- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Preauthorizing Apple Computers at Login Screen
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-27-2019 07:31 AM
When a computer is sitting at the login screen, user authentication will not work and the machine will be kicked off the network without having a failback for machine pre-auth
We currently have a policy that has a condition for "Domain Computers" and gives them access to the corporate VN as well as a dACL for limited access to DNS, DHCP and AD.
This seems to work great for Windows machines, but our major problem right now is with Apple Mac computers.
Even though they are bound to AD, the Mac computers do not advertise themselves and being members of “Domain Computers” so this machine authentication policy does not work.
Does anyone have a recommendation for setting up a similar machine authentication policy for Mac computers so they do not get kicked off the network when sitting at the login window?
Possible solutions that I would like to avoid:
- Giving pre-auth to all Apple Computers based on OUI MAC
- Using MDM to set Login Window Mode (we have tried this in a limited capacity and MDM is unreliable and complex to set up)
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2019 12:40 PM
Giving pre-auth to all Apple Computers based on OUI MAC
If you have profiling in use technically you could utilize the AD-Probe and setup a scenario like this:
Parent Policy (Policy1) leverages and uses AD-Host-Exists EQUALS true. Then create a child policy(Policy-1-Child) that matches based on OUI MAC or some other attribute you can narrow down to your apple computers. Then use the profiled endpoint group in your condition to meet your requirement. Then you would know that any host profiled as Policy-1-Child (or whatever you name it) is a member of AD and an apple comp.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2019 12:28 PM
What about machine certs?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2019 12:40 PM
Giving pre-auth to all Apple Computers based on OUI MAC
If you have profiling in use technically you could utilize the AD-Probe and setup a scenario like this:
Parent Policy (Policy1) leverages and uses AD-Host-Exists EQUALS true. Then create a child policy(Policy-1-Child) that matches based on OUI MAC or some other attribute you can narrow down to your apple computers. Then use the profiled endpoint group in your condition to meet your requirement. Then you would know that any host profiled as Policy-1-Child (or whatever you name it) is a member of AD and an apple comp.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2019 01:45 PM - edited 05-29-2019 02:08 PM
Hey Mike
I appreciate this response. Its the first time someone has presented this as a possible solution.
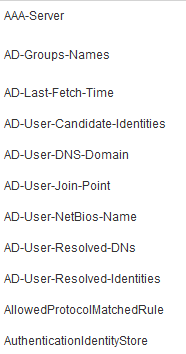
I have not used AD-Probe before for profiling. Do you know the syntax? Is it AD-Host-Exists EQUALS true?
I checked my deployment and see that AD probe is enabled. But when I look an an endpoint detail, I dont see AD-Host-Exists as a attribute
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2019 05:24 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2019 06:13 AM
I am getting host-name in the attributes.
I tried profiling based on AD-host-exists equals true and I don't see the devices getting profiled correctly in live logs
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide