- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE 2.4 + IOS-XE 16.3.6 // ISE approves exec authorization for local users via console?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2018 05:12 PM
Questions/concerns
- Console authentication is correctly using the CON method list, but console authorization is using the VTY method list even though authorization exec CON is configured on line console 0; see config details below.
- When logging into console using a local credential whose username is the same an AD user's account (but with a different password), the authorization is sent to ISE (erraneously?) and passes authorization.
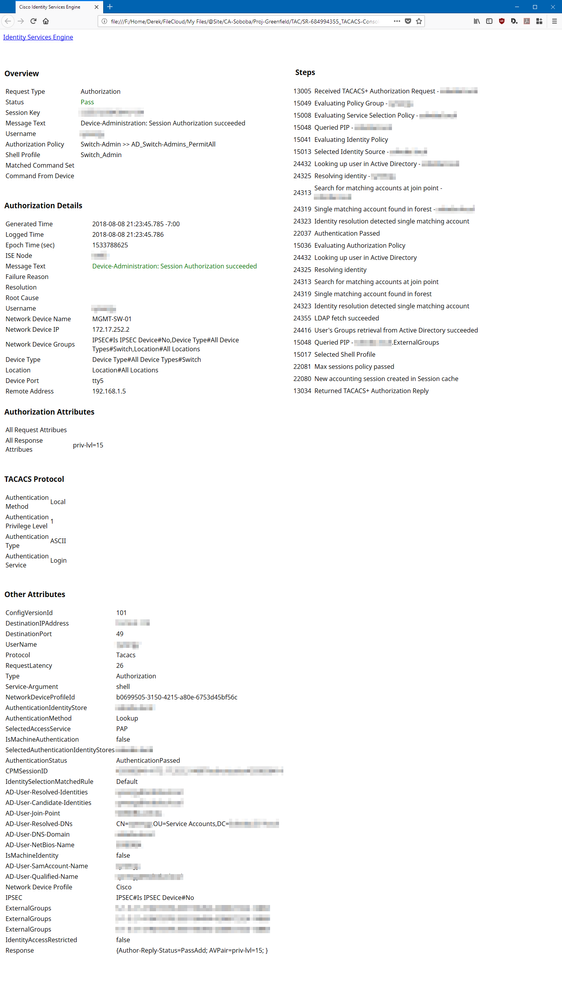
Is the account and password required for ISE to authorize exec, or only the account name? In the debug and screenshots hidden in the spoiler(s) below, I see that the ISE authorization log is listing the authentication method as Local. does that mean ISE does not need to verify the password against the AD user its referencing?
Config Details
- VTY lines should use the VTY method lists for authentication and authorization.
- Console line should use the CON method lists for authentication and authorization.
line console 0
authorization exec CON
login authentication CON
line vty 0 15 authorization exec VTY login authentication VTY
- AAA authentication and authorization method lists.
aaa authentication login CON local aaa authentication login VTY group ISE-TACACS local
aaa authorization console aaa authorization exec CON local if-authenticated aaa authorization exec VTY group ISE-TACACS local if-authenticated
- TACACS server group.
aaa group server tacacs+ ISE-TACACS server-private 10.0.0.1 single-connection key server-private 10.0.0.2 single-connection key server-private 10.0.0.3 single-connection key
- ISE Device Admin Policy Set.
Credential in external AD Group 'Switch-Admins';
derek -- tacacspassword
Local switch credentials;
username admin privilege 15 secret 0 localpassword username derek privilege 15 secret 0 localpassword
Observed Behavior
- When logging in through SSH with AD account: derek -- tacacspassword
- authentication uses the VTY method list, result: PASS.
- authorization uses the VTY method list, result: PASS.
- Debug...
Spoiler
AAA/BIND(00001FD5): Bind i/f AAA/AUTHEN/LOGIN (00001FD5): Pick method list 'VTY' TPLUS: Queuing AAA Authentication request 8149 for processing TPLUS(00001FD5) login timer started 1020 sec timeout TPLUS: processing authentication start request id 8149 TPLUS: Authentication start packet created for 8149(derek) TPLUS: Using server 10.0.0.1 TPLUS(00001FD5)/0/NB_WAIT/FFA3D590E8: Started 5 sec timeout TPLUS(00001FD5)/0/NB_WAIT: wrote entire 46 bytes request TPLUS(00001FD5)/0/READ: read entire 12 header bytes (expect 15 bytes) TPLUS(00001FD5)/0/READ: read entire 27 bytes response TPLUS(00001FD5)/0/FFA3D590E8: Processing the reply packet TPLUS: Received authen response status GET_PASSWORD (8) TPLUS: Queuing AAA Authentication request 8149 for processing TPLUS(00001FD5) login timer started 1020 sec timeout TPLUS: processing authentication continue request id 8149 TPLUS: Authentication continue packet generated for 8149 TPLUS(00001FD5)/0/WRITE/FFA3D590E8: Started 5 sec timeout TPLUS(00001FD5)/0/WRITE: wrote entire 26 bytes request TPLUS(00001FD5)/0/READ: read entire 12 header bytes (expect 6 bytes) TPLUS(00001FD5)/0/READ: read entire 18 bytes response TPLUS(00001FD5)/0/FFA3D590E8: Processing the reply packet TPLUS: Received authen response status PASS (2) AAA/AUTHOR (0x1FD5): Pick method list 'VTY' TPLUS: Queuing AAA Authorization request 8149 for processing TPLUS(00001FD5) login timer started 1020 sec timeout TPLUS: processing authorization request id 8149 TPLUS: Protocol set to None .....Skipping TPLUS: Sending AV service=shell TPLUS: Sending AV cmd* TPLUS: Authorization request created for 8149(derek) TPLUS: using previously set server 10.0.0.1 from group ISE-TACACS TPLUS(00001FD5)/0/NB_WAIT/FFA74A7E08: Started 5 sec timeout TPLUS(00001FD5)/0/NB_WAIT: wrote entire 65 bytes request TPLUS(00001FD5)/0/READ: read entire 12 header bytes (expect 18 bytes) TPLUS(00001FD5)/0/READ: read entire 30 bytes response TPLUS(00001FD5)/0/FFA74A7E08: Processing the reply packet TPLUS: Processed AV priv-lvl=15 TPLUS: received authorization response for 8149: PASS
- When logging in through console with local account: admin -- localpassword
- authentication uses the CON method list, result: PASS (not debugged)
- !!! authorization uses the VTY method list. !!!, result: FAIL
- Debug...
Spoiler
AAA/BIND(00001FD2): Bind i/f AAA/AUTHEN/LOGIN (00001FD2): Pick method list 'CON' AAA/AUTHOR (0x1FD2): Pick method list 'VTY' TPLUS: Queuing AAA Authorization request 8146 for processing TPLUS(00001FD2) login timer started 1020 sec timeout TPLUS: processing authorization request id 8146 TPLUS: Protocol set to None .....Skipping TPLUS: Sending AV service=shell TPLUS: Sending AV cmd* TPLUS: Authorization request created for 8146(admin) TPLUS: Using server 10.0.0.1 TPLUS(00001FD2)/0/NB_WAIT/FF9D4FC748: Started 5 sec timeout TPLUS(00001FD2)/0/NB_WAIT: wrote entire 58 bytes request TPLUS(00001FD2)/0/READ: read entire 12 header bytes (expect 6 bytes) TPLUS(00001FD2)/0/READ: read entire 18 bytes response TPLUS(00001FD2)/0/FF9D4FC748: Processing the reply packet TPLUS: received authorization response for 8146: FAIL AAA/AUTHOR/EXEC(00001FD2): Authorization FAILED
- Here's where things get interesting for me, when logging in through console with local account: derek -- localpassword
- authentication uses the CON method list, result: PASS (not debugged)
- !!! authorization uses the VTY method list !!!... , result: PASS
- Debug and ISE authorization screenshot...
Spoiler
AAA/BIND(00001FD4): Bind i/f AAA/AUTHEN/LOGIN (00001FD4): Pick method list 'CON' AAA/AUTHOR (0x1FD4): Pick method list 'VTY' TPLUS: Queuing AAA Authorization request 8148 for processing TPLUS(00001FD4) login timer started 1020 sec timeout TPLUS: processing authorization request id 8148 TPLUS: Protocol set to None .....Skipping TPLUS: Sending AV service=shell TPLUS: Sending AV cmd* TPLUS: Authorization request created for 8148(derek) TPLUS: Using server 10.18.2.113 TPLUS(00001FD4)/0/NB_WAIT/FF9D4FC748: Started 5 sec timeout TPLUS(00001FD4)/0/NB_WAIT: wrote entire 61 bytes request TPLUS(00001FD4)/0/READ: read entire 12 header bytes (expect 18 bytes) TPLUS(00001FD4)/0/READ: read entire 30 bytes response TPLUS(00001FD4)/0/FF9D4FC748: Processing the reply packet TPLUS: Processed AV priv-lvl=15 TPLUS: received authorization response for 8148: PASS
I see that the ISE authorization log is listing the authentication method as Local, does that mean ISE does not need to verify the password against the AD user its referencing?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2018 10:08 AM - edited 08-10-2018 01:50 PM
@Nidhi wrote:
ISE will not validate password in Authorization policy.
@Nidhi wrote:
ISE is validating the user against this group
These two statements satisfy my curiosity.
So the switch is authenticating the user, and then passing the authorization request to ISE; ISE then validates the username only against the authorization profile and responds accordingly.
That being said, I have adjusted our configuration to achieve the following (validated via debugs);
- Console connections use the CON method list to authenticate and the default method list to authorize against local switch user(s) privileges.
- SSH connections use the default method list to authenticate and authorize against ISE/TACACS policies.
- The default authorization method list includes local and the ISE-TACACS group; the users authorize to whichever credential/method they authenticated with.
New Config
line con 0
exec-timeout 15 0
logging synchronous
login authentication CON
line vty 0 15
exec-timeout 30 0
logging synchronous
transport input ssh ! aaa authentication login CON local aaa authentication login default group ISE-TACACS local aaa authorization console aaa authorization exec default local group ISE-TACACS if-authenticated
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2018 09:07 PM
If the password type is set to internal users , ISE will not validate it with AD user.
you will have to change the password type filed for this user to the specific AD or use AD join points.
Let me know if this helps.
Thanks
Nidhi
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2018 09:12 PM - edited 08-09-2018 09:22 PM
Nidhi - thank you for your response, however I am not having issues authenticating the external AD user.
Plain english example;
Engineer connected to the console port is prompted to log in and does so using local switch credentials. Switch authenticates the credential against the local user database, switch then sends the authorization request to ISE, which ISE is approving; i.e. passing.
When we look at the ISE authorization log, we see that ISE authorized the user against the AD user of the same name... the local switch username and the AD account do not have the same password.
The question/concern is whether or not this is expected behavior... Does ISE validate the password during the authorization request, or just look to see if the AD user is in the AD group referenced by the authorization policy?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2018 08:35 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2018 08:37 AM
Unless you're looking for something else, I put a screenshot of the authorization policy in my original post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2018 08:48 AM
Apologize missed that.
I see that you are referencing the external group in the authorization policy condition. ISE is validating the user against this group. please check the ad_agent.log to verify.
Thanks,
Nidhi.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2018 10:08 AM - edited 08-10-2018 01:50 PM
@Nidhi wrote:
ISE will not validate password in Authorization policy.
@Nidhi wrote:
ISE is validating the user against this group
These two statements satisfy my curiosity.
So the switch is authenticating the user, and then passing the authorization request to ISE; ISE then validates the username only against the authorization profile and responds accordingly.
That being said, I have adjusted our configuration to achieve the following (validated via debugs);
- Console connections use the CON method list to authenticate and the default method list to authorize against local switch user(s) privileges.
- SSH connections use the default method list to authenticate and authorize against ISE/TACACS policies.
- The default authorization method list includes local and the ISE-TACACS group; the users authorize to whichever credential/method they authenticated with.
New Config
line con 0
exec-timeout 15 0
logging synchronous
login authentication CON
line vty 0 15
exec-timeout 30 0
logging synchronous
transport input ssh ! aaa authentication login CON local aaa authentication login default group ISE-TACACS local aaa authorization console aaa authorization exec default local group ISE-TACACS if-authenticated
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: