- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Microsoft RRAS + ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-27-2018 01:56 PM - edited 09-27-2018 01:59 PM
I'm trying to get RRAS to use ISE instead of NPS for VPN authentication. When I define the ISE server as the radius host in RRAS, the VPN connection won't come up on the client.
The ISE logs show the following:
Ensure that the ISE server certificate is trusted by the client, by configuring the supplicant with the CA certificate that signed the ISE server certificate. It is strongly recommended to not disable the server certificate validation on the client!
The ISE certificate is issued by Digicert and the intermediate and root certs are both in the cert store on the client.
Any guidance on getting RRAS and ISE to work together?
Thanks.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-01-2018 06:37 AM - edited 10-01-2018 06:38 AM
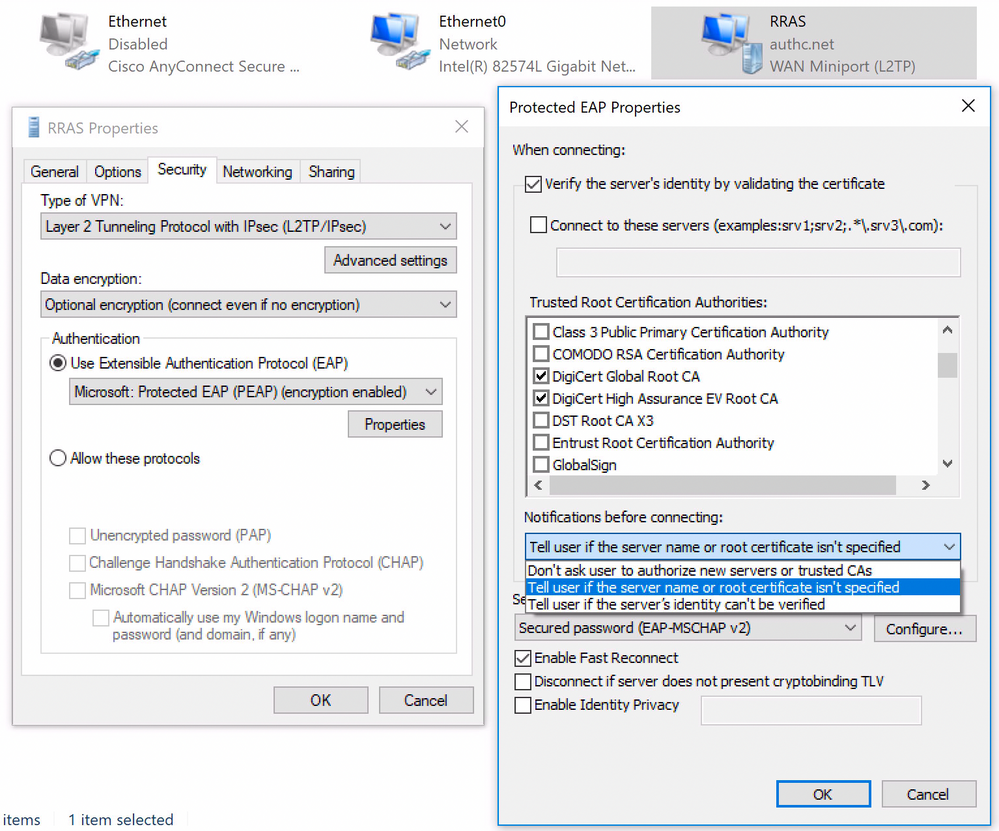
Some screenshot of the settings and additional information about the setup would help. But, since you are getting that error, I assume the RRAS and the client is using PPP-EAP, and either PEAP or EAP-TTLS EAP type. Having the Digicert root/intermediate in the client certificate store is not enough. You need to make sure the client authentication setting for VPN is configured to trust the Digicert root certificate for EAP purpose. You can do so by logging on to client Windows machine and go to its Network Connections. Find the VPN connection and click on its properties -> Security tab. Then under ‘Authentication’ click Properties and make sure the proper root CA is checked and the server names rule works with the ISE certificate. Showing here is example of PEAP:
If the connection still fails with the same issue, temporarily change the setting above to notify the user if certificate doesn’t match. By doing so you will see what certificate is being presented during connection and confirm proper server certificate is being presented by ISE or not. It will reveal SHA1 hashed fingerprint which you can compare on ISE.
You can check the ISE EAP certificate by logging on to ISE GUI, then go to Administration -> System -> Certificates. Then on the left hand side, click Certificate Management -> System Certificates. Check to see which certificate is showing ‘Used By’ EAP. Click on the checkbox for the certificate and click on ‘View’ which reveals the Certificate Hierarchy and the SHA1 fingerprint. Make sure ISE can visualize the path between EAP certificate and the root CA and the fingerprint matches what client is seeing. If the path is incomplete, make sure to get the root CA and any intermediate certificate from Digicert and install them in to the ISE Trusted Certificate store. This will allow ISE to present proper certificate chain to the client during authentication.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-30-2018 03:28 AM
Certificate is irrelevant in case of remote access RADIUS. Please provide the full log message and make sure the authentication rule is matched. (Authentication rule may not match if PAP is not checked under Allowed Protocols.)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-01-2018 06:37 AM - edited 10-01-2018 06:38 AM
Some screenshot of the settings and additional information about the setup would help. But, since you are getting that error, I assume the RRAS and the client is using PPP-EAP, and either PEAP or EAP-TTLS EAP type. Having the Digicert root/intermediate in the client certificate store is not enough. You need to make sure the client authentication setting for VPN is configured to trust the Digicert root certificate for EAP purpose. You can do so by logging on to client Windows machine and go to its Network Connections. Find the VPN connection and click on its properties -> Security tab. Then under ‘Authentication’ click Properties and make sure the proper root CA is checked and the server names rule works with the ISE certificate. Showing here is example of PEAP:
If the connection still fails with the same issue, temporarily change the setting above to notify the user if certificate doesn’t match. By doing so you will see what certificate is being presented during connection and confirm proper server certificate is being presented by ISE or not. It will reveal SHA1 hashed fingerprint which you can compare on ISE.
You can check the ISE EAP certificate by logging on to ISE GUI, then go to Administration -> System -> Certificates. Then on the left hand side, click Certificate Management -> System Certificates. Check to see which certificate is showing ‘Used By’ EAP. Click on the checkbox for the certificate and click on ‘View’ which reveals the Certificate Hierarchy and the SHA1 fingerprint. Make sure ISE can visualize the path between EAP certificate and the root CA and the fingerprint matches what client is seeing. If the path is incomplete, make sure to get the root CA and any intermediate certificate from Digicert and install them in to the ISE Trusted Certificate store. This will allow ISE to present proper certificate chain to the client during authentication.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2018 12:51 PM
Adding Digicert to the trusted root authorities did take care of it. I had been doing some testing using only my internal CA and forgot that I needed to add the public root CAs also.
Thanks!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide