- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: How to search mac address falls under which identity groups
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2019 09:33 AM
Hi,
1) Can ISE find mac address in this format? copy out from the switch sh mac address-table
a009.ed05.4678
2)Do i need to go into "each" identity groups and search whether this mac address belongs to the grp?
OR is there a fastest way i can search if this mac- address belongs to any identity grp?
Many many thanks!!
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2019 07:27 PM
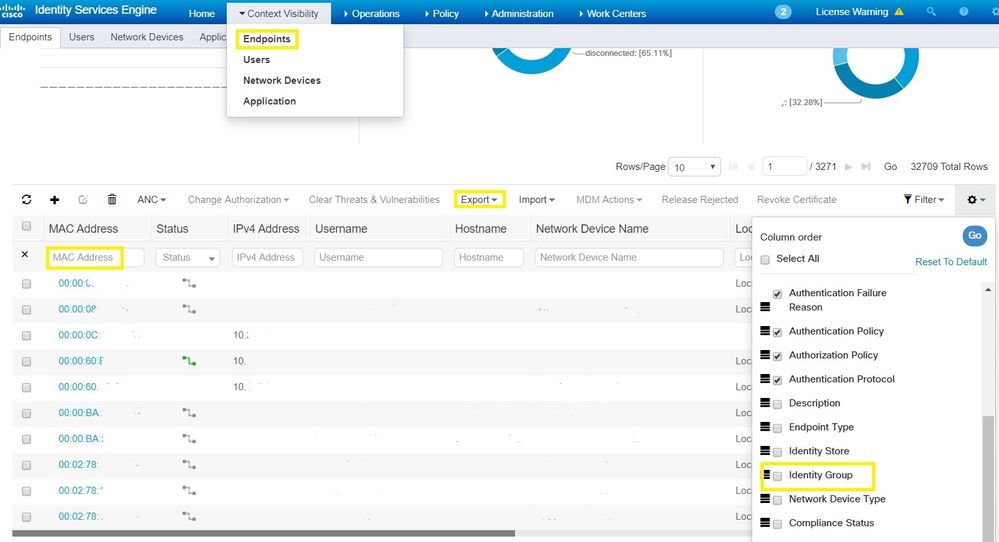
I'm a visual person so maybe this will help you, you will have to add the Identity group to the filter via the gear/menu before you can search by it.
You can also, select export > all endpoints, and the generated CSV will have the information you want. It can be quicker to do it via excel.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2019 12:43 PM
Hi,
If you go to "Context Visibility > Endpoints" you can filter on mac address, paste the mac address and it will filter (it displays the mac address in the format a0:09:ed:05:46:78, but you can use the format a009.ed05.4678 as well). Click the endpoint mac address, under the attributes tab you will see General attributes and the Identity Group assignment.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2019 07:27 PM
I'm a visual person so maybe this will help you, you will have to add the Identity group to the filter via the gear/menu before you can search by it.
You can also, select export > all endpoints, and the generated CSV will have the information you want. It can be quicker to do it via excel.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-13-2019 10:46 PM
Hi,
Many thanks for enlightening me!!!
IS it possible to knw if the particular mac-address falls under which policy? so that ISE can tell if the device is authorized or not i.e ALLOW/BLOCK.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2019 11:39 AM
The authorization policy column on the Context Visibility column shows you that information, but CV is buggy and not always the accurate source of truth for that information. The live logs or RADIUS authentication report is the source of truth what what rule the device is hitting.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: