- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Anyconnect and ISE with DUO MFA strange issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Anyconnect and ISE with DUO MFA strange issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2019 11:53 AM
I am using the ASA to primary auth against Cisco ISE servers and then secondary authentication to DUO proxy servers using DUO_auth Only.
I am seeing some strange things in the ISE radius logs. I see a successful auth followed by a rejected auth, but I still get one and still have access.
First session says 5200 authentication succeeded.
| 24343 | RPC Logon request succeeded - stevenwilliams@eftdomain.net | |
| 24402 | User authentication against Active Directory succeeded - All_AD_Join_Points | |
| 22037 | Authentication Passed | |
| 24423 | ISE has not been able to confirm previous successful machine authentication | |
| 15036 |
Evaluating Authorization Policy |
| 15004 | Matched rule - IT | |
| 15016 | Selected Authorization Profile - SSLVPN_IT | |
| 11022 | Added the dACL specified in the Authorization Profile | |
| 22081 | Max sessions policy passed | |
| 22080 | New accounting session created in Session cache | |
| 11002 | Returned RADIUS Access-Accept |
So that looks good. RADIUS looks good also. Then the second log says RADIUS failed due to incorrect password.
| Event | 5400 Authentication failed |
| Failure Reason | 24408 User authentication against Active Directory failed since user has entered the wrong password |
| Resolution | Check the user password credentials. If the RADIUS request is using PAP for authentication, also check the Shared Secret configured for the Network Device |
| Root cause | User authentication against Active Directory failed since user has entered the wrong password |
| Username | stevenwilliams |
| 24323 | Identity resolution detected single matching account | |
| 24344 | RPC Logon request failed - STATUS_WRONG_PASSWORD,ERROR_INVALID_PASSWORD,stevenwilliams@eftdomain.net | |
| 24408 | User authentication against Active Directory failed since user has entered the wrong password - All_AD_Join_Points | |
| 22057 | The advanced option that is configured for a failed authentication request is used | |
| 22061 | The 'Reject' advanced option is configured in case of a failed authentication request | |
| 11003 | Returned RADIUS Access-Reject |
So I do not get it. The only thing I am thinking is this is happening due to incorrect configuration at the authentication policy area. What are these "suppose" to be how are they "suppose" to be configured? When do they need to be modified?
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2019 09:53 PM
Does your authentication goes to ise first?
Have you deployed duo auth proxy?
Personally, i configure asa to send requests to duo proxy and then duo will forward it to ise for auth and authorization.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2019 06:27 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2019 08:22 AM
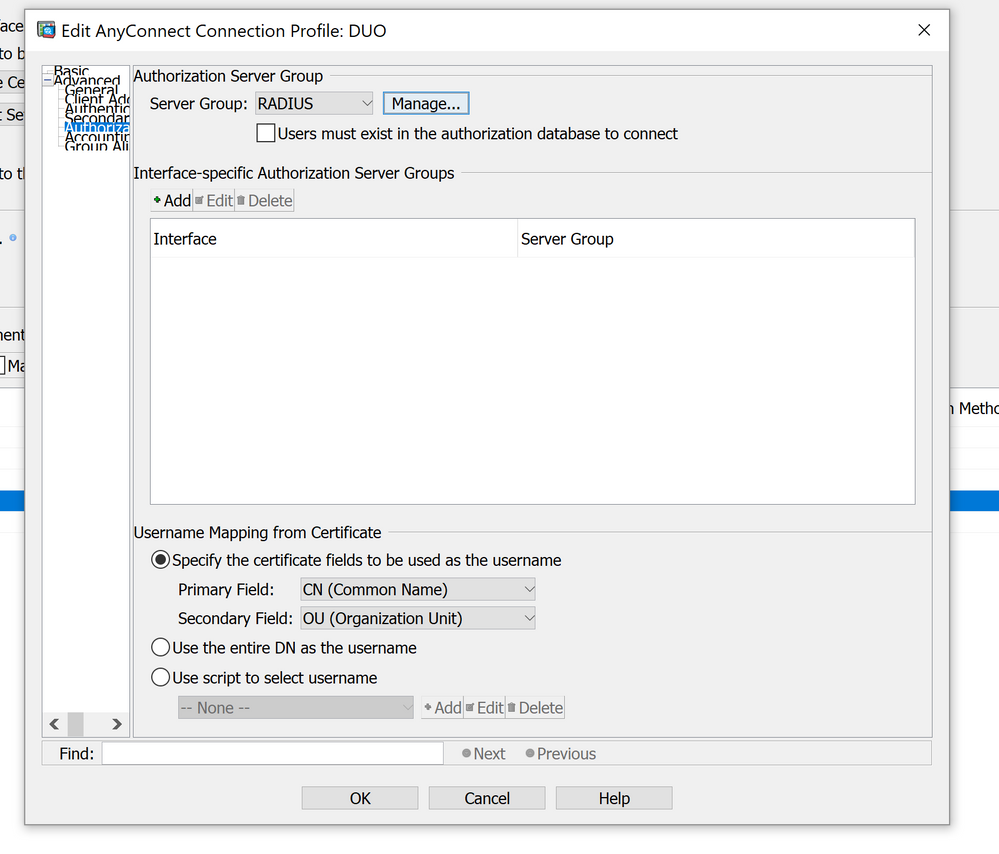
Does DUO auth proxy also tie to the backend AD? IF yes, I believe you can set ISE as only your authorization server. What this should do is authenticate against DUO (with AD and push/passcode) and check authorization against ISE. Authorization is what gives you the DACL's, so your CoA/posture should work normally.
So DUO can be set up as this:
https://duo.com/docs/cisco-alt
And then you add ISE as authz server as seen below:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2019 08:28 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2019 09:42 AM
Ok, makes sense. Can you paste the ASA side config for that tunnel-group?
Also, do you have the ASA radius debug output that you can sanitize and share? My thought is that since the username looks to be shared between the primary and secondary auth, the second failure is when the ASA uses the secondary creds (duo) also for authorization, causing a failure on ISE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2019 06:47 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2019 02:05 PM
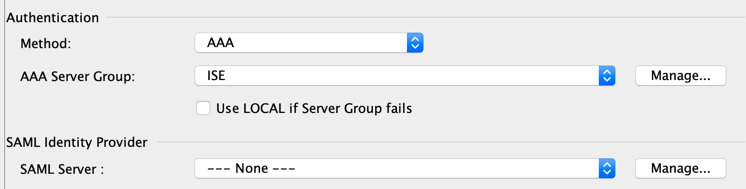
Normally your ASA should reach ISE as radius server.
Then you have on ISE:
- external radius token which will be your duo auth proxy server
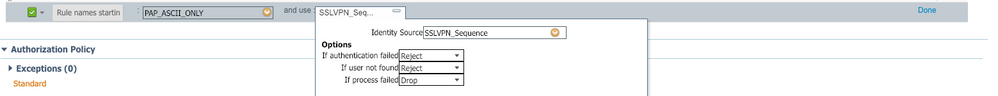
- identity source sequence which has DUO radius token only as source identity
- create a policy-set VPN (just assumption here)
- authentication going to identity source sequence previously created
- authorization policy with your authz profile (dACL,...)
On your duo auth proxy, you have radius_server_auto section (which has ISE IP) + you can have radius_client (your ISE IP as well) to validate users credentials.
Or have you configured it another way?
I'm testing FTD (FDM) 6.4 and tested it with success. (not tested dACL right now) but it shouldn't affect as DUO is part of authentication process only and then authorization is between ISE and ASA
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2019 02:41 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2019 03:01 PM
Then you are in the old fashion way with 1st authentication from ASA to ISE and 2nd authentication to Duo right? Or I missed something here.
The 2nd auth is using DUO-LDAP straight to internet or going to local duo-proxy?
Then why the 2nd auth is sent to ISE which triggers a failed. Normally when ISE replies with an access-accept the 1st time, then ASA should request the 2nd auth server (DUO) to validate the passcode or push the popup.
If using proxy, can you share the authproxy cfg file (remove all passwords) + ASA config ?
Can you also please share ISE config (Identity Source Sequence) and the full log of authentication (both: accept and failed)?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2019 04:00 PM
ASA:
AAA Server Group = ISE Server
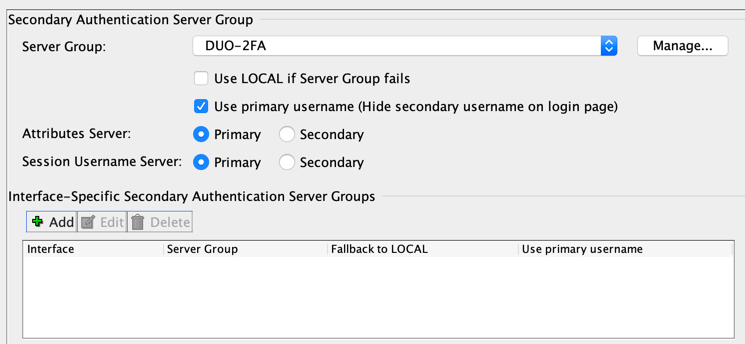
-> Secondary Authentication = DUO-RADIUS -> Use Primary Username
;[radius_server_auto]
;ikey=
;skey=
;api_host=
;radius_ip_1=
;radius_secret_1=
;failmode=safe
;client=ad_client
;port=1812
[duo_only_client]
[radius_server_duo_only]
ikey=DI2DTOC8S*****
skey=qrVyCPhvfkczB7****
api_host=api-7****.duosecurity.com
failmode=safe
radius_ip_1=10.53.0.251
radius_secret_1=****an2nv6ehz9P***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2019 03:35 PM - edited 02-14-2019 04:10 PM
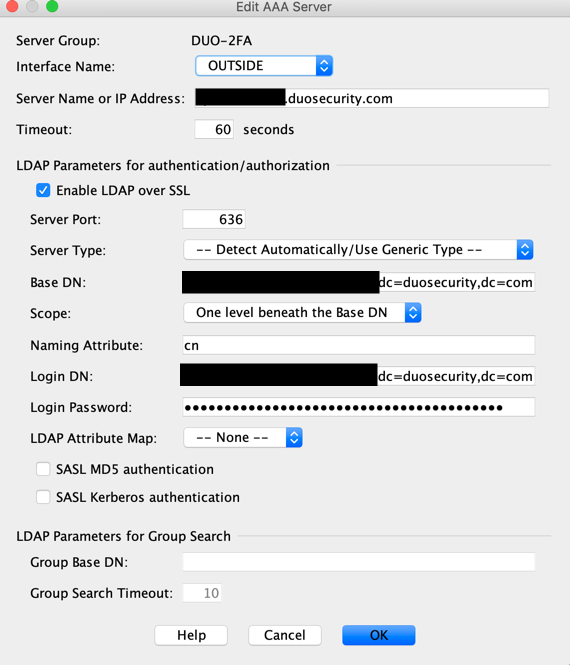
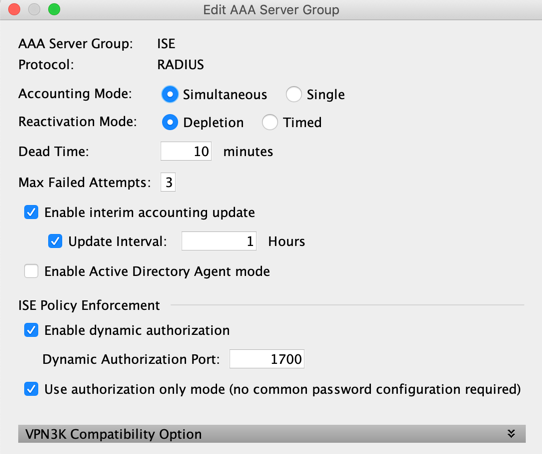
I've done it on my LAB and it works fine. Here my config
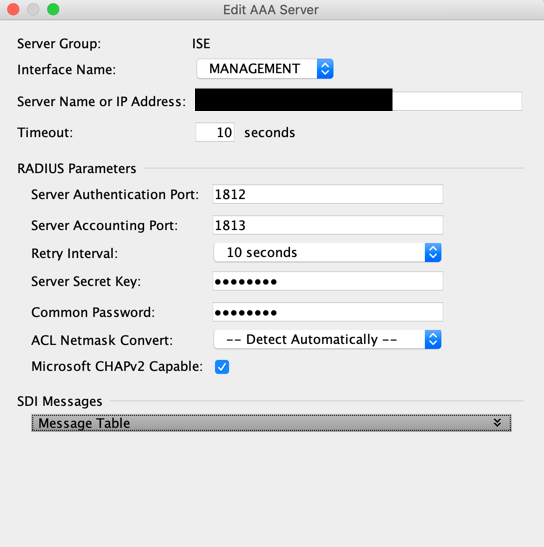
It works like a charm!
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2019 04:01 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2019 04:11 PM
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2019 04:13 PM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide