- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE Interface Alias and EAP Cert
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2017 02:28 PM
Hello,
I fully understand how ISE interface alias works for Portal services on non-Eth0. My question is regarding EAP Cert using Public CA. I will use the following scenario:
ISE hostname = ise1.company.local
EAP SAN = ise1-aaa.company.com
Interface = Eth1
Would an interface alias be required on ISE in addition to the DNS record of ise1-aaa.company.com, as the EAP certificate would be public signed? Or is the DNS record of ise1-aaa.company.com only what is required?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2017 03:27 PM
EAP server certificates do not need interface aliases.
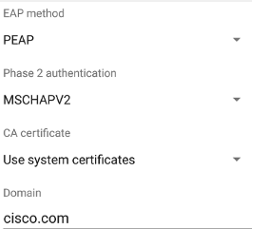
However, Windows client OS has an option to match the RADIUS server names in "Connect to these servers" and recent Android client OS needs to fill in the domain name (see below).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2017 03:27 PM
EAP server certificates do not need interface aliases.
However, Windows client OS has an option to match the RADIUS server names in "Connect to these servers" and recent Android client OS needs to fill in the domain name (see below).

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2017 06:49 PM
hslai,
Thanks for responding. I know about the option in Windows OS, but wouldn't that have to be the PSN FQDN (hostname) or IP addresses and not the SAN such ise1-aaa.company.com? Would I have to specify radius server names or won't it work without specifying any names?
To paint the picture clearer, I have the following setup and requirements:
1. Internal Domain - xyz.local
2. Company domain - company.com
3. Internal Root CA available for only xyz.local but not for company.com.
4. Use Public CA for EAP and Portal Service (Posture only). The Public cert would be Single UC-Multi-Domain
5. Use Internal CA for Admin only - Eth0. Each ISE node would have its Admin Cert
6. Eth1 for others - EAP and Posture
7. There is split-DNS for company.com
My thought process is follows:
1. Setup ISE cluster with company.com domain hostnames
2. Generate Admin CSR with CN as ise.company.com but put SANs as ise.xyz.local and also ise.company.com
3. Generate Single cert on any ISE node and sign with public CA with multiple SANs pan1.company.com, psn1.company.com and import into all ISE nodes with private key.
4. Eth0 would be for Admin and Eth1 would be for Radius. Both interfaces would be on the same subnet.
5. Use Interface Alias (Eth1) because of Posture redirection
Is my proposed setup correct?
Thanks again for the earlier response.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2017 08:01 PM
Configure Wireless Clients running Windows 7 and Windows Vista for PEAP-TLS Authentication
says,
...
To specify which Remote Authentication Dial-In User Service (RADIUS) servers your wired access clients must use for authentication and authorization, in Connect to these servers , type then name of each RADIUS server, exactly as it appears in the subject field of the server certificate. Use semicolons to specify multiple RADIUS server names.
...
This is optional.
Since your ETH0 and 1 on the same subnet, please ensure routing correctly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2017 08:15 PM
Thanks again. But please could you confirm if my earlier proposed setup is OK? Also not sure what you mean by
"Since your ETH0 and 1 on the same subnet, please ensure routing correctly".
Obviously the NADs would be configured IP address of Eth1 as the Radius Server and the IGP would get the packets to the destination. In the past, in a previous place I worked, I had Eth0 and Eth1 on the same subnet for a Guest PSN in the DMZ and no issues with Guest Redirection on Eth1 and Interface Alias on the Guest PSN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2017 08:39 PM
Well. The routing, if not taken care of, could be like this:
NAD -> ISE:ETH1 -> ISE:ETH0 -> NAD.
Your proposal looks fine for EAP. Best to test it yourself (in a lab), nonetheless.
Note: CPP and Admin certificate different but on same interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2017 06:59 AM
I would also ask why are you trying to use another interface for EAP Authentication? I prefer to keep my ISE deployments as simple as possible and use only 1 interface on my ISE nodes unless the customer has a guest portal situation requiring the PSNs to have a presence in a DMZ.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: