- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE - Looking for Multiple Users Logged into the Same Machine
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2019 04:35 PM
We currently have ISE installed in a primarily Apple MAC environment. And we have cases where 2 users will log into the same machine - a user where switch sessions so another can take their place.
We log everything ise-related in Splunk. And I'm hoping to capture these events. But I'm unsure what fields to look for to make this a success.
Help is appreciated.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2019 05:31 PM
Hi @TitanAE
I don't have Splunk, but I have the poor man's equivalent ... rsyslog :-p
below is the rsyslog formatted output from ISE when I perform a Windows User Authentication. I don't think Apple has the equivalent of this network authentication event (although you might correct me if I am wrong). As far as I know, when MACOS boots up and connects to the WiFi, it does so at a machine level. And when you switch users, there is no network authentication event that happens as a result. This is only done (AFAIK) in Windows.
Below is what I see when I log into my Windows (using EAP-TLS)
Nov 1 10:09:04 ise01 CISE_Passed_Authentications 0000724329 7 3 AuthorizationPolicyMatchedRule=IPTel Domain Joined Asset, EapAuthentication=EAP-TLS, Serial Number=3C 00 00 03 E4 62 5F D0 9E A4 20 2F 3B 00 00 00 00 03 E4, Subject - Common Name=Arne Bier, Subject Alternative Name=XXXXXX@XXXXXXXXXXXXX, Subject A lternative Name=XXXXXXXXXXXXXXXXXXXX, Subject - Email=XXXXXXXXXXXXXXXXXX, CPMSessionID=4400A8C00001CD1923B9C2F4, EndPointMACAddress=D4-3B-04-CF-B5-3E, PostureAssessmentStatus=NotApplicable, EndPointMatchedProfile=Windows10-Workstation, ISEPolicySetName=IPTEL WIRELESS 802.1X, IdentitySelectionMatchedRule=IPTEL EAP-TLS, AD-User-Resolved-Identities=XXXXXXXXXXXXXXXXXXXX, AD-User-Join-Point=XXXXXXX, StepData=4= DEVICE.Device Type, StepData=44=certificate for Arne Bier, StepData=61= Network Access.EapAuthentication, StepData=68= Session.ANCPolicy, StepData=69= Network Access.EapAuthentication, StepData=70=IPTE L_AD, StepData=71=XXXXXXXXXXXXXXXXXXXX,
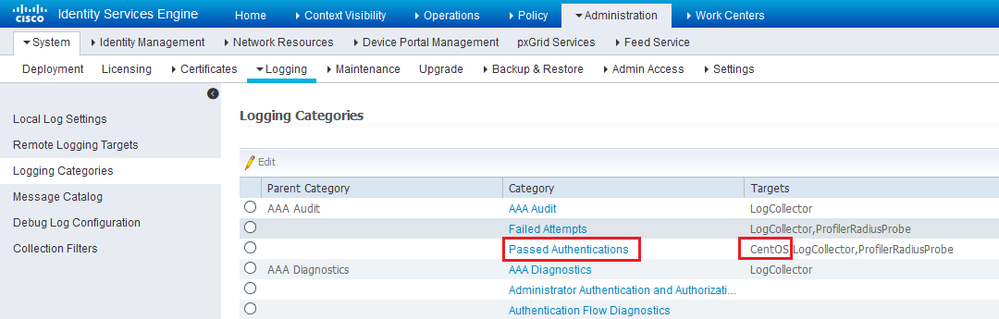
I enabled "Passed Authentications" logging category to spit out the SYSLOG to my CentOS server
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2019 05:31 PM
Hi @TitanAE
I don't have Splunk, but I have the poor man's equivalent ... rsyslog :-p
below is the rsyslog formatted output from ISE when I perform a Windows User Authentication. I don't think Apple has the equivalent of this network authentication event (although you might correct me if I am wrong). As far as I know, when MACOS boots up and connects to the WiFi, it does so at a machine level. And when you switch users, there is no network authentication event that happens as a result. This is only done (AFAIK) in Windows.
Below is what I see when I log into my Windows (using EAP-TLS)
Nov 1 10:09:04 ise01 CISE_Passed_Authentications 0000724329 7 3 AuthorizationPolicyMatchedRule=IPTel Domain Joined Asset, EapAuthentication=EAP-TLS, Serial Number=3C 00 00 03 E4 62 5F D0 9E A4 20 2F 3B 00 00 00 00 03 E4, Subject - Common Name=Arne Bier, Subject Alternative Name=XXXXXX@XXXXXXXXXXXXX, Subject A lternative Name=XXXXXXXXXXXXXXXXXXXX, Subject - Email=XXXXXXXXXXXXXXXXXX, CPMSessionID=4400A8C00001CD1923B9C2F4, EndPointMACAddress=D4-3B-04-CF-B5-3E, PostureAssessmentStatus=NotApplicable, EndPointMatchedProfile=Windows10-Workstation, ISEPolicySetName=IPTEL WIRELESS 802.1X, IdentitySelectionMatchedRule=IPTEL EAP-TLS, AD-User-Resolved-Identities=XXXXXXXXXXXXXXXXXXXX, AD-User-Join-Point=XXXXXXX, StepData=4= DEVICE.Device Type, StepData=44=certificate for Arne Bier, StepData=61= Network Access.EapAuthentication, StepData=68= Session.ANCPolicy, StepData=69= Network Access.EapAuthentication, StepData=70=IPTE L_AD, StepData=71=XXXXXXXXXXXXXXXXXXXX,
I enabled "Passed Authentications" logging category to spit out the SYSLOG to my CentOS server
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide