- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: WLAN Interface Groups with Cisco ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2019 03:58 AM
Hi,
Is it possible in Cisco ISE to push wireless interface group for WLAN 802.1x?
Also, is it possible for ISE to have an authorization policy like the following logic,
1. Each floors will be configured with a wireless ap-group (example, Level 1 will be having AP-Group A).
2. Each AP-group will be assigned into a VLAN (example, AP-Group-A will be having VLAN 10).
3. In ISE, if the users connects to this particular ap-group (AP-Group-A) then ISE will push VLAN10.
Thanks
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2019 06:59 AM - edited 03-18-2019 01:19 PM
Vlan Groups (for Cisco Switches) and Interface Groups (for Cisco WLCs) can be done if you simply return the "name" of the Group in your ISE Authorization Profile. I do it all the time for WLC's and for Cisco Switches.
And yes you can return Authorization Profiles for just about any condition that you can think of. But I would recommend using something that works universally. Groups are a good abstraction - and they also take care of DHCP exhaustion by performing DHCP snooping. If the client doesn't get a DHCP response then the Switch/WLC just runs the hash algorithm again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2019 06:37 AM - edited 03-18-2019 06:38 AM
Hi,
1- you could group your APs per floor and give them a specific name.
in the author Policy put a condition for called-station ID begins or ends with the specifies group name.
Point to an author profile that u can push a vlan like vlan 10 for example.
Please rate if helpful
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2019 06:59 AM - edited 03-18-2019 01:19 PM
Vlan Groups (for Cisco Switches) and Interface Groups (for Cisco WLCs) can be done if you simply return the "name" of the Group in your ISE Authorization Profile. I do it all the time for WLC's and for Cisco Switches.
And yes you can return Authorization Profiles for just about any condition that you can think of. But I would recommend using something that works universally. Groups are a good abstraction - and they also take care of DHCP exhaustion by performing DHCP snooping. If the client doesn't get a DHCP response then the Switch/WLC just runs the hash algorithm again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2019 07:06 AM
Hi @Arne Bier , thanks for the feedback.
What in particular should I use for the authorization policy in ISE for me to have if user is connecting to this particular "AP-Group", then push the VLAN?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2019 01:33 PM
I am not sure if you are just giving an example or really trying to have AP groups per floor on different VLANs. I think that will be disastrous as you can't control client roaming that precisely. It is completely possible on client on floor 3 will roam from a floor AP to a floor 2 AP back to a floor 3 AP as they walk around floor 3. If you move the client onto a different VLAN when it hit an AP on floor 2 the client will most likely be stuck because it will have an IP from floor 3 and not know to refresh.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2019 09:23 PM
@paul , based on my understanding in your statement, it is much better to have the wireless in 1 VLAN?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2019 10:09 PM
I am just cautioning that you have to think of client roaming and not necessarily always roaming to an AP on the same floor.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2019 06:46 AM
hi @paul , actually there is a real life scenario there that i need to take into consideration.
so every time a client goes to different floor and have a different ap-group, ISE needs to send out CoA to grab a new IP in that ap-group.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2019 07:31 AM
You are talking about client physically walking from floor 1 to floor 2, but I am saying that is not how wireless works. Client could be walking on floor 2 and be roaming between APs on floor 1 and floor 2. If those are mapped to different VLANs you are going to most likely disrupt the client's communication. The client will not know to refresh their IP because there is no network adapter event. The client is simply roaming on the same SSID.
I would test it in the lab before trying anything like this in productions. Setup two APs each with different VLAN assignment and roam between the two and watch your client get stranded when it roams from one to the other. I could be wrong, but I pretty sure you will see a disruption.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2019 04:34 PM
Hi Arne,
How is this configured on the WLAN and ISE? Is there documentation/examples available that you know of?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2019 11:40 PM
You're asking about the dynamic VLAN override on a Cisco WLC? The concept is that you return a VLAN name (string) instead of the VLAN number (numeric). On the WLC you always give an Interface a name. That WLC Interface Name string would be a valid string that ISE can return to the WLC during a RADIUS authentication. If your WLC is using Interface Groups, then put all your interfaces that you want/need into that Group, and tell ISE to return the Interface Group name string to the WLC during RADIUS auth.
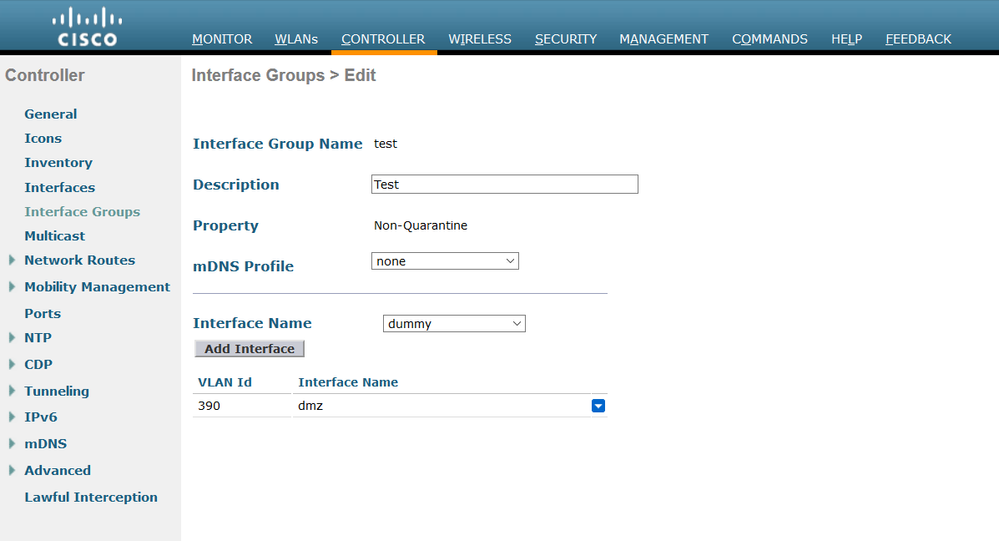
below is an example from an AirOS WLC which has an Interface Group with a very creative name of "test". That Group contains one VLAN at the moment - vlan 390, whose Interface is called 'dmz'.
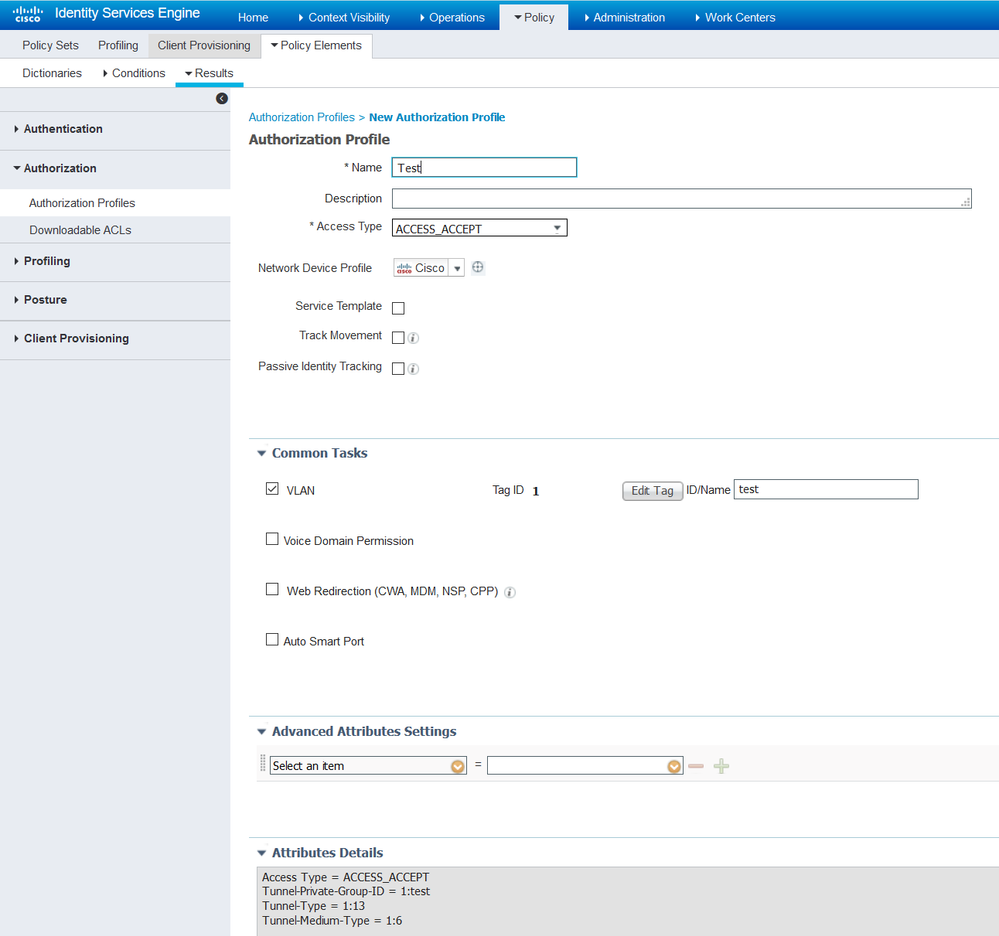
In ISE I would return an Authorization profile that looks like this
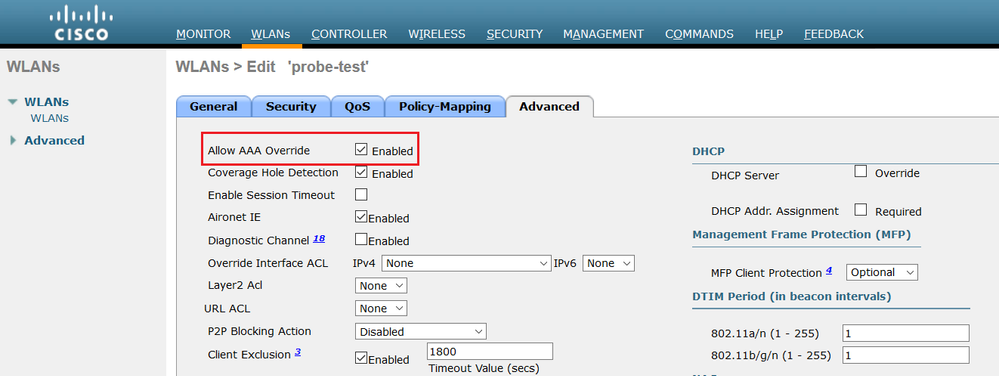
You have to ensure that the WLC WLAN is configured to allow AAA Override.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide