- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Renewal ISE 2.0.0.306 third party Wildcard Certificate
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2019 10:06 PM
Hi team,
Before posting here, I was searching and tried to find a post either from here or other places where it clears the step by step process, I know that this is a quite old version Im running,
I have some question regarding the renewal process on this version of ISE and perhaps you can give me some hints
We have a DigiCert certificate that is about to expire and it is serving only for our Guest Portal
Under the system certificate I can see the column: "Used by" Portal
The third party cert provider has sent me the file to which I have to bind it to ISE, in other words, its been renewed (purchased),
I checked trusted certificates and ROOTS by the vendor are good, so its just the cert being used by the portal
Do I need to create a new CSR? In other words, Do I need to click on Generate Certificate Signing Request (CSR) button to generate the file so I can re-send this new file?
They just sent me and provided me the file without asking me first for the CSR from ISE.
Can they sign the cert from the past records?
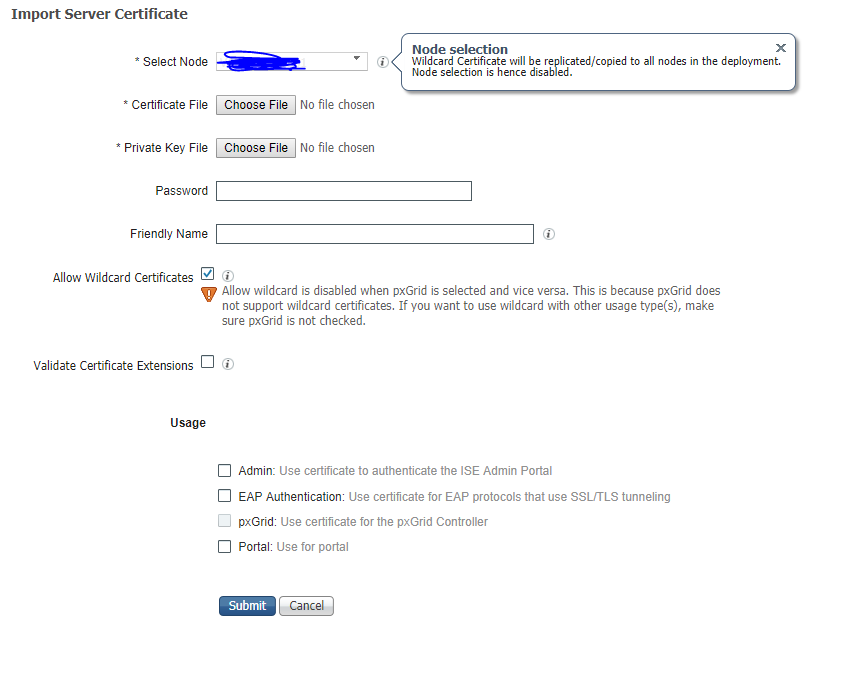
On the below image, is it simple as just
- uploading the files on certificate file and private key file?
- select: Allow wildcard certificates
- Put a password
- Select the check box: "Portal"
Will the appliance reboot ? or just the services will restart? If so, how many minutes will it take to restart the services (aprox)
Since its not expired yet the current one, is it best practice to export it and then delete it so the new one can be active?
I have 5 PSNs and 2 PANs, will the change take effect immediately and be reflected on all nodes?
What Im trying to find out is if there is going to be a severe downtime on end users or if its minimum considering the fact that it is only being used by the portal
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2019 04:27 AM - edited 03-20-2019 05:13 AM
Installing System certs can be done in two ways (this applies to any device that requires a system cert installed)
1) create a CSR and submit CSR to CA - CA creates Cert and you then install on your host - in ISE terminology this is called "binding" the cert to its private key. The act of generating a CSR does two things: creates a private key on the host. This private key should never leave the host. And then secondly it creates the public key and the CSR file.
2) Ask a CA (but not a public CA) to create the cert on their PKI. This is normal behaviour for an internal organisation that is mature and trusted to own all the private key of its clients. A public CA should NEVER have any clients' private keys! So internally you can ask your CA admins to create you a cert, and then export the whole lot including private key in a password encrypted file. This can then be installed in ISE. I have done this before many times but only for internal PKI certs.
The third method is when your public CA has issued you with a wildcard cert. In that case someone in your org would have created a CSR and got back a wildcard cert. All good. You install that on the system that created the CSR. Then you export that cert and private key and re-use it elsewhere. That is also typical behaviour. Wildcards are very handy for portals especially if you want to re-use what you already have.
I am not sure whether installing the new cert and associating it with your Portal will cause downtime. Maybe someone else can comment. Restarts happen when Admin certs are renewed. EAP cert renewal doesn't restart anything.
My guess is that there might be some disruption because these certs are tied to a web server - but in all honesty I would give this a go in the lab, even with a self signed cert and see what the impact is.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2019 04:27 AM - edited 03-20-2019 05:13 AM
Installing System certs can be done in two ways (this applies to any device that requires a system cert installed)
1) create a CSR and submit CSR to CA - CA creates Cert and you then install on your host - in ISE terminology this is called "binding" the cert to its private key. The act of generating a CSR does two things: creates a private key on the host. This private key should never leave the host. And then secondly it creates the public key and the CSR file.
2) Ask a CA (but not a public CA) to create the cert on their PKI. This is normal behaviour for an internal organisation that is mature and trusted to own all the private key of its clients. A public CA should NEVER have any clients' private keys! So internally you can ask your CA admins to create you a cert, and then export the whole lot including private key in a password encrypted file. This can then be installed in ISE. I have done this before many times but only for internal PKI certs.
The third method is when your public CA has issued you with a wildcard cert. In that case someone in your org would have created a CSR and got back a wildcard cert. All good. You install that on the system that created the CSR. Then you export that cert and private key and re-use it elsewhere. That is also typical behaviour. Wildcards are very handy for portals especially if you want to re-use what you already have.
I am not sure whether installing the new cert and associating it with your Portal will cause downtime. Maybe someone else can comment. Restarts happen when Admin certs are renewed. EAP cert renewal doesn't restart anything.
My guess is that there might be some disruption because these certs are tied to a web server - but in all honesty I would give this a go in the lab, even with a self signed cert and see what the impact is.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2019 04:46 AM
Hi,
Very well detailed from Arne as usual :)
We recently created CSR for our Sponsor Portal page for a wildcard certificate and installed the signed cert on one node.
Also better to create a Certificate Tag group for better management.
nothing rebooted and the good thing when u have wildcard Cert, you install it on one Node, it gets replicated to all the nodes you have.
For creating a wildcard cert please refer to this great manual from Aaron woland:
Btw if you are purchasing from a third party like Digicert, wildcard cert is more than double the price of a regular Cert.
what you could also do is create a regular cert with as much as possible Subject alternative names: SAN
like this you can cover many Portals with one cert.
ex:
guest.company.com
byod.company.com
sponsor.company.com
Please rate if helpful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2019 06:06 PM
you are right, abt the downtime, nothing happened :) and thanks for the URL,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2019 06:05 PM
that is good info at hands,
Im late with this reply because 2 days after posting, I was not able to access the post, seemed like it was deleted or something and I could not see my own post, lol
well, let me give you a brief summary
yesterday I uploaded the certs, there was many errors at the beginning, one of them was in the binding option I got a certificate /private key validation failed and the other one was invalid file
at the end, it was accepted via the import certificate under system certificates section. I have 2 files and a password one of them was a .pem and the other file was the private key, selected portal and prompted me to overwrite the existing certificate, I clicked yes, and it took immediately
the concern was the previous cert was there, the root and the intermediate root certificate has not expired, so all good from the trusted certificate store, no changes there,
however, when we renewed the cert and provided us the file crt only, no private key, I asked the sysad guy to convert and to their magic and he provided me the 2 files .pem and .key files and gave me a password (those worked)
the thing is that I did not create the CSR file and provided to the sysad guy so he provide to the public third party certificate vendor.
so I circled back again to where was the right method to upload in my scenario.
I should have created the CSR, download the .pem file and send it to sysad guy and he would have provided me the new cert, then go to binding option and put it there?
I mean, I just had the feeling that I skipped something along the way, because I did not provide anything from ISE itself, nor I did not use the binding option.
well, anyway, somehow and by lucky it worked now since it was a wildcard, all PSNs were renewed de facto, no system reboot nor applications rebooted, just took it right away, but from the import section,
not sure if Im having the right to say this but a lot of ISE documention lacks of this type of scenarios, type of files, etcs
or just simply I lack of knowledge which is true
thanks for your big help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2019 04:25 AM
Hi,
In fact when you want to get a certificate without a CSR you need the entire cert (Pub + priv key pair) that's the reason you received from the sysadmin 2 files with a password for the private key.
When you create a CSR, in the background you are creating a pub/priv key pair and send in the CSR the pub key part only.
Like this you can received a signed Cert (only one file) since the Private key stays on the ISE system.
it got complicated for you because you didn't create a CSR with binding.
Certificate extensions are can be explained in this link below:
Please rate if helpful
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2019 11:09 AM
super clear, now I have the full image,
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2019 06:09 AM
Glad we were able to help :).
Could you please mark the discussion as solved?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide