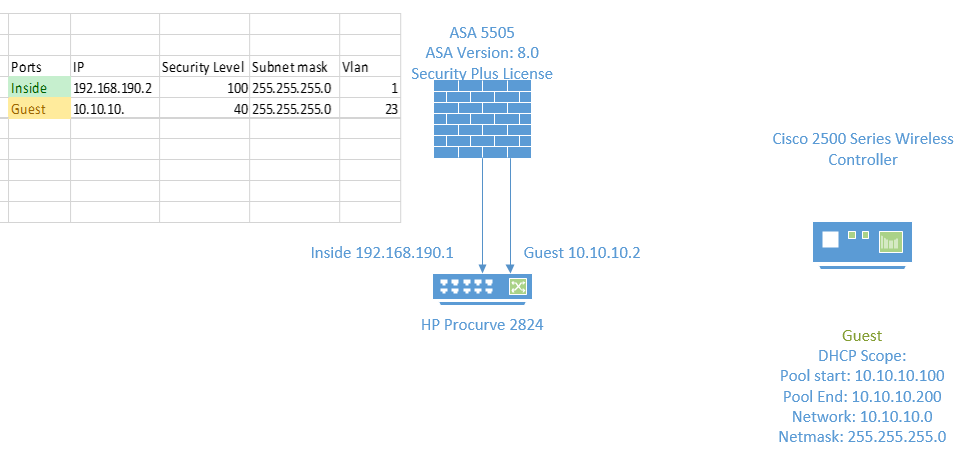
I can ping from for example 10.10.10.103 a windows 7 client to the server 192.168.190.27.. Which works without a problem.
Pinging from the server to the client works fine..
But when i try to browse to http://192.168.190.27 https://192.168.190.27 no luck
Packet capture from the client 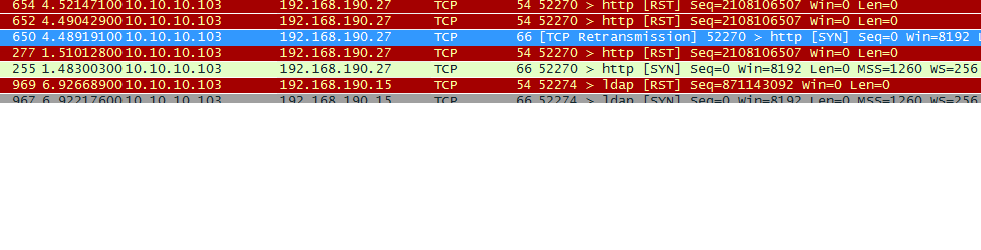
a bunch of RST packets
And here is a pic from the logging in the ASA..
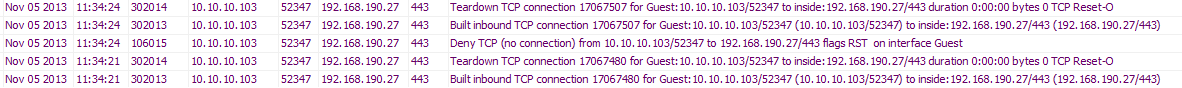
sh run | in Guest
nameif Guest
access-list Guest_access_in extended permit ip 10.10.10.0 255.255.255.0 any
access-list Guest_nat0_outbound extended permit ip 10.10.10.0 255.255.255.0 192.168.190.0 255.255.255.0
mtu Guest 1500
nat (Guest) 0 access-list Guest_nat0_outbound
nat (Guest) 1 10.10.10.0 255.255.255.0
static (inside,Guest) 192.168.190.0 192.168.190.0 netmask 255.255.255.0
static (Guest,inside) 10.10.10.0 10.10.10.0 netmask 255.255.255.0
access-group Guest_access_in in interface Guest
dhcpd address 10.10.10.100-10.10.10.200 Guest
dhcpd dns 192.168.190.91 192.168.190.15 interface Guest
dhcpd enable Guest
Appreciate all your help!
Shane
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2013 04:21 AM
Hi,
That is a clear problem with regards to the operation of the ASA.
If you now have routing activated on the HP Switch (as you say) and you have a Guest Vlan interface on the HP switch with an IP address from the network 10.10.10.0/24 then traffic (or return traffic) from network 192.168.190.0/24 will never pass through the ASA. ASA has to see the whole TCP conversation between the devices in different network, not just the other half.
The simplest solution for ASA would be to have a the HP Switch only act as a L2 switch for the 2 user Vlans and the ASA act as the L3 point for the network. Alternatively you could remove any L3 related operation for Guest Vlan from the HP Switch and leave the original LAN network 192.168.190.0/24 as it is.
So if possible you could remove the Vlan interface IP address for the Guest Vlan so the only routing device for that Vlan would be the ASA.
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2013 05:00 AM
Hi,
Just to be sure, can you provide the output of "packet-tracer"
packet-tracer input Guest tcp 10.10.10.103 12345 192.168.190.27 80
The screencapture from Wireshark seems to have its packets in the wrong order? Do you have a complete capture file of connection attempts that you could provide to us?
Is the HP switch you are using purely a L2 switch or does it have L3/Routing capabilities?
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2013 05:28 AM
Hi,
The output from the packet-tracer:
Phase: 1
Type: FLOW-LOOKUP
Subtype:
Result: ALLOW
Config:
Additional Information:
Found no matching flow, creating a new flow
Phase: 2
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
static (inside,Guest) 192.168.190.0 192.168.190.0 netmask 255.255.255.0
match ip inside 192.168.190.0 255.255.255.0 Guest any
static translation to 192.168.190.0
translate_hits = 0, untranslate_hits = 1560025
Additional Information:
NAT divert to egress interface inside
Untranslate 192.168.190.0/0 to 192.168.190.0/0 using netmask 255.255.255.0
Phase: 3
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group Guest_access_in in interface Guest
access-list Guest_access_in extended permit ip 10.10.10.0 255.255.255.0 any
Additional Information:
Phase: 4
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 5
Type: NAT-EXEMPT
Subtype: rpf-check
Result: ALLOW
Config:
Additional Information:
Phase: 6
Type: NAT
Subtype:
Result: ALLOW
Config:
static (Guest,inside) 10.10.10.0 10.10.10.0 netmask 255.255.255.0
match ip Guest 10.10.10.0 255.255.255.0 inside any
static translation to 10.10.10.0
translate_hits = 15571, untranslate_hits = 0
Additional Information:
Static translate 10.10.10.0/0 to 10.10.10.0/0 using netmask 255.255.255.0
Phase: 7
Type: NAT
Subtype: host-limits
Result: ALLOW
Config:
static (Guest,inside) 10.10.10.0 10.10.10.0 netmask 255.255.255.0
match ip Guest 10.10.10.0 255.255.255.0 inside any
static translation to 10.10.10.0
translate_hits = 15571, untranslate_hits = 0
Additional Information:
Phase: 8
Type: NAT
Subtype: rpf-check
Result: ALLOW
Config:
static (inside,Guest) 192.168.190.0 192.168.190.0 netmask 255.255.255.0
match ip inside 192.168.190.0 255.255.255.0 Guest any
static translation to 192.168.190.0
translate_hits = 0, untranslate_hits = 1560028
Additional Information:
Phase: 9
Type: NAT
Subtype: host-limits
Result: ALLOW
Config:
static (inside,outside) x.x.x.x 192.168.190.27 netmask 255.255.255.255
match ip inside host 192.168.190.27 outside any
static translation to x.x.x.x
translate_hits = 251573, untranslate_hits = 636450
Additional Information:
Phase: 10
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 11
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 17190653, packet dispatched to next module
Phase: 12
Type: ROUTE-LOOKUP
Subtype: output and adjacency
Result: ALLOW
Config:
Additional Information:
found next-hop 192.168.190.27 using egress ifc inside
adjacency Active
next-hop mac address 000c.2946.f8e5 hits 1
Result:
input-interface: Guest
input-status: up
input-line-status: up
output-interface: inside
output-status: up
output-line-status: up
Action: allow
The HP switch is a L3..
I'll get back to you asap with the capture file..
Thanks
Shane
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2013 05:31 AM
Hi,
So if the HP switch is indeed L3 and doing routing then could you tell me if both "inside" and "Guest" networks have an Vlan interface with IP address on the HP Switch? If they do, does that IP act as the default gateway for either of "inside" / "Guest" user networks?
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2013 05:57 AM
Yes it does.. here is the output from the show ip route on the switch..

/shane
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2013 06:02 AM
Hi,
What is the configured gateway IP address for the "inside" and "Guest" networks?
Is it some IP address configured on the HP Switch or the ASA5505.
If one network is using ASA as the gateway and the other is using the HP Switch then you will have routing problems
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2013 07:26 AM
Hi,
Gateway for the inside= 192.168.190.2
guest= 10.10.10.1
Its the ip configured on the interfaces of the ASA..
Here is the pcap file:
https://lifesthlm.com/owncloud/public.php?service=files&t=718a347d89adc98c3836b2835546ce21
/shane
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2013 09:09 AM
Just remove the layer 3 configuraton from the HP switch for the 10 network and haver server and PC point to the ASA.
If you have a lot of devices pointing to the switch IP remove the IP from the switch and swap it out on the interface of the ASA guest interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2013 09:23 AM
Hi,
Maybe you should also share the ASA configuration that we can be sure there there is no problem there.
The capture only seems to show TCP SYNs that the host sends and Resets right away after sending the SYN. There is absolutely no return traffic from the server itself.
If neither network uses the HP switch as their L3 gateway then I imagine that there should not be problems regarding the routing though it would still be best to have no routing related to the different LAN Networks on the HP Switch but only have some Management Vlan on the switch for remote management from some LAN network.
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2013 09:30 AM
Also the complete capture because I can't confirm who is sending the RST, it could be another device.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2013 10:19 AM
Hi,
It would seem to me that the TCP Reset is from the same source MAC address as the actual host that sent the TCP SYN.
I would imagine that if the ASA was sending the TCP Reset for example (or some other device) that the TCP Reset would also be coming with the source IP address of the server.
I am not sure why the host itself sending the TCP Reset.
I presume this capture is from the actual host or is it from the ASA?
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2013 10:40 AM
Well if we can't see the MAC addresses we cannot confirm, that is why I'm asking for the sniffer file.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2013 10:45 AM
Hi,
But I just said we can see the MAC address? But more importantly I would imagine that if some other device was sending the TCP Reset it would not be sending the TCP Reset with the source IP address of the connecting host but rather then destination hosts/servers IP address.
We havent seen the configuration of the ASA but the information would seem to suggest that both network are directly connected to the ASA so whether the capture was taken from the host or the ASA we should be seeing the actual source MAC address of the packet in the capture file that was linked in the earlier post.
Though it does seem strange that in the capture there is nothing from the server or from any other device. I am not sure why that would happen though unless there is another NIC involved somehow.
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2013 10:50 AM
Ups did not see the file LoL just saw the image
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2013 03:48 AM
Yeah it seems that the devices on the 192.168.190.0 netwok have a default gateway of the ip configured on the HP switch which is 192.168.190.1..
And the 10.10.10.0 network uses the 10.10.10.1 which is the ip on Guest interface of the ASA.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:


