- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE 2.1 Linux BYOD Client provisioning
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2017 03:30 AM
Hi
Please assist where to I get the client provisioning for Linux machines? I am unable to download direct from ISE. Or please assist on the configuration of this. I get device not supported on the BYOD flow.
Regards
Chris
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2017 04:30 AM
There is no posture compliance (anyconnect system scan) or BYOD flow support for linux devices.
For EAP-TLS cert auth to ISE
In ISE you can use our certificate provisioning portal to generate endpoint certificate for linux and can manually install it. There is API that can help automate as well
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2017 04:30 AM
There is no posture compliance (anyconnect system scan) or BYOD flow support for linux devices.
For EAP-TLS cert auth to ISE
In ISE you can use our certificate provisioning portal to generate endpoint certificate for linux and can manually install it. There is API that can help automate as well
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2017 04:39 AM
Thanks
But the solution is for wired so I need a way to profile the device as linux and then get the user to login via CWA bypass client provision to match AD group and provide rights as per AD group. Any way in doing this?
Regards
Chris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2017 04:54 AM
Certainly you can profile and send them to a CWA portal. However there is a chicken egg thing going on here.. If it’s a new device, unless you specify a list of mac addresses of your linux machines then we need to hit a portal to find out if it is a linux machine.
Can you explain further what you would like to do?
Step by step what is supposed to happen with the following when they first connect
linux devices
windows/apple mac
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2017 04:59 AM
My question here is if I enable under the Profiler Policy List > workstation (dell, hp and so on) NMAP what kind CPU will this add if this is enabled? Running ISE 2.1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2017 05:10 AM
This wouldn’t work because you’re trying to profile as linux workstation. What good would it do you to identify the type of Physical workstation they are using? Does a specific type of physical workstation (example HP) only run linux?? Are you running linux on multiple different type of hardware?
If these are company owned linux then you might need to somehow identify
I would suggest you learn about profiling here - https://communities.cisco.com/docs/DOC-68156
Please explain the flows you are wanting to support from the wired switch
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2017 05:14 AM
Catch all rule CWA need to be able to login with Linux machine no client provision enabled for Linux only possible or not?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2017 05:32 AM
There is this setting
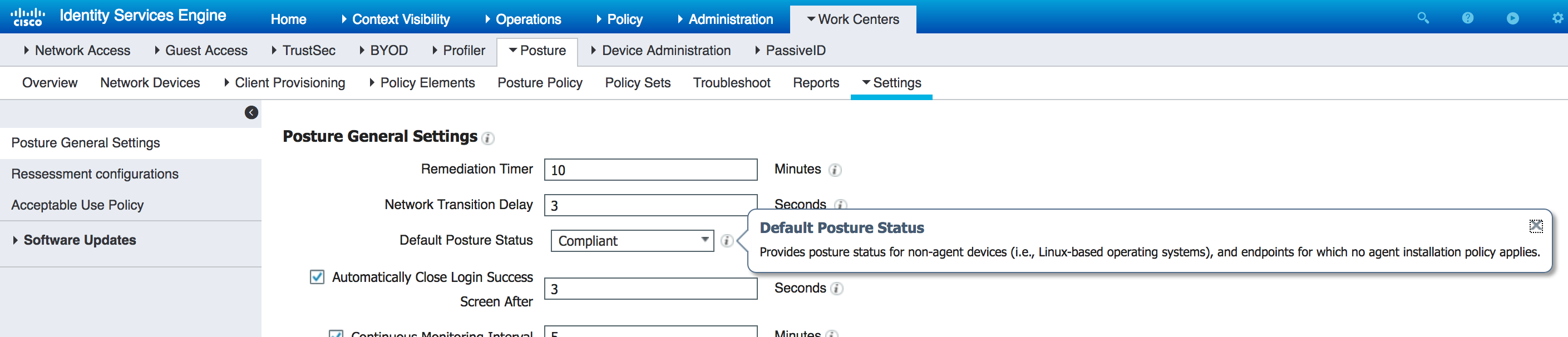
There is no way to call this out in client provisioning policy.
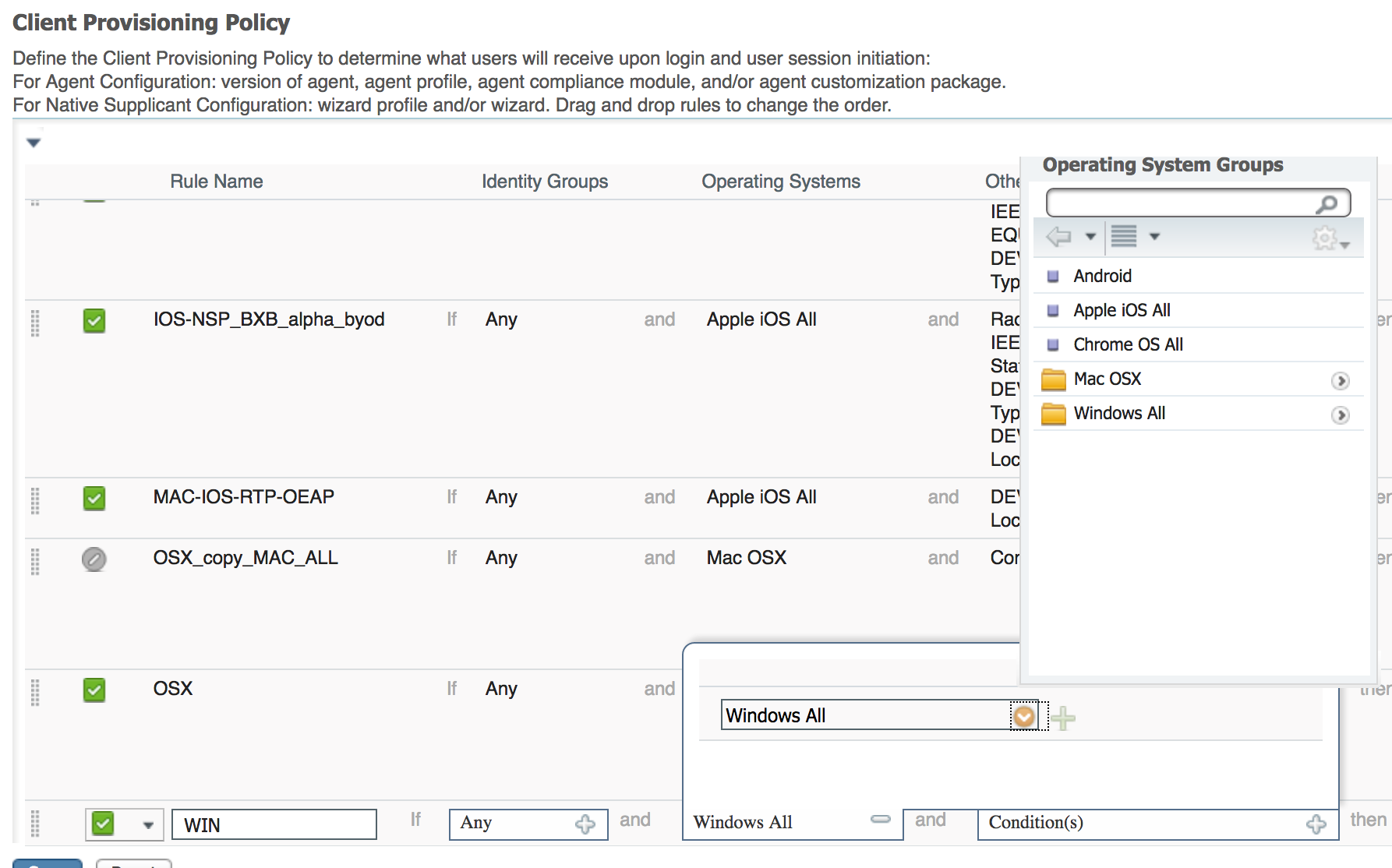
Its still not clear on your flows.. How do you want to handle other OS. Are you doing BYOD certificate provisioning or posture.. etc
You might want to call the TAC and explain this to have a detailed conversation. Or request through your sales channel to discuss with an ISE expert. From this thread you are not providing enough context on what you're wanting to do.
You could possibly do this:
if wired_mab and windows/mac and using certificate then permitWindowsMACaccess
if wired_mab and linux then PermitLinuxAccess
if wired_mab and windows/mac then BYOD
if wired_mab then redirect to CWA (when they hit the portal they will be profiled)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2017 08:30 AM
Hi Jason
See below. Network setup assistant pushed below settings with Public ROOT CA from ISE. No EAP-TLS is used in this deployment.

You have let say 10000 clients which some of them are domain user but private machines.
Only domain machines are postured checked with any connect clients and posture agent. Working on all windows machines. EAP Chain result machine and user authenticated.
Rest of machines are BYOD machines. Above native supplicant profile is used and send to Windows and MAC OX users. Tested working. User can be identified as staff or non staff and authorization profiles with rights enforced.
Now you have users how have their own machines with Linux. For them to access corparate resource you need to identify them. You send them to a portal to login (catch all mab CWA rule ) to capture their details, from here device not supported displayed on the BYOD for linux machines. The question here is how do you allow these machines on the network without any user interaction or little and how do you identify the user for this machine.
Settings already enabled as per your screen shot.
Hope this information helps or if still unclear I can add more if you need.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2017 07:39 AM
Would recommend working through TAC to debug, please update with the solution
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2017 03:40 AM
Hi Jason
What I am currently doing is the following. MAB rule with CWA then user login with AD credential to get the machine profiled as linux. I have set the Native supplicant provisioning policy Unavailable " Allow Network Access" under the Administration settings to get passed the client provision issue for Linux device not support is that is now displayed but network access is allowed. With the COA user now falls in the Wired_BYOD_Devices and combined with Authorization rules to match Linux and Wired_BYOD_Devices user is then redirected to Guest Portal with no BYOD flow. When user then authenticated against AD correct access is allocated with a DACL. This only happens once with the redirect to 2 different Portals.
MAB with CWA Guest Portal flow with BYOD
The other issue I am now faces with is below when a guest logs in.
[ 400 ] Bad Request,The request is invalid due to malformed syntax or invalid data
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2017 07:28 AM
please work through the tac sorry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2017 05:29 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2017 05:29 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

