- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: VPN certificate auth using ISE?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2017 05:26 PM
Hey guys, I'm sure I read about this but my Google-fu is letting me down....
Basically, trying to authenticate VPN users using machine certificates (Cisco ASA VPN termination point) using ISE. That way we limit VPN access to machines on the domain. The idea is similar to machine authentication using EAP-TLS, but over VPN.
I know you can't do EAP-TLS over VPN, but how is this achieved with ISE?
Thanks
Darren
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-10-2017 11:20 AM
Typical VPN connection will terminate certificate auth at ASA, not ISE. In other words, ISE cannot authenticate the VPN users via certificate as it is never presented with a RADIUS auth request based on cert.
You could use secondary auth to verify identity based on extracted cert info, or straight user auth.
For cert only auth, you could use ISE for authorization only. You can lock down via tunnel group and then match RADIUS requests based on extended ASA VPN attributes (VPN-3000 disctionary...VSA ID: 3076/146). This would indicate user validated using machine cert.
Craig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-10-2017 11:20 AM
Typical VPN connection will terminate certificate auth at ASA, not ISE. In other words, ISE cannot authenticate the VPN users via certificate as it is never presented with a RADIUS auth request based on cert.
You could use secondary auth to verify identity based on extracted cert info, or straight user auth.
For cert only auth, you could use ISE for authorization only. You can lock down via tunnel group and then match RADIUS requests based on extended ASA VPN attributes (VPN-3000 disctionary...VSA ID: 3076/146). This would indicate user validated using machine cert.
Craig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-10-2017 04:28 PM
Can you provide a reference to this solution:
"You can lock down via tunnel group and then match RADIUS requests based on extended ASA VPN attributes (VPN-3000 disctionary...VSA ID: 3076/146). This would indicate user validated using machine cert."
I couldn't find anything.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-10-2017 06:46 PM
The VPN Group config is probably more of an ASA question, but essentially you can dictate which auth methods apply to which tunnel group (Connection Profile). To authenticate to TG "Employee", for example, you can set the authentication to cert auth. Employees would select TG via drop down, or crafted URL that matches TG.
The attribute I previously mentioned would be matched in Authorization condition to grant Employee access:
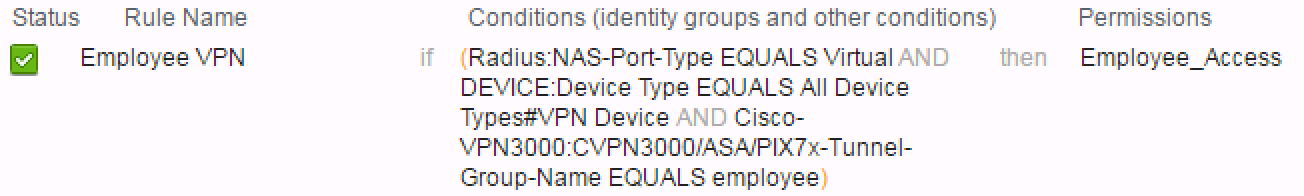
Example below shows how to match on specific NDG based on VPN devices, or NAS-Port-Type. It also shows use of the RADIUS Attribute to match on TG name.
/Craig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2017 07:24 AM
Darren,
There are a few caveats you will run into when setting this up if this is your first time doing this. My standard VPN now for customers is this:
Tunnel Group- Employee
- Group URL- www.mycompany.com/employee
- Authentication- Cert + AAA
- Client Profile- Mach Cert + Cert store override + Nice Name for Group URL (Employee VPN), automatic software updates, backup server config if needed
Tunnel Group- Vendor
- Group URL- www.mycompany.com/vendor
- Authentication- Cert + AAA
- Client Profile- Nice Name for Group URL (Vendor VPN), no software updates, backup server config if needed
In ISE, I setup a Policy set for Employee VPN and one for Vendor VPN keying off the tunnel group name as Craig stated above. I usually don't use the other conditions as no other device is going to be setting that Tunnel Group parameter.
The trick here is you HAVE to download the employee client profile (XML) file and distribute that out to your employees ahead of time, i.e. use SCCM to push the file to the AnyConnect profiles directory. The reason for this is the AnyConnect client on its own cannot look into the computer cert store. It needs to be told to look there by the XML file.
So we usually push the file out, have users test with it then send a communication out to employees to have them start using "Employee VPN" in their drop down. Then after a while we monitor who is still using the old tunnel group and contact them directly eventually shutting off the legacy tunnel group.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2017 08:44 AM
Using additional conditions like NDG will allow control over where policy is applied in case want to roll out and test to select VPN gateways.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2019 10:22 PM - edited 01-30-2019 10:26 PM
Hi Craig. It's been a while since your last post, however I'm hoping you can help us.
We have a scenario where we'd like to authenticate end user devices using machine based certificates. This is working fine on the ASA side - end user devices with valid certificates signed by our CA are authenticating without an issue - however we'd like to use ISE for authorisation, in particular for the dACLs.
We're finding it difficult to use a policy set (ISE v2.4) for this purpose, as the username is sent as "INVALID" when the ASA sends the AAA request to ISE - ie; authentication fails (probably due to certificate authentication being used instead of CHAP) - even though the authentication rule within the policy set is configured to "continue" if the username is not found - ie; we're using the authentication rule to match against the tunnel group to identify the correct dACL. Is there a trick we can use to "fool" ISE into accepting the authentication and then processing the authorisation? Given the end user device has been authenticated using machine based certificates, I'd say it is still a relatively secure approach.
Thanks in advance.
Chris.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-10-2017 12:28 PM
Adding to Craig, it's possible to perform EAP auth if using IKEv2 as the RA VPN protocol. See
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2019 10:15 AM
Christopher,
You should define an AAA server group in ASA and set the Connection Profile/Tunnel Group to use it for authorization only. AuthC is performed by ASA, ISE is not involved. Then an AuthZ request is sent to ISE, no AuthC is performed in this RADIUS session. This is implemented by Authorize-Only RADIUS request.
aaa-server ISERAD-authz protocol radius
authorize-only
tunnel-group EMP type remote-access
tunnel-group EMP general-attributes
authorization-server-group ISERAD-authz
authorization-required
username-from-certificate UPN
tunnel-group EMP webvpn-attributes
authentication certificate
The Username attribute will be contained in the RADIUS request and it should be the machine name. You should check and set in ASA which certificate field is suitable for computer name lookup in AD. I guess UPN or CN. It can be used by AD group membership conditions in ISE policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2019 12:56 AM
Dear Peter,
But how about authentication configuration on ISE side ? If we still configure authentication with option "If username not found" -> Continue ?
To summarize: I need only authorization from ISE, because ASA authenticate my client based on certificate.
Question is: What I must configure in section about authentication in ISE 2.4 ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2019 12:34 AM
The Authentication Policy does not really matter in this case actually as the RADIUS request contains Authorize-only attribute. Our AuthC policy contains a single line:
Default -----> AD
Auth Fail: REJECT
User not Found: REJECT
Process fail: DROP
No CONTINUE is needed.
If you have authentication failure logs the RADIUS request may not be az AuthZ-only request.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2020 07:08 AM
Hi Peter,
I am trying to get this working using AnyConnect, FTD and ISE 2.4.
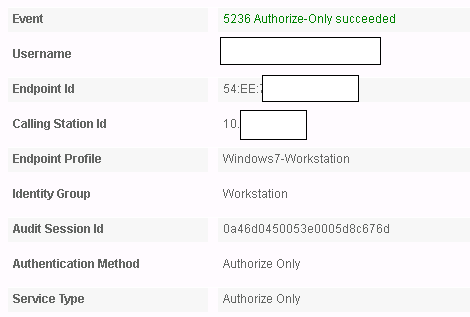
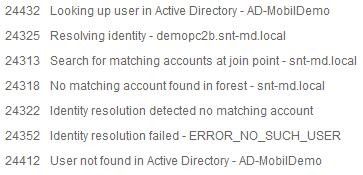
When the username is sent to ISE for authorization, using the machine name attribute from the certificate, ISE is not matching my authz profile because it can't find the "user". It appears it is trying to look up a user rather than machine, which is failing. See output below. Any ideas if I can resolve this?
The same ISE is successfully authenticating and authorising machines based on machine certificates using 802.1x for wireless.
|
Thanks
Russ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2020 10:40 AM
It should work if the certificate subject contains the Distinguished Name of the computer, e. g.
CN=machine,OU=Computers,DC=test,DC=local
instead of machine.test.local
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2020 05:30 AM
I had problems with FQDN and hostname too:
Then a rewrite rule helped:

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2023 03:49 PM - edited 04-21-2023 03:50 PM
Hello Gentleman,
I have the same task.. In our current environmant we have Cisco ASA anyconnect VPN. User gets authenticated via Username and RSA secure ID token. We have anyconnect VPN client in our environment and that will be continue to be used. We now have requirement to enable Username+Password authentication via Cisco ISE along with RSA secure ID token, as well if user machine is having machine certificate then only it is allowed to authorize to connect to VPN. Can anyone help me and provide me step by step instructions. Any help would be much appreciated. Thanks in Advance.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: