- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Cannot enable admin role for certificate - Error "Certificate must contain the FQDN..."
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2019 12:13 AM - edited 04-09-2019 12:13 AM
ISE 2.2
Running into this weird issue, I am renewing my publicly signed certificate used for all usage types (EAP, Portal, Admin, etc). I am able to assign portal and eap to the new certificate, but not Admin.
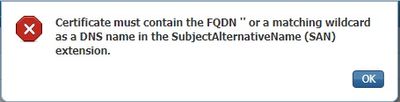
When I try to assign Admin to the new certificate I get this error: "Certificate must contain the FQDN " or a matching wildcard as a DNS name in the SubjectAlternativeName (SAN) extension."
Error message looks a bit broken in the sense that it doesn't mention the FQDN of the node and just a single quote ". The error message should show the node's FQDN correctly, but it doesn't. The new certificate CN and SAN DNS name match exactly and matches the FQDN configured on the node. The thing is the node's FQDN is all lower case while the certificate has the FQDN in all uppercase. I couldn't find anything in the documentation stating the certificate matching for Admin is case sensitive. It mentions best practice to have FQDN as lower case, but nothing about the matching being case sensitive. Can someone please confirm?
And as a test in my lab (ISE 2.4) I just generated a self-signed cert with all upper case FQDN CN and SAN's while my node is lower case and had no issues associating the cert with Admin. Do you know what could be the issue here?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2019 05:05 AM
could it be that the certificate has a typo in it (trailing space) or 0O/l1 mismatch etc.? Unicode?
I sometimes run the cert through openssl to display it in plan text. If the cert is in PEM format then
openssl x509 -in cert.pem -text
And if it's in DER format then openssl x509 -inform DER -in cert.pem -text
It could also be a bug. But see if the FQDN is an EXACT match (apart from the case, which *shouldn't* matter)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2019 05:05 AM
could it be that the certificate has a typo in it (trailing space) or 0O/l1 mismatch etc.? Unicode?
I sometimes run the cert through openssl to display it in plan text. If the cert is in PEM format then
openssl x509 -in cert.pem -text
And if it's in DER format then openssl x509 -inform DER -in cert.pem -text
It could also be a bug. But see if the FQDN is an EXACT match (apart from the case, which *shouldn't* matter)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2019 05:37 AM
Hi Arne,
Thanks, that's some good suggestions. I suspect it could be a trailing space. Will check via openssl and see how it goes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2019 06:06 AM - edited 04-10-2019 06:08 AM
No luck, the certs seem fine (no typo, no trailing space). Tried a new CSR with CN/SAN FQDN all lower case to match the node FQDN, still get the same error. Also tried a self signed cert, no luck.
Looks like a bug to me, the node cannot get its own hostname or domain.
ise-psc.log:
2019-04-10 17:19:27,861 ERROR [admin-http-pool20][] cpm.infrastructure.certmgmt.api.CertMgmtService -:admin::editLocalCert:- Exception occured while getting hostname or domain name
2019-04-10 17:19:27,865 ERROR [admin-http-pool20][] cpm.infrastructure.certmgmt.helpers.CertificateValidationHelper -:admin::editLocalCert:- Certificate must contain host FQDN '' as a DNS name in the SubjectAlternativeName (SAN) extension. DNS value(s) in SAN of the certificate: ise.company.com
then dumps a bunch of java errors.
Anyone from Cisco able to confirm if this is a known issue? Mind you the ISE is running 2.2 patch 2 (which probably explains if its a bug).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2019 07:01 AM
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: