- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Anyconnect and ISE with DUO MFA strange issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Anyconnect and ISE with DUO MFA strange issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2019 11:53 AM
I am using the ASA to primary auth against Cisco ISE servers and then secondary authentication to DUO proxy servers using DUO_auth Only.
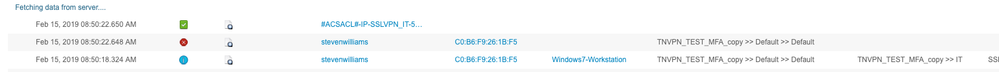
I am seeing some strange things in the ISE radius logs. I see a successful auth followed by a rejected auth, but I still get one and still have access.
First session says 5200 authentication succeeded.
| 24343 | RPC Logon request succeeded - stevenwilliams@eftdomain.net | |
| 24402 | User authentication against Active Directory succeeded - All_AD_Join_Points | |
| 22037 | Authentication Passed | |
| 24423 | ISE has not been able to confirm previous successful machine authentication | |
| 15036 |
Evaluating Authorization Policy |
| 15004 | Matched rule - IT | |
| 15016 | Selected Authorization Profile - SSLVPN_IT | |
| 11022 | Added the dACL specified in the Authorization Profile | |
| 22081 | Max sessions policy passed | |
| 22080 | New accounting session created in Session cache | |
| 11002 | Returned RADIUS Access-Accept |
So that looks good. RADIUS looks good also. Then the second log says RADIUS failed due to incorrect password.
| Event | 5400 Authentication failed |
| Failure Reason | 24408 User authentication against Active Directory failed since user has entered the wrong password |
| Resolution | Check the user password credentials. If the RADIUS request is using PAP for authentication, also check the Shared Secret configured for the Network Device |
| Root cause | User authentication against Active Directory failed since user has entered the wrong password |
| Username | stevenwilliams |
| 24323 | Identity resolution detected single matching account | |
| 24344 | RPC Logon request failed - STATUS_WRONG_PASSWORD,ERROR_INVALID_PASSWORD,stevenwilliams@eftdomain.net | |
| 24408 | User authentication against Active Directory failed since user has entered the wrong password - All_AD_Join_Points | |
| 22057 | The advanced option that is configured for a failed authentication request is used | |
| 22061 | The 'Reject' advanced option is configured in case of a failed authentication request | |
| 11003 | Returned RADIUS Access-Reject |
So I do not get it. The only thing I am thinking is this is happening due to incorrect configuration at the authentication policy area. What are these "suppose" to be how are they "suppose" to be configured? When do they need to be modified?
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2019 04:26 PM
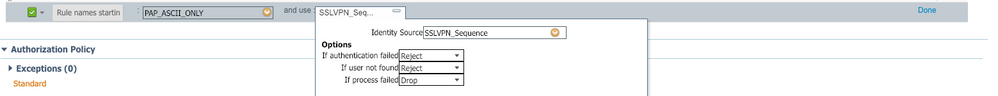
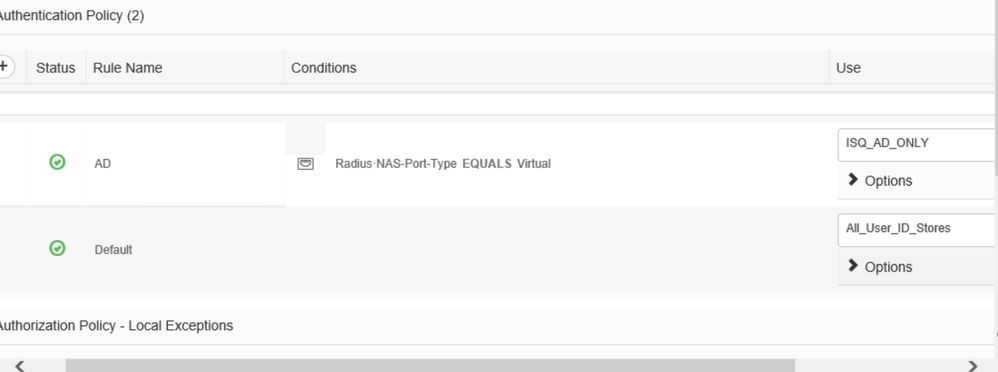
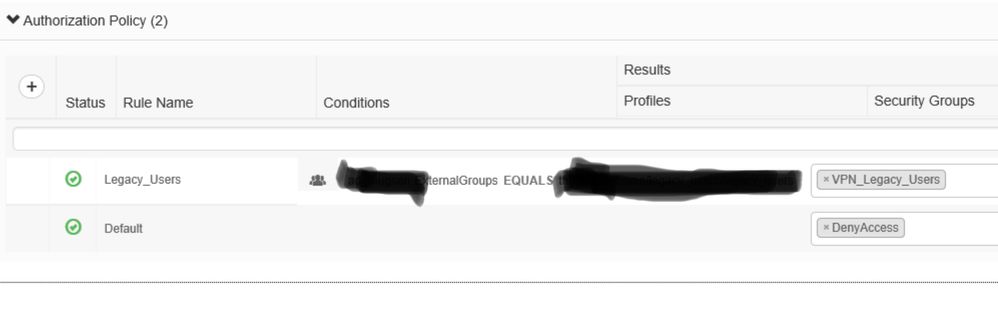
Very basic config. Take a look at the pictures.
I changed to use my duo proxy and it works the same way.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2019 04:30 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2019 04:33 PM
Then, create an ISQ with only 1 AD for testing and see if it works.
Maybe it’s an issue with your multi-domain ISQ.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2019 06:52 AM
The issue has to be with the ASA and/or ISE. I made the secondary authentication DUO-LDAP which will send the request right out to DUO cloud and I still get one success login and one denied login:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2019 06:57 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2019 08:09 AM
If so, can you take a tcpdump on your ISE + a debug on your ASA to see what traffic is exchanged and which one is making trouble here.
The 2nd auth could be either LDAP or PROXY, there's no relationship with ISE because both are going straight to Duo cloud.
Can you also share your ASA config please?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2019 11:05 AM
webvpn
enable outside
anyconnect-essentials
anyconnect image disk0:/anyconnect-macos-4.6.02074-webdeploy-k9.pkg 1
anyconnect image disk0:/anyconnect-win-4.6.02074-webdeploy-k9.pkg 2
anyconnect profiles Anyconnect_Client_Profile_01 disk0:/anyconnect_client_profile_01.xml
anyconnect enable
cache
disable
error-recovery disable
group-policy DfltGrpPolicy attributes
dns-server value 10.20.1.55
vpn-tunnel-protocol ikev1 ikev2 l2tp-ipsec ssl-client ssl-clientless
webvpn
anyconnect profiles value Connection_Profile type user
group-policy VPNGroupPolicy internal
group-policy VPNGroupPolicy attributes
vpn-tunnel-protocol ssl-client
group-policy NA_SSLVPN internal
group-policy NA_SSLVPN attributes
dns-server value 10.20.0.55 10.21.0.56
vpn-idle-timeout 5
vpn-tunnel-protocol ssl-client ssl-clientless
split-tunnel-policy tunnelall
address-pools value Na_VPN_Subnet
webvpn
anyconnect keep-installer installed
anyconnect profiles value Anyconnect_Client_Profile_01 type user
anyconnect ask none default anyconnect
dynamic-access-policy-record DfltAccessPolicy
tunnel-group DefaultWEBVPNGroup general-attributes
address-pool Na_VPN_Subnet
authentication-server-group NA_ISE
secondary-authentication-server-group Duo-LDAP use-primary-username
authorization-server-group NA_ISE
accounting-server-group NA_ISE
default-group-policy NA_SSLVPN
password-management password-expire-in-days 5
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2019 08:07 PM
Can you show the AAA configuration please?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2019 10:14 AM
aaa-server BNA_ISE (Management) host 10.20.0.85
aaa-server BNA_ISE (Management) host 10.81.3.25
aaa-server TACACS protocol tacacs+
aaa-server TACACS (Management) host 10.20.0.85
aaa-server TACACS (Management) host 10.81.3.25
aaa-server Duo-LDAP protocol ldap
aaa-server Duo-LDAP (outside) host api-******.duosecurity.com
aaa-server Duo-RADIUS protocol radius
aaa-server Duo-RADIUS (INSIDE) host 10.20.0.93
aaa authentication enable console TACACS LOCAL
aaa authentication http console TACACS LOCAL
aaa authentication serial console TACACS LOCAL
aaa authentication ssh console TACACS LOCAL
aaa authorization command TACACS LOCAL
aaa accounting ssh console TACACS
aaa accounting serial console TACACS
aaa accounting enable console TACACS
aaa accounting command TACACS
aaa authorization exec authentication-server auto-enable
aaa authentication login-history
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2019 10:31 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2019 05:30 PM
As you're using ise for authentication, this same radius server give authorization through the same flow and no need to resend an authorization to ISE for this same user.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- « Previous
-
- 1
- 2
- Next »
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: