- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Cisco Firepower policy question
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2018 11:52 AM - edited 02-21-2020 07:27 AM
Hello,
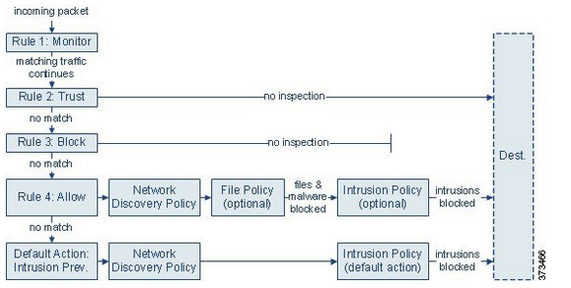
If you look at the below policy inspection by Firepower, You have allow and block permits, etc...Let's say, Rule number 3 also says block country South Korea from any source to any destination and under rule 2, I am allowing access to samsung.com. If I access samsung.com, I should be allowed to get through, right? well, not the case. It's still blocked, and reason? - Country blocked. Why? I thought, If I'm allowing the website at rule 2, I shouldn't even hit rule 3 and beyond, correct? Don't understand this. I checked with Cisco, they didn't really have an answer for me. Any ideas?
Solved! Go to Solution.
- Labels:
-
IPS and IDS
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2018 02:23 PM
I meant under Security Intelligence (SI) add a DNS Policy with your domains in a DNS Whitelist.
If you are not using SI you should review the features, they add additional levels of security at the benefit of the device because the SI Blacklist occurs before Rule 1 - no CPU wasted on inspection.
Once you get the DNS whitelist working you can review the SI Category blocking for IP's and DNS and determine if it fits your needs.
Cisco link:
https://www.cisco.com/c/en/us/td/docs/security/firepower/601/configuration/guide/fpmc-config-guide-v601/DNS_Policies.pdf
popravak has good write-ups about Firepower features as well:
https://popravak.wordpress.com/2016/03/22/sourcefire-security-intelligence-dns-policy/
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2018 03:18 PM
Hello,
Yes that is the premise, what do your logged events indicate?
Is the request to the URL logged in the Trust and then the IP blocked in the GEO blocking rule?
Check direction for the rules.
If the URL is trusted Source > Destination and the GEO rule is blocking ANY-ANY then return traffic may be denied.
When it comes to URL's it can get interesting.
What method of URL filtering are you using? SI URL White list or URL filtering license?
The requested URL may initially be allowed but if the site utilizes a CDN then some or all the traffic may not be coming from that URL/Domain or even the same country.
The Event logs and a capture at the client of a working session should help with the mystery.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2018 08:35 AM
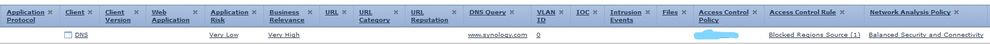
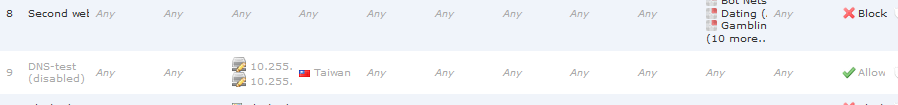
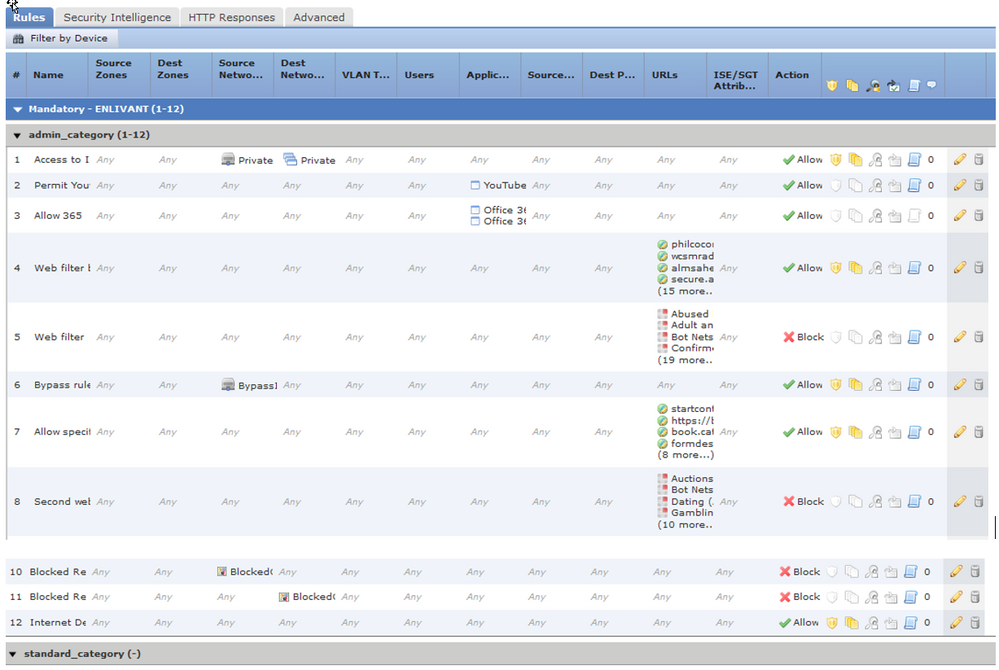
Here is a part of the log, it says it was blocked by source country. But why? I included a screenshot of my policy.
LOG:
POLICY
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2018 09:07 AM
The other fun part of URL filtering and trusts.
On the Blocked log the 'Client' is DNS.
It is not blocking the URL, it is blocking the Domain lookup. We can't see the source/dest IP addresses in your event but I assume the returned DNS server for site resides in your Geo Block or it returned the IP located in your Geo block. I'm not sure which the Geo blocking is acting on.
Try add the domains for your trusted URL's to the DNS whitelist on rule #4.
You may still have issues depending on how your DNS is set up and located (behind the IPS) if it is querying DNS servers globally.
You also may still have issues if content returned from trusted URLS comes from other sources with different url.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2018 01:03 PM
I see whats you're saying, I just not sure what you mean by this:
Try add the domains for your trusted URL's to the DNS whitelist on rule #4.
Can you explain?
Also, you're right, because when I added a rule 9 (thats why you dont see it there, I temporarily disabled it) I had my DNS servers allowed to THAILAND and that worked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2018 02:23 PM
I meant under Security Intelligence (SI) add a DNS Policy with your domains in a DNS Whitelist.
If you are not using SI you should review the features, they add additional levels of security at the benefit of the device because the SI Blacklist occurs before Rule 1 - no CPU wasted on inspection.
Once you get the DNS whitelist working you can review the SI Category blocking for IP's and DNS and determine if it fits your needs.
Cisco link:
https://www.cisco.com/c/en/us/td/docs/security/firepower/601/configuration/guide/fpmc-config-guide-v601/DNS_Policies.pdf
popravak has good write-ups about Firepower features as well:
https://popravak.wordpress.com/2016/03/22/sourcefire-security-intelligence-dns-policy/
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2018 06:17 AM
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: