- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Cisco switch administration through radius using ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-01-2019 03:02 AM
Hi all,
To facilitate switch administration using ISE as radius server, I have configured my ISE (v2.4) with the policy set as below.
1) Condition - Radius: Service-Type Equals NAS Prompt
2) Allowed protocols: PAP
3)also configured the necessary authentication and authorization policy.
The above works in terms of administration for my cisco WLC but could not work for my cisco switches.
When i check my ISE logs to verify my admin access for switches via ssh, i notice my attempts to access the switches does not hit the ISE policy set i created, instead it goes to the last default policy set. The endpoint indicated in ise log also reflect the ip address of my client pc attempting ssh to the switch.
I have also added the following for my cisco switches but it fail to work.
1)aaa authentication login default group ISEGRP local
2)aaa authorization exec default group ISEGRP local if-authenticated
"ISEGRP" is defined correctly as my 802.1x config on the switch works for 802.1x for user pc connection against ISE.
Please advise. TIA!
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-02-2019 05:47 PM
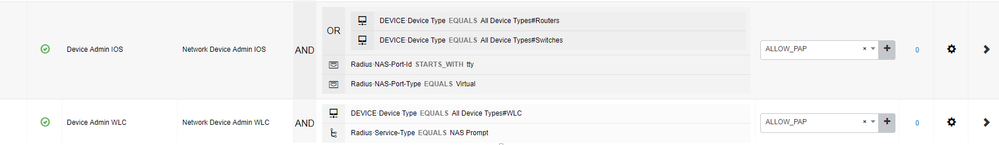
Hi @donnie
AirOS and IOS send different RADIUS Attributes during a device authentication - see below what I have configured in ISE:
For IOS you then return the Cisco AV Pair to assign level 0-15 - cisco-avpair= "shell:priv-lvl=15" etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-01-2019 05:50 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-02-2019 05:47 PM
Hi @donnie
AirOS and IOS send different RADIUS Attributes during a device authentication - see below what I have configured in ISE:
For IOS you then return the Cisco AV Pair to assign level 0-15 - cisco-avpair= "shell:priv-lvl=15" etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2019 06:57 PM
Hi Arne,
Thank you very much. Your suggestion works.
I will fine tune my authorization policy to segregate between user and full priviledge.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide