- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: The primary intent is to tell
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2017 08:30 AM - edited 03-10-2019 06:52 AM
From the FMC -
I have created an Access Control Policy and within that Policy I have a simple "any to any" rule.
Within my "any to any" rule - I have my own Intrusion Policy set and also my own File Policy.under the inspection tab.
Within the Access Control Policy - what would be recommended default action in this scenario?
What is the actual order of operations with the above (if send traffic to the sensor using the above policy)
* All my traffic will match the any to any rule and will then be run through my inspection and file policy?
Should I then "trust" all traffic in the default action (as if it passes my intrusion and file policies, one would assume it is good?)
Am i understanding the order of things here? Any offerings of advice?
Thanks
Solved! Go to Solution.
- Labels:
-
IPS and IDS
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2017 08:46 PM
As far as the Access Control Policy, yes - you have it correct.
You should also be sure to setup your $HOME_NET and $EXTERNAL_NET objects,Discovery policy and FirePOWER IPS rule recommendations to better inform the ACP of the correct actions to take based on your actual network hosts and their vulnerabilities.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2017 08:46 PM
As far as the Access Control Policy, yes - you have it correct.
You should also be sure to setup your $HOME_NET and $EXTERNAL_NET objects,Discovery policy and FirePOWER IPS rule recommendations to better inform the ACP of the correct actions to take based on your actual network hosts and their vulnerabilities.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2017 01:11 AM
Thanks for the input Marvin.
For the following - $HOME_NET and $EXTERNAL_NET
$HOME_NET - I have put in 10/8 and 172.16/12
(Is it best practise to Narrow this down to actual address space used rather than just the whole RFC1918? Upon looking further, should I be creating network objects containing subnets for each remote site I have and then adding these objects inside the $HOME_NET variable?
For $EXTERNAL_NET -
(what is expected here? Any external IP address space owned/used by the company?, e.g RIPE assigned address space or similar?)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2017 01:57 AM
You're welcome.
The primary intent is to tell FirePOWER which hosts are inside your network and which are external. That information is used to give context for many Snort rules that have a directional aspect and to guide FirePOWER regarding which hosts to discover so that it can build more accurate profiles (what OS, what applications running etc.) that it can then use to fine tune your IPS rules to more accurately protect against compromises.
If you have a disparate set of internal networks all with private addresses then you can use the RFC 1918 pre-built object (since version 6.0) or define them manually as you have partially done with the 10.0.0.0/8 and 172.16.0.0/12 supernets. If you have any publicly addressed internal networks then be sure to include those in the $HOME_NET object.
Once you have $HOME_NET defined, the recommendation is to simply define $EXTERNAL_NET = !HOME_NET (that is, anything that is NOT the home net object).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2017 01:57 AM
Excellent points, thanks.
Last query and I believe I am good :-)
"Once you have $HOME_NET defined, the recommendation is to simply define $EXTERNAL_NET = !$HOME_NET (that is, anything that is NOT the home net object)"
Is this just a case of of going into the EXTERNAL_NET variable and adding HOME_NET to the excluded Networks?
Thanks again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2017 02:25 AM
Yes.
In FirePOWER Management center, go to Objects > Object Management > Variable Set > Edit Variable Set Default-Set > Edit variable $EXTERNAL_NET.
Select $HOME_NET and put it in the Excluded Networks column. Save and it should then show up as I noted - i.e., !HOME_NET.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2017 02:41 AM
It does indeed! Brilliant, thanks a lot Marvin. I do appreciate the time you take to answer my queries.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-25-2019 07:49 AM
Hello Marvin,
Please what do you mean by "Snort rules that have a directional aspect"?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
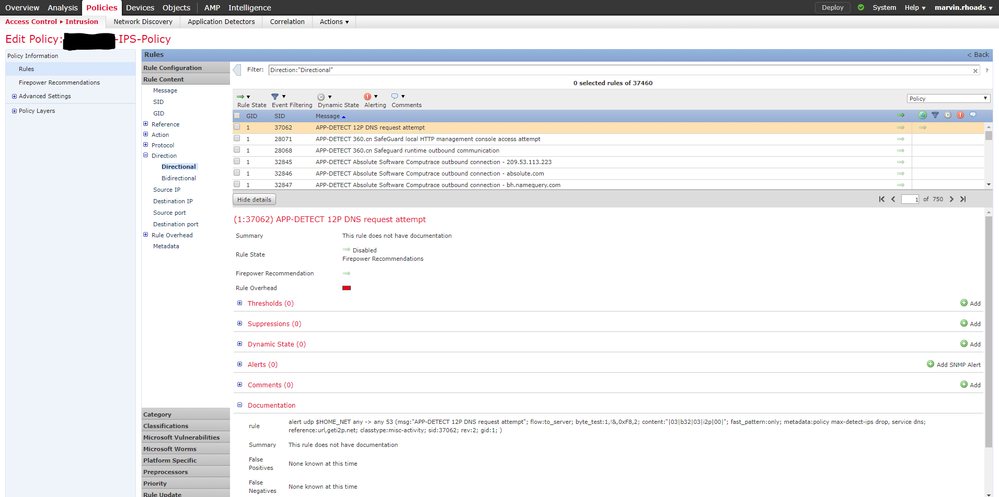
06-08-2019 07:33 AM
Some Snort rules (aka IPS Policy rules) have a direction specified within the rule. See the following screenshot for example and note that within the Rule tree I selected those with Rule Content > Direction > Directional. The one I have selected applies to traffic from $HOME_NET
:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-30-2019 04:24 AM
Thank You
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: