- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Wildcard or variables in Access Policies on FTD
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2017 11:31 PM - edited 02-21-2020 06:24 AM
Hello,
Is there any way to achieve implementation of wildcard masks or variables in IP addresses in FTD? Particularly for example I need to create a policy to deny the traffic from particular host to IP addresses ending with .121 in all our branches (there are 70 branches with subnets like 192.168.10.0/24, 192.168.11.0/24, 192.168.13.0/24, etc). I want to accomplish this by creating a single rule? The oprion of creating 70 network objects is also not convenient.
Thank you!
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2017 07:11 AM - edited 10-01-2017 01:29 PM
Hello Neroshake,
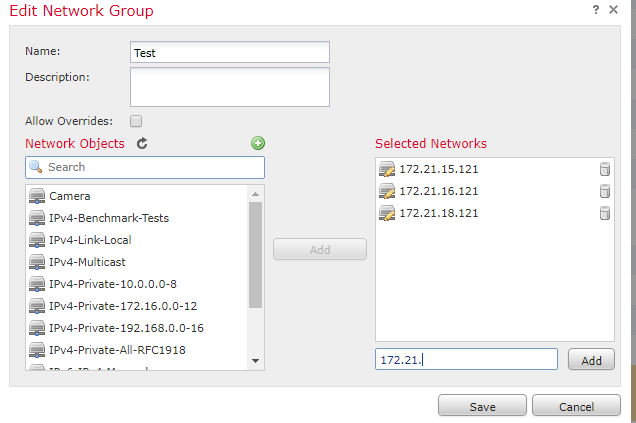
Wildcards are not currently supported in the Firepower Threat Defense or the ASA.
I would create a group and add them individually to the group - Thereby you save time by not having to create 70 network object. See the example below:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2017 12:26 AM
Yes, you can apply wildcard mask to filter specific hosts from different networks. For example,
if you have 192.168.11.0/24, 192.168.13.0/24, 192.168.14.0/24,..., and you choose to allow only to one host in each network (192.168.x.121), run the following command:
access-list 1 permit 192.168.0.121 0.0.255.0
What you basically did is that you want to match 192.168 and 121, but not the 3rd octet.
Please rate it if you find it helpful : )
HTH,
Meheretab
Meheretab
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2017 12:20 AM
Thank you, meheretabm!
My deployment is a HA of two FTDs managed by FMC. Where I should enter that ACLs and how do I connect them with Access Policies?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2017 07:33 AM - edited 09-30-2017 07:33 AM
The earlier respondent was thinking about ASA and/or router ACLs. Unfortunately FTD does not currently have 100% feature parity with ASA - even in something as basic as ACLs.
An FTD / FMC standard or extended access-list entry does not currently (as of 6.2.2) permit non-contiguous netmasks such as you would have to use here to specify all of the .121 hosts with a single object.
You can't even work around by using flexconfig as the access-list command is blacklisted from flexconfig.
I believe the only method is to create all of the individual /32 entries as network objects and then combine them into a group which you can then use in your policies.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2017 07:11 AM - edited 10-01-2017 01:29 PM
Hello Neroshake,
Wildcards are not currently supported in the Firepower Threat Defense or the ASA.
I would create a group and add them individually to the group - Thereby you save time by not having to create 70 network object. See the example below:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2017 07:12 AM
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: