- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE 2.3 wireless profile in AnyConnect not connecting
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2019 02:45 PM
ISE 2.3 patch 5
WLC 5520 8.5.131.0
I had my wireless profiles in AnyConnect working perfectly fine with ISE, but all of a sudden seeing this issue where AC won't complete connecting to the wireless profile. To troubleshoot I changed my authz policy on ISE from posture to allow access without posturing, my result (authorization) profile is just an airespace ACL that has a permit all. I have the same flexconnect ACL configured in the WLC and the flexconnect group ACL mapping policies has the ACL added to the list. Again this was working before and no changes have been made from what I can tell on the WLC.
I see this in the debug client on the WLC:
*Dot1x_NW_MsgTask_6: Jan 23 15:18:08.975: 40:a3:cc:f0:82:46 flex webauth acl id to be sent :5 name :dACL-Posture-Redirect client acl id : 65535
*Dot1x_NW_MsgTask_6: Jan 23 15:18:08.975: 40:a3:cc:f0:82:46 Vlan while overriding the policy = -1
*Dot1x_NW_MsgTask_6: Jan 23 15:18:08.975: 40:a3:cc:f0:82:46 sending to spamAddMobile vlanId -1 aclName = , flexAclId 65535
*Dot1x_NW_MsgTask_6: Jan 23 15:18:08.975: 40:a3:cc:f0:82:46 0.0.0.0 L2AUTHCOMPLETE (4) Plumbed mobile LWAPP rule on AP 80:e0:1d:96:28:c0 vapId 17 apVapId 6 flex-acl-name:dACL-Posture-Redirect
*Dot1x_NW_MsgTask_6: Jan 23 15:18:08.975: 40:a3:cc:f0:82:46 0.0.0.0 L2AUTHCOMPLETE (4) Change state to DHCP_REQD (7) last state L2AUTHCOMPLETE (4)
*Dot1x_NW_MsgTask_6: Jan 23 15:18:08.975: 40:a3:cc:f0:82:46 spamSendFabricClientRegistration: Not sending Registration for Fabric client 40:a3:cc: f0:82:46, primary and secondary MS IP is zero
*Dot1x_NW_MsgTask_6: Jan 23 15:18:08.975: 40:a3:cc:f0:82:46 0.0.0.0 DHCP_REQD (7) pemAdvanceState2 7006, Adding TMP rule
*spamApTask2: Jan 23 15:18:08.975: 40:a3:cc:f0:82:46 Add SGT:0 to AP 80:e0:1d:96:28:c0
*spamApTask2: Jan 23 15:18:08.975: 40:a3:cc:f0:82:46 Add CTS mobile SGT - Encoded the capwap payload for the mobile with SGT 0
*Dot1x_NW_MsgTask_6: Jan 23 15:18:08.975: 40:a3:cc:f0:82:46 0.0.0.0 DHCP_REQD (7) Adding Fast Path rule
type = Airespace AP - Learn IP address
on AP 80:e0:1d:96:28:c0, slot 0, interface = 8, QOS = 2
IPv4 ACL ID = 255, IPv
*Dot1x_NW_MsgTask_6: Jan 23 15:18:08.975: 40:a3:cc:f0:82:46 0.0.0.0 DHCP_REQD (7) Fast Path rule (contd...) 802.1P = 5, DSCP = 46, TokenID = 64206, IntfId = 0 Local Bridging Vlan = 0, Local Bridging intf id = 0
*Dot1x_NW_MsgTask_6: Jan 23 15:18:08.975: 40:a3:cc:f0:82:46 0.0.0.0 DHCP_REQD (7) Fast Path rule (contd...) AVC Ratelimit: AppID = 0 ,AppAction = 4, AppToken = 64206 AverageRate = 0, BurstRate = 0
*Dot1x_NW_MsgTask_6: Jan 23 15:18:08.975: 40:a3:cc:f0:82:46 0.0.0.0 DHCP_REQD (7) Fast Path rule (contd...) AVC Ratelimit: AppID = 0 ,AppAction = 4, AppToken = 64206 AverageRate = 0, BurstRate = 0
*Dot1x_NW_MsgTask_6: Jan 23 15:18:08.975: 40:a3:cc:f0:82:46 0.0.0.0 DHCP_REQD (7) Fast Path rule (contd...) AVC Ratelimit: AppID = 0 ,AppAction = 4, AppToken = 64206 AverageRate = 0, BurstRate = 0
*Dot1x_NW_MsgTask_6: Jan 23 15:18:08.975: 40:a3:cc:f0:82:46 0.0.0.0 DHCP_REQD (7) Successfully plumbed mobile rule (IPv4 ACL ID 255, IPv6 ACL ID 255, L2 ACL ID 255,URL ACL ID 255,URL ACL Action 0)
*spamApTask2: Jan 23 15:18:08.975: 40:a3:cc:f0:82:46 Successful transmission of LWAPP Add-Mobile to AP 80:e0:1d:96:28:c0
*Dot1x_NW_MsgTask_6: Jan 23 15:18:08.975: 40:a3:cc:f0:82:46 0.0.0.0 DHCP_REQD (7) NO release MSCB
*Dot1x_NW_MsgTask_6: Jan 23 15:18:08.975: 40:a3:cc:f0:82:46 Successfully Plumbed PTK session Keysfor mobile 40:a3:cc:f0:82:46
*pemReceiveTask: Jan 23 15:18:08.975: 40:a3:cc:f0:82:46 0.0.0.0 Added NPU entry of type 9, dtlFlags 0x0
*spamApTask2: Jan 23 15:18:08.995: 40:a3:cc:f0:82:46 Received DELETE mobile, reasonCode MN_CLIENT_ACL_MISMATCH, deleteReason 15 from AP 80:e0:1d:96:28:c0, slot 0 ...cleaning up mscb
*spamApTask2: Jan 23 15:18:08.995: 40:a3:cc:f0:82:46 Succesfully freed AID 3, slot 0 on AP 80:e0:1d:96:28:c0, #client on this slot 5
*spamApTask2: Jan 23 15:18:08.995: 40:a3:cc:f0:82:46 Scheduling deletion of Mobile Station: (callerId: 30) in 1 seconds
*apfOpenDtlSocket: Jan 23 15:18:09.182: 40:a3:cc:f0:82:46 Recevied management frame ASSOCIATION REQUEST on BSSID 80:e0:1d:96:28:ca destination addr 80:e0:1d:96:28:ca
*apfMsConnTask_3: Jan 23 15:18:09.182: 40:a3:cc:f0:82:46 Processing assoc-req station:40:a3:cc:f0:82:46 AP:80:e0:1d:96:28:c0-01 ssid : CORPORATE-WIFI thread:217a0660
*apfMsConnTask_3: Jan 23 15:18:09.182: 40:a3:cc:f0:82:46 Ignoring 802.11 assoc request from mobile pending deletion
*apfMsConnTask_3: Jan 23 15:18:09.182: 40:a3:cc:f0:82:46 Sending assoc-resp with status 12 station:40:a3:cc:f0:82:46 AP:80:e0:1d:96:28:c0-00 on apVapId 6
*apfMsConnTask_3: Jan 23 15:18:09.182: 40:a3:cc:f0:82:46 Sending Assoc Response (status: 'Assoc denied unspecified') to station on AP TEST-AP on BSSID 80:e0:1d:96:28:ca ApVapId 6 Slot 1, mobility role 0
What does MN_CLIENT_ACL_MISMATCH mean?
Anyway if I change the authz policy result profile to the default "PermitAccess" 'i have no issues connecting to the wireless profile.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2019 02:20 PM - edited 01-29-2019 02:21 PM
I was able to resolve the issue, it looks like buggy behaviour on the WLC.
If I used the default "PermitAccess" result in my authz policy, no wirespace acl is used and it works. If I use a result which has a wirespace acl defined connecting to wireless fails. Even though the flexconnect acl is present and configured on the WLC. I removed the flexconnect group mapping policy ACL and reapplied the same ACL and it works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2019 03:25 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2019 04:47 PM
Hi Damien,
I was pushing down a posture ACL, but then set up a new simple authz policy that pushed a permit all acl for testing. I found the same issue and same messages in the debug client output. sorry I only have the debug output from when I tested the posture acl at this time. authentication is configured for eap-tls. On ISE side Radius live logs shows the correct authz policy being hit by the client, but then I also see a Dynamic Authorization failed event pop up in the live logs:
Event 5417 Dynamic Authorization failed
Error-Cause Session Context Not Found
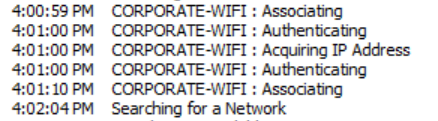
On AC it never finishes connecting to the wireless goes into loop like this:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2019 02:20 PM - edited 01-29-2019 02:21 PM
I was able to resolve the issue, it looks like buggy behaviour on the WLC.
If I used the default "PermitAccess" result in my authz policy, no wirespace acl is used and it works. If I use a result which has a wirespace acl defined connecting to wireless fails. Even though the flexconnect acl is present and configured on the WLC. I removed the flexconnect group mapping policy ACL and reapplied the same ACL and it works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2019 02:22 PM
I recall older version of AireOS required regular ACL with same name as FlexACL in existence on the WLC. The regular ACL didn't need any entries, just having it present with exact same name would be enough. Other possibility is to confirm whether the Flex AP actually has the policy ACL downloaded when part of the group or temporarily testing with single AP with FlexACL pushed to it for testing as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2019 03:00 PM
Hi Hosuk,
Yes that is correct for older AireOS version. I was able to work with TAC and they found the issue to be CSCvi85464. If the AP reloads then it loses the flexconnect acl config, so it has to be reapplied to the AP.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide