- Cisco Community
- Technology and Support
- Security
- Network Access Control
- adding Posture in dot1x environment
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2019 03:56 PM
Hi Guys:
I'm new in ISE and now I have a good challenge to enable a Posture module for a current environment with dot1x. my deal is I have 30 authorization rules with the syntaxes of:
item 1 AD_group_A then applied VLAN_A
item 2 AD_group_B then Applied VLAN_B
..
item 30 AD_group_30 then applied VLAN_30
After I read the Posture implementation guide, it says We need to create an authorization condition for posture status equal "complaint" and "no complaint", for this reason, I would like to know in your experience if there a way you can create a simple 2 authorization rule in the top of them or I must duplicate all Authz with complaint and No complaint.
Thanks,
Jhony
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2019 04:25 PM
In case the endpoints in your deployment able to get new IP addresses after changing subnets, then it possible to assign the endpoint to a common quarantine subnet before their posture statuses become compliant.
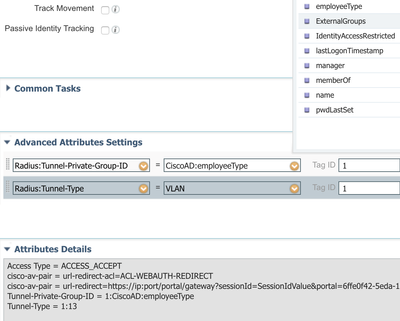
In case to keep separate subnets even during quarantine or in case endpoints unable to refresh IP addresses between unknown and compliant, please see whether we may store the VLAN ID or name as an AD user attribute. This way we might be able to assign the VLAN by the AD user attribute, instead, in the authorization profiles, to aggregate the number of rules and profiles.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2019 04:25 PM
In case the endpoints in your deployment able to get new IP addresses after changing subnets, then it possible to assign the endpoint to a common quarantine subnet before their posture statuses become compliant.
In case to keep separate subnets even during quarantine or in case endpoints unable to refresh IP addresses between unknown and compliant, please see whether we may store the VLAN ID or name as an AD user attribute. This way we might be able to assign the VLAN by the AD user attribute, instead, in the authorization profiles, to aggregate the number of rules and profiles.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: