- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Question: Public Root-CA vs private internal PKI for EAP-TLS from a security point of view
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2019 08:04 AM - edited 02-08-2019 08:05 AM
Hello,
we're currently migrating from ACS 5.8 to ISE 2.2 in a pure MS Windows environment with MS Active Directory and MS Windows Server PKI for internal purposes. Every domain joined endpoint gets provisioned with a client-certificate over group policy over which it authenticates to the ACS. Currently ACS is configured with this environment in mind, but now with ISE we want to expand that even further for "Eduroam" wireless clients, where we need a certificate from a publicly trusted certificate authority for roaming endpoints to be secured over EAP-TLS and for the ISE (currently FreeRadius) to establish an encrypted RADIUS (radsecproxy) connection to the federation server. But ISE can't handle more than one EAP-Certificate so we have to choose. Cost wise it is no option for us to set up another ISE-Cluster.
Now I'm standing here evaluating the security impacts switching our trusted internal PKI to a public trusted certificate authority might have... if that even has a impact. What do you think? Does switching from a purely internal PKI for EAP to a public trusted CA have an impact on security? The endpoints still get a client certificate for authentication, the only difference would be the EAP-Cert on the ISE and the trusted root ca change on the clients.
Thanks!
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2019 09:26 PM
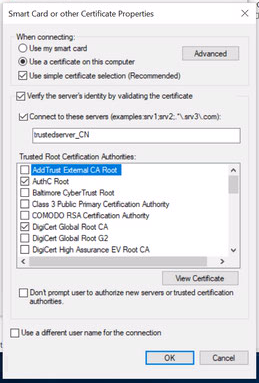
Since you are using endpoint certificates, the risk is not as big compared to using passwords. Using certificates the endpoint is merely sending public certificate to the server for validation. However, you can still add more security by using supplicant trust settings (Preferably via GPO) on all the machines. When doing so use 'Connect to these servers (example...):' option to validate the CN matches the new ISE EAP certificate. This allows supplicant to only trust your certificate and not any other server certificate signed by specific public CA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2019 09:26 PM
Since you are using endpoint certificates, the risk is not as big compared to using passwords. Using certificates the endpoint is merely sending public certificate to the server for validation. However, you can still add more security by using supplicant trust settings (Preferably via GPO) on all the machines. When doing so use 'Connect to these servers (example...):' option to validate the CN matches the new ISE EAP certificate. This allows supplicant to only trust your certificate and not any other server certificate signed by specific public CA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2019 06:05 AM - edited 02-09-2019 06:06 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2019 08:50 AM
You should use the same EAP cert on all the ISE PSNs that avoids the clients having to deal with different certs when authenticating. This could especially a problem if you have any mobile device authentication use case that like to complain about certificates the first time they connect to an SSID. If you have different certs on each PSN you could have multiple cert warnings. Just make a CN cert with radius.cisco.com as you said. You don't need to put the ISE PSN hostnames in the SAN field for the EAP authentication use case.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide