- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Authentication policies order of operation with multiple join points
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2019 08:57 AM
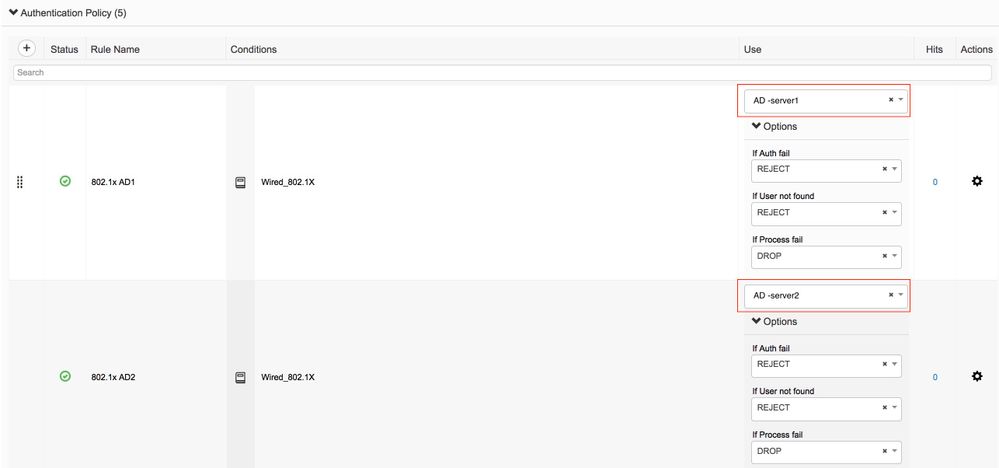
I just wanted to confirm the behaviour, where I have two active directory join points in ISE. If I am not using scope mode or All_AD_Join_Points in Identity Source Sequences can I have multiple authentication policies with a single AD join point?
Example, I have two authentication polices with identical condition, but each one is referencing a different join point. If the user is not found in AD-server1 in rule 802.1x AD1, will ISE move to the next rule 802.1x AD2 and check the user in AD-server2?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2019 04:33 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2019 05:37 PM
Scope is used to have multiple join points. These join points may not be trusted. You will be using the scope in the auth policy or Identity source sequence. At that point ISE checks the join points in the scopes or Identity source sequence since it is part of the same policy, "The USER not found = Reject" does not impact as long as the join points, User stores are part of scopes or ISS.
Thanks
Krishnan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2019 09:17 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2019 09:56 AM
Thanks for the reply. So the way around it is to use "If User not found - CONTINUE" option so the second authentication policy is checked?
And also using a scope with both join points or identity source sequence with each individual join point would work with REJECT option right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2019 12:17 PM
If you provide condition continue it will move to the authorization policy.
You can create a identity source sequence for AD1 and AD2. So that if the user not found on AD1 , then it will do the look up on AD2. This will happen based on the sequence you have defined.
Sathiyanarayanan Ravindran
Please rate the post and accept as solution, if my response satisfied your question:)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2019 04:33 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2019 05:37 PM
Scope is used to have multiple join points. These join points may not be trusted. You will be using the scope in the auth policy or Identity source sequence. At that point ISE checks the join points in the scopes or Identity source sequence since it is part of the same policy, "The USER not found = Reject" does not impact as long as the join points, User stores are part of scopes or ISS.
Thanks
Krishnan
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide