- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ASA5508-X not responding to dynamic authorization request from ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2019 11:48 PM
Hello,
I have set up Posture for AnyConnect VPN clients using ISE 2.4 and ASA ver 9.9.
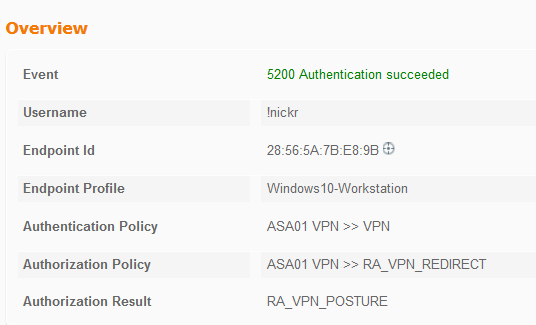
When starting up anyconnect the session connects to the ASA and hits an ISE policy that correctly redirects:
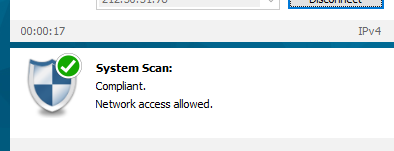
The AnyConnect client then runs a scan of the laptop to check for a simple file and this succeeds:
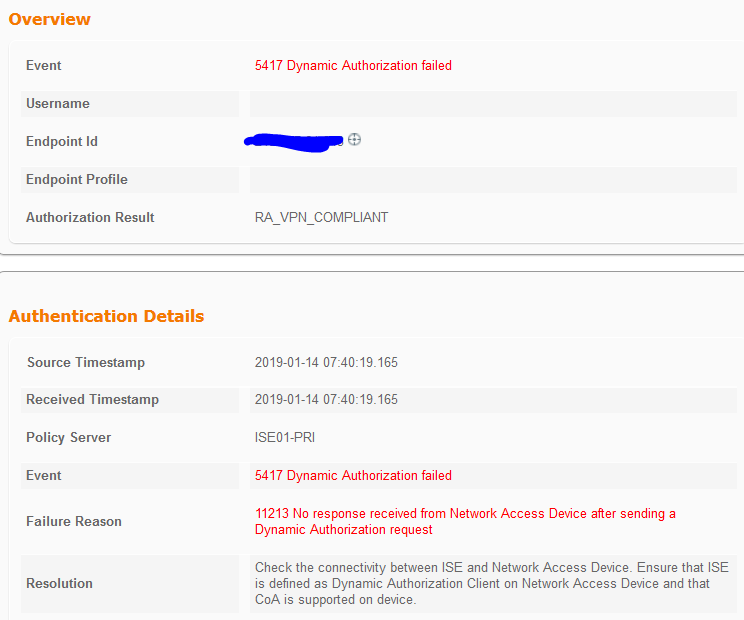
However, the CoA never happens and the logs on ISE show the below:
Below is a portion of the configuration on the ASA:
aaa-server ISE01 protocol radius
authorize-only
interim-accounting-update periodic 1
dynamic-authorization
aaa-server ISE01 (outside) host x.x.x.x
key *****
radius-common-pw *****
aaa-server TACACS-ISE protocol tacacs+
aaa-server TACACS-ISE (outside) host x.x.x.x
key *****
cts sxp enable
user-identity default-domain LOCAL
aaa authentication ssh console TACACS-ISE LOCAL
aaa authentication enable console TACACS-ISE LOCAL
aaa authentication http console ISE01 LOCAL
aaa accounting ssh console ISE01
aaa authentication login-history
webvpn
enable outside
anyconnect image disk0:/anyconnect-win-4.7.00136-webdeploy-k9.pkg 1
anyconnect image disk0:/anyconnect-win-4.5.02033-webdeploy-k9.pkg 2
anyconnect profiles AnyConnect-Profile disk0:/anyconnect-profile.xml
anyconnect enable
tunnel-group-list enable
cache
disable
error-recovery disable
group-policy DfltGrpPolicy attributes
vpn-tunnel-protocol ikev1 l2tp-ipsec ssl-clientless
group-policy ANYCONNECT.GP internal
group-policy ANYCONNECT.GP attributes
dns-server value x.x.x.x
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value SplitTunneling
webvpn
anyconnect profiles value AnyConnect-Profile type user
dynamic-access-policy-record DfltAccessPolicy
tunnel-group ANYCONNECT.VPN type remote-access
tunnel-group ANYCONNECT.VPN general-attributes
address-pool ANYCONNECT
authentication-server-group ISE01
accounting-server-group ISE01
default-group-policy ANYCONNECT.GP
tunnel-group ANYCONNECT.VPN webvpn-attributes
group-alias ANYCONNECT.VPN enable
tunnel-group x.x.x.x type ipsec-l2l
tunnel-group x.x.x.x ipsec-attributes
ikev1 pre-shared-key *****
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****------
When I initially connect my anycconnect to the firewall I see it getting an AV-Pair:
LAB-ASA01# debug radius dynamic-authorization
LAB-ASA01#
LAB-ASA01#
LAB-ASA01# Got AV-Pair with value profile-name=Windows10-Workstation
But nothing else after that.
Any help / ideas would be great.
Thanks
Nick
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2019 06:42 AM
Right, I have found the issue.
The ISE server sits behind a VSE firewall in our cloud. The firewall is configured to NAT incoming traffic destined to ISE 10.99.100.x. on a spare public IP. However, the outbound traffic from the ISE hits an overload NAT and NATs to the outside interface (separate IP than the incoming NAT) of the virtual firewall. So my guess is that this causes asymmetric traffic between ISE and ASA.
Once I created a static 1-to-1 NAT so that the ISE uses the same public IP address for both inbound and outbound traffic ASA successfully responds to the CoA from the ISE and all works correctly.
Thanks
Nick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2019 02:46 AM
Please cross verify this ASA configuration guide Here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2019 04:50 AM
Thank you for the link. This was the actual link I used to configure the ASA and ISE. So all my configuration seems to match.
The issue I see is that the ASA is just not responding to the CoA Request from ISE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2019 04:55 AM - edited 01-14-2019 04:56 AM
Hi,
Is there any firewall between VPN Fw and ISE ?
Are the ports of COA allowed ?
RADIUS Authentication: UDP/1645, 1812
RADIUS Accounting: UDP/1646, 1813
RADIUS Change of Authorization (CoA) Send: UDP/1700
RADIUS Change of Authorization (CoA) Listen/Relay: UDP/1700, 3799
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2019 05:09 AM
Hello,
Yes there is a firewall in front of the ISE server. At present we are allowing all TCP and UDP traffic from the ASA to the ISE and from ISE to ASA.
Thanks
Nick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2019 05:23 AM
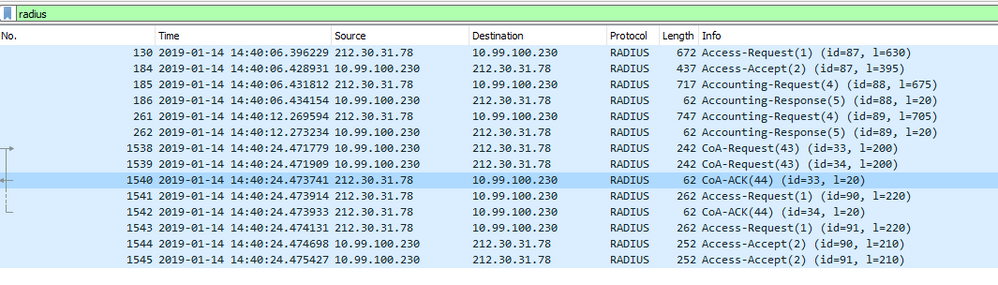
Can you take capture from ISE to ASA/ ASA to ISE and check whether coa-request is send & received by the ISE in the radius packet?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2019 06:42 AM
Right, I have found the issue.
The ISE server sits behind a VSE firewall in our cloud. The firewall is configured to NAT incoming traffic destined to ISE 10.99.100.x. on a spare public IP. However, the outbound traffic from the ISE hits an overload NAT and NATs to the outside interface (separate IP than the incoming NAT) of the virtual firewall. So my guess is that this causes asymmetric traffic between ISE and ASA.
Once I created a static 1-to-1 NAT so that the ISE uses the same public IP address for both inbound and outbound traffic ASA successfully responds to the CoA from the ISE and all works correctly.
Thanks
Nick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2019 06:53 AM
Hi Aravind,
This is exactly what I did earlier. Capture from ISE to ASA shows ISE sending the CoA to the ASA. Capture on ASA does not show the CoA request that ISE sent.
Tweaking the NAT statements on the firewall in from of the ISE server to be a static one-to-one NAT fixed the issue. I believe the issue was caused by asymmetry.
Thanks
Nick
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: