- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE Authorization Policy
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2016 11:13 AM
Hi guys,
I try to understand something about Authorization Policy and implement it on my Lab
I have Lab environment in GNS3 that I connect to physical switch c3750,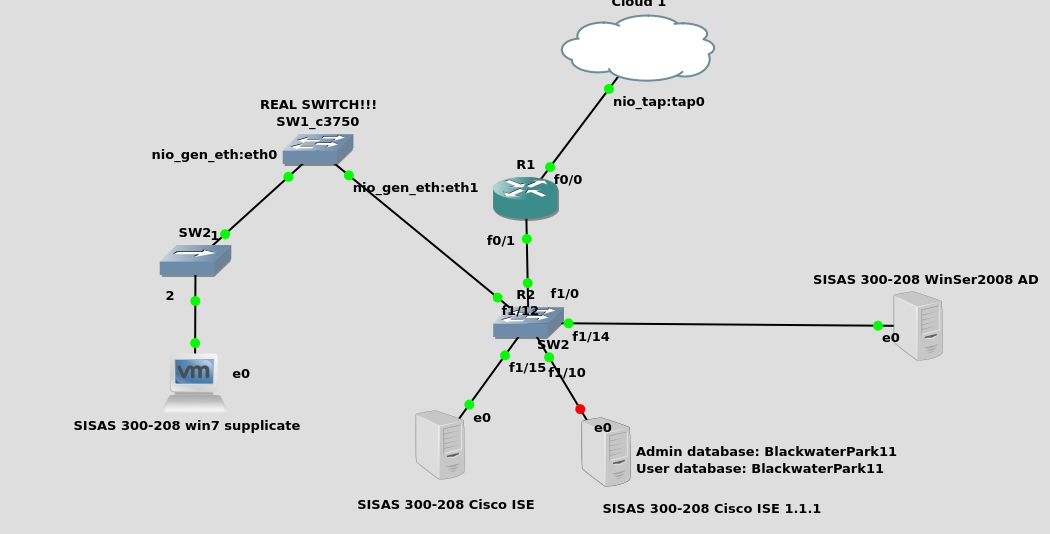
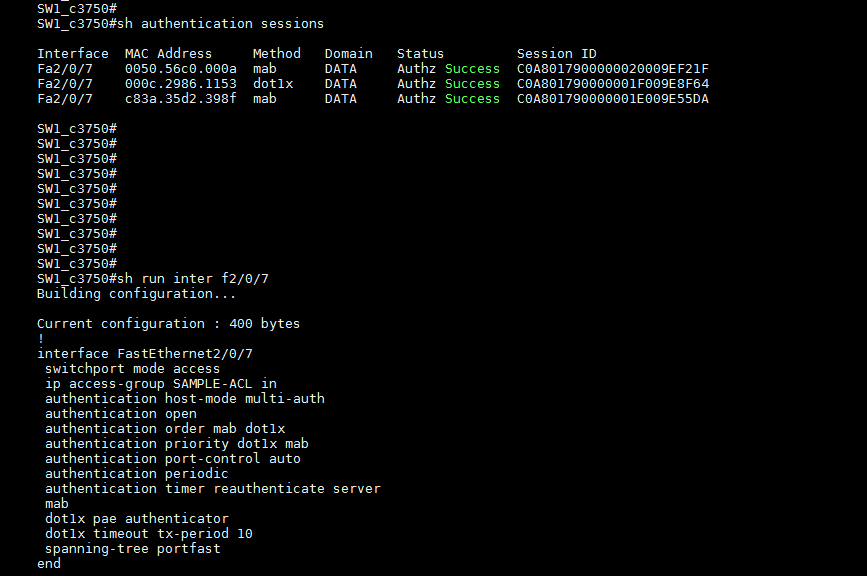
On that switch I setup the port Fa2/0/7 as follow:
interface FastEthernet2/0/7
switchport mode access
ip access-group SAMPLE-ACL in
authentication host-mode multi-auth
authentication open
authentication order mab dot1x
authentication priority dot1x mab
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
mab
dot1x pae authenticator
dot1x timeout tx-period 10
spanning-tree portfast
end
And the ACL is:
Extended IP access list SAMPLE-ACL
10 deny icmp any host 8.8.8.8
20 permit ip any any (74 matches)
In the Authorization Policy I try to implement policy that accept Wired MAB and base on the MAC implement some ACL that permit 8.8.8.8
It doesn't work and the switch doesn't get my ACL...:\
On Policy Element>Authorization Profiles, I add a new Authorization Profile named "Our_Author_profile" and in the Access Type I selected ACCESS_ACCEPT and in Common Tasks >DACL name I selected the PERMIT_ALL_TRAFFIC and save the change.
On "Policy>Authorization>Authorization Policy I add a new rule named "MAC and AD users Auth" in the conditions I setup the follow:
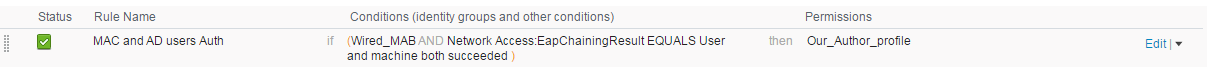
On the the port Fa2/0/7 I get 3 MAC's, 1-for the win7 PC and more two (that arrived from my virtual interfaces that I make on my machine [linux])
how can I force the ISE to implement the DACL on port 2/0/7?
Why it doesn't work for me?
The authorization success on the port but the ACL doesn't implement on my switch.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2016 03:25 AM
Hi guys!
Big thanks so much!!
I had some rule (policy>authorization) that was before my rule named "Basic_Authentication_Access" with "PermitAccess" and my device authorize by that rule and not my the rule that I make:
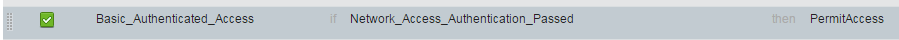
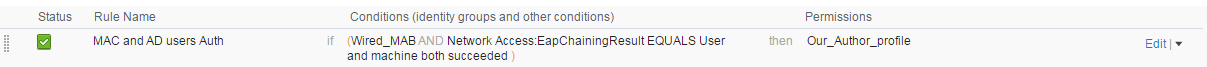
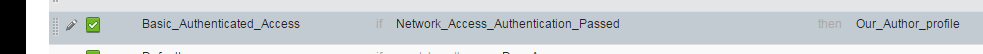
So I delete my rule and on the "Basic_Authentication_Access" I change the Permissions to "Out_Author_profile" that apply DACL (PERMIT_ALL_TRAFFIC),
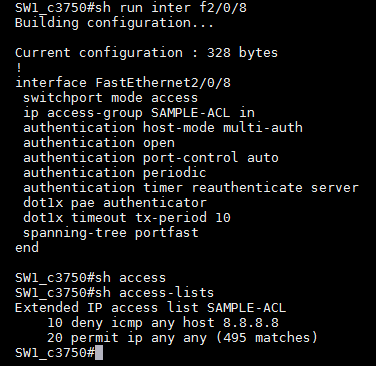
On my switch (c3750) I apply some ACL that reject ICMP to 8.8.8.8 on the interface 2/0/8,
And at the time I have some ping test to 8.8.8.8 (which failed because of the SAMPLE-ACL that reject it) and I reconnect to the network using native supplicate with the user "bob", and as I succeeded to authenticate the switch get my dACL and the ping test was succeeded!:]
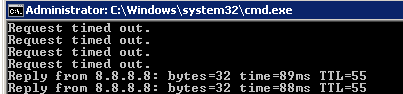
And now at-lest I can see the applying ACL!!:]
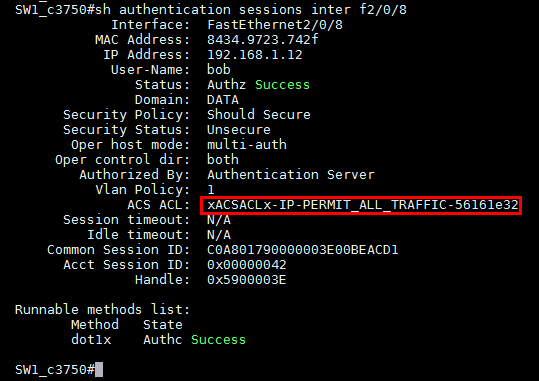
Cheers!!!:]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2016 11:27 AM
Guy, the dACL feature doesn't replace the ACL that was applied to the interface via 'ip access-group' command. In other words the interface command will stay the same post dACL. The dACL is prepended above the interface ACL dynamically without changing the configuration. To see the resultant ACL on the interface you have to run 'show ip access-list interface fastethernet 2/0/7' command. I suggest reviewing following document regarding ACL application on Cisco IOS switches:
802.1x DACL, Per-User ACL, Filter-ID, and Device Tracking Behavior - Cisco
Also, make sure you have all the commands applied referenced in the how-to guide:
How To: Universal IOS Switch Config for ISE
Hosuk
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2016 02:25 PM
Hi Hosuk,
Thanks for reply
I can't see any ACL that I tried to apply via the comman 'show ip access-list interface fastethernet 2/0/7'
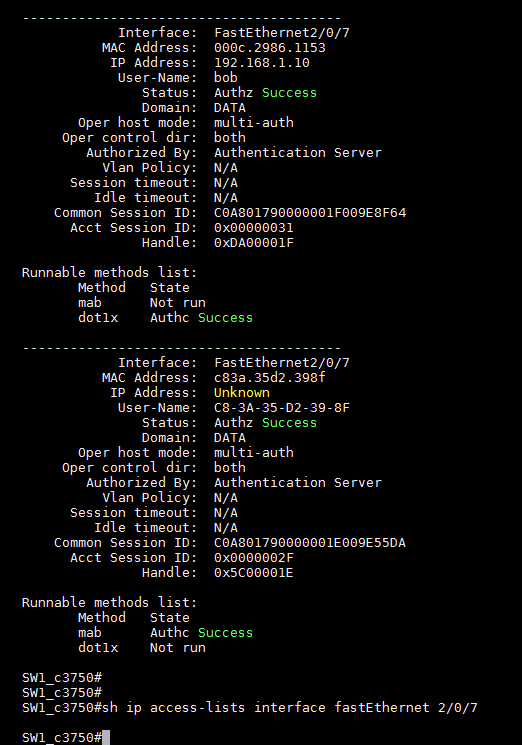
I started to read your document! and it's look great!!:]
Thanks again:]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2016 09:41 AM
I setup again DACL, and the results are the same, the ACL doesn't implemented on my switch..
What I missed?
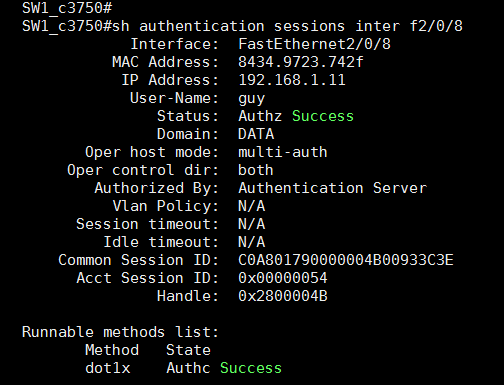
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2016 12:12 PM
Is ip device tracking configured? If yes can you see anything with show ip device tracking all
You could try to add the epm logging command that give you some dACL related messages.
And also debug epm for more info.
And if the ACL syntax is wrong the switch will ignore it, but you probably verified it in ISE (a bigger problem before ![]() )
)
Quick edit: See Hosuk's link Universal Switch Config. If I remember right, there are some information about epm logging there
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2016 12:35 PM
Couple things you can try:
- Check the syntax of the ACL on ISE using the built-in syntax tool. Switches won't accept the ACL if it is not created properly.
- Make sure your AAA configuration on the switch is correct. If you are missing part of the configuration, the switch could perform authentication but not the authorization. Hosuk provided the URL for the Universal Switch Guide.
Regards,
-Tim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2016 03:25 AM
Hi guys!
Big thanks so much!!
I had some rule (policy>authorization) that was before my rule named "Basic_Authentication_Access" with "PermitAccess" and my device authorize by that rule and not my the rule that I make:


So I delete my rule and on the "Basic_Authentication_Access" I change the Permissions to "Out_Author_profile" that apply DACL (PERMIT_ALL_TRAFFIC),

On my switch (c3750) I apply some ACL that reject ICMP to 8.8.8.8 on the interface 2/0/8,

And at the time I have some ping test to 8.8.8.8 (which failed because of the SAMPLE-ACL that reject it) and I reconnect to the network using native supplicate with the user "bob", and as I succeeded to authenticate the switch get my dACL and the ping test was succeeded!:]

And now at-lest I can see the applying ACL!!:]

Cheers!!!:]
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

