- Cisco Community
- Technology and Support
- Security
- Network Access Control
- CSCvg88945 CoA on Reprofile Still Not Fixed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2018 11:18 AM - edited 08-09-2018 11:20 AM
<vent mode>
This bug has gone on for so long and it is key concept that has to work in ISE. If there is a profile change and I have CoA set globally to Reauth or specifically set on the profile to Reauth ISE has to send out a CoA.
I am testing this with 2.4 and it still doesn't work. If things go from unknown to anything that works, but when there is a profile change say from Cisco-Device to Cisco-IP-Phone it doesn't work.
In particular, I have IND integrated with ISE setting custom endpoint attribute tags that allow be to switch SGT tags based on these attributes. Profiling with these attributes is working perfectly. As soon as I change the security tag in IND the profile changes in ISE, but no CoA is sent. If I manually CoA life it good.
You might say well what about the silly exception action work around. That does work for the first flip, but then the profile is statically set and no more profiling can occur for that MAC. So when I switch it back in IND it doesn't reprofile.
Can I get an accurate status of this bug or get it reclassified as not fixed? If the devs need someone to truly test out a fix for them I am willing to do that.
</vent mode>
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2018 07:39 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2018 06:17 AM
My open TAC case was also linked to CSCvm22838. TAC said 2.4 patch 4 for targeted release for a fix and tentative early October time frame for release.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2018 06:41 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2018 03:46 PM
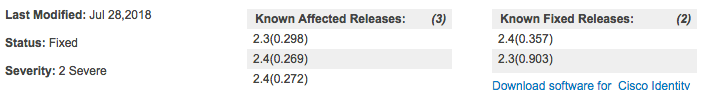
2.3.0.903 means 2.3 Patch 3.
2.4.0.357 is the FCS of ISE 2.4.
Please call TAC if you want to troubleshoot with ISE 2.4 and re-open the bug.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2018 03:53 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2018 01:19 PM
Will this bug also affect if we change static identity group ?
I tried to showcase quarantine behaviour of ISE by moving and endpoint to blacklist but I did not see any CoA issued.
However it was working on 2.2 just fine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2018 01:30 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2018 03:40 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2018 02:19 PM
This issue has been escalated and Krishnan is engaging our engineering team.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2018 03:33 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2018 05:40 PM
Hsing,
I have upgraded to patch 2, but need to do some testing after I resolve my live session issue. I have a TAC case open on why I don't see live sessions. That could be affecting my CoAs as well. I am still seeing inconsistent results.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2018 10:32 AM
I'm seeing the same thing on a 2.4 patch 1 deployment today. I thought I was going crazy for a bit until I saw this thread.
I was trying to use IP address in one of my profiling policies, which was correctly changing the profile for the device after it got an IP address from DHCP but the device was stuck on my Monitor-Mode-MAB authz rule.
What I've seen today:
1. Workstation connects > Profiled as Microsoft-Workstation > Static Set Corp-Printer Policy > No CoA
2. Printer connects > Profiled as Cannon-Device > Re-Profiled as Corp-Cannon-Device > No CoA
3. Security Device Connects > Unknown Device > Profiled as Corp-Security-Device > CoA reauthorizes session
Anytime it matches an existing Cisco profile first, the re-profiling works but it doesn't respect the global profiling CoA Reauth settings. I even tried to set the CoA Reauth in the profile itself without any success.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2018 10:37 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2018 10:44 AM
Oh your right, I agree with your statement above.
It's pretty frustrating when you're expecting it to just work when doing a bunch of profiling rule build out. :)
I opened a case with TAC as the accepted answer recommends. Thankfully for troubleshooting purposes its pretty easy to replicate the issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-27-2018 01:10 AM
We see the exact same behavior. Running 2.4 patch 2 at the moment.
It's working when going from unknown to another profile policy, however when we manually import the MAC address to an endpoint group it doesn't work.
When I configure an Exception Action to force a CoA for a specific profile policy it's also working but that's not a solution you want :)
I see the bug still has the status fixed, have you heard anything from TAC about this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-27-2018 05:40 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-27-2018 07:00 AM
Yes, please do open a TAC case. And, focus on the new issue that ISE profiling CoA requests with this Cisco AVP subscriber:reauthenticate-type=last
If ISE 2.3 not including such option in the same requests, then ask TAC to file a new bug.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide