- Cisco Community
- Technology and Support
- Networking
- IPv6
- Dynamic IPv6 prefix delegation to core switch, lost cause?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Dynamic IPv6 prefix delegation to core switch, lost cause?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2020 07:17 AM
Hello,
We have a horrible ISP here that I can not change, delegating a dynamic IPV6 prefix with every connection just like IP4, thing is life was simpler when it was only two vlans and "core" switch was treated as L2 switch, now since the intervlan routing is done with the switch, I managed to have IPv6 connectivity by manually subnetting the delegated /56 prefix and IPv6 rip, now the problem is, every 2-3 days the ISP change the delegated prefix and IPv6 connectivity is lost.
It is driving me crazy, I really have searched everywhere for a solution but no luck any help is _greatly_ appreciated.
thank you.
- Labels:
-
IPv6 Configuration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2020 07:56 AM
can you us more information "every 2-3 days the ISP change the delegated prefix and IPv6 connectivity is lost. "
explain with example, show us what you configured, how your network connected ? what is the challenge you have.
if possible we can suggest to overcome the issue with simple way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2020 12:43 PM
!
! Last configuration change at 22:13:14 UTC Mon Sep 21 2020 by #########
! NVRAM config last updated at 22:21:31 UTC Mon Sep 21 2020 by #########
version 16.9
service timestamps debug datetime msec
service timestamps log datetime msec
service call-home
platform qfp utilization monitor load 80
no platform punt-keepalive disable-kernel-core
platform hardware throughput crypto 250000
!
hostname router
!
boot-start-marker
boot system flash bootflash:packages.conf
boot-end-marker
!
!
enable password #########
!
aaa new-model
!
!
aaa authorization exec default local
!
!
!
!
!
!
aaa session-id common
clock timezone UTC 2 0
cef table consistency-check IPv4 type scan-rib-ios count 100
call-home
! If contact email address in call-home is configured as sch-smart-licensing@cisco.com
! the email address configured in Cisco Smart License Portal will be used as contact email address to send SCH notifications.
contact-email-addr sch-smart-licensing@cisco.com
profile "CiscoTAC-1"
active
destination transport-method http
no destination transport-method email
!
ip domain name home.lan
!
!
!
login on-success log
ipv6 unicast-routing
!
!
!
!
!
!
!
subscriber templating
!
!
!
!
!
multilink bundle-name authenticated
!
!
!
crypto pki trustpoint TP-self-signed-3530869696
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-3530869696
revocation-check none
rsakeypair TP-self-signed-3530869696
!
crypto pki trustpoint SLA-TrustPoint
enrollment terminal
revocation-check crl
!
!
crypto pki certificate chain TP-self-signed-3530869696
certificate self-signed 01 nvram:IOS-Self-Sig#2.cer
crypto pki certificate chain SLA-TrustPoint
certificate ca 01 nvram:CiscoLicensi#1CA.cer
!
crypto pki certificate pool
cabundle nvram:ios_core.p7b
!
no license feature hseck9
license udi pid C1111X-8P sn ###############
license accept end user agreement
license boot level securityk9
no license smart enable
memory free low-watermark processor 70177
!
diagnostic bootup level minimal
!
spanning-tree extend system-id
et-analytics
!
!
username ######### privilege 15 password 0 #############
!
redundancy
mode none
!
!
!
!
!
vlan internal allocation policy ascending
!
!
class-map type inspect match-any CLASS
match protocol tcp
match protocol udp
match protocol icmp
!
policy-map type inspect WAN-TO-SELF-POLICY
class type inspect CLASS
inspect
class class-default
drop
policy-map type inspect LAN-TO-SELF-POLICY
class class-default
pass
policy-map type inspect LAN-TO-WAN-POLICY
class type inspect CLASS
inspect
class class-default
drop
policy-map type inspect SELF-TO-LAN-POLICY
class class-default
pass
policy-map type inspect SELF-TO-WAN-POLICY
class type inspect CLASS
inspect
class class-default
drop
policy-map type inspect WAN-TO-LAN-POLICY
class type inspect CLASS
inspect
class class-default
drop
!
zone security WAN
description internet
zone security LAN
description default lan
zone-pair security LAN_SELF source LAN destination self
service-policy type inspect LAN-TO-SELF-POLICY
zone-pair security LAN_WAN source LAN destination WAN
service-policy type inspect LAN-TO-WAN-POLICY
zone-pair security SELF_LAN source self destination LAN
service-policy type inspect SELF-TO-LAN-POLICY
zone-pair security SELF_WAN source self destination WAN
service-policy type inspect SELF-TO-WAN-POLICY
zone-pair security WAN_LAN source WAN destination LAN
service-policy type inspect WAN-TO-LAN-POLICY
zone-pair security WAN_SELF source WAN destination self
service-policy type inspect WAN-TO-SELF-POLICY
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface Loopback0
ip address 172.16.1.1 255.255.255.255
!
interface GigabitEthernet0/0/0
no ip address
negotiation auto
!
interface GigabitEthernet0/0/0.881
encapsulation dot1Q 881
pppoe enable group global
pppoe-client dial-pool-number 1
!
interface GigabitEthernet0/0/1
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet0/1/0
switchport access vlan 1000
!
interface GigabitEthernet0/1/1
switchport access vlan 1000
!
interface GigabitEthernet0/1/2
switchport access vlan 1000
!
interface GigabitEthernet0/1/3
switchport access vlan 1000
!
interface GigabitEthernet0/1/4
switchport access vlan 1000
!
interface GigabitEthernet0/1/5
switchport access vlan 1000
!
interface GigabitEthernet0/1/6
switchport access vlan 1000
!
interface GigabitEthernet0/1/7
switchport access vlan 1000
!
interface Vlan1
no ip address
!
interface Vlan1000
description Routed WAN
ip address 192.168.1.1 255.255.255.252
ip nat inside
zone-member security LAN
ipv6 address 2001:16A2:5F38:DF10::/64 eui-64
ipv6 address PD ::/64 eui-64
ipv6 enable
ipv6 rip RIP6 enable
!
interface Dialer1
ip address negotiated
ip nat outside
zone-member security WAN
encapsulation ppp
ip tcp adjust-mss 1452
dialer pool 1
dialer idle-timeout 0
dialer persistent
dialer-group 1
ipv6 address autoconfig default
ipv6 enable
ipv6 dhcp client pd hint ::/56
ipv6 dhcp client pd PD
ipv6 dhcp client request vendor
ipv6 rip RIP6 enable
ppp mtu adaptive
ppp authentication pap callin
ppp pap sent-username ############## password 7 ##########
ppp ipcp dns request
ppp ipcp route default
!
!
router eigrp 1
network 192.168.1.0 0.0.0.3
redistribute static
!
ip forward-protocol nd
no ip http server
no ip http secure-server
ip nat inside source list 11 interface Dialer1 overload
ip ssh version 2
!
!
access-list 11 permit 192.168.1.0 0.0.0.3
access-list 11 permit 192.168.10.0 0.0.0.255
access-list 11 permit 192.168.20.0 0.0.0.255
access-list 11 permit 192.168.30.0 0.0.0.255
access-list 11 permit 192.168.50.0 0.0.0.255
access-list 11 permit 192.168.90.0 0.0.0.255
ipv6 router rip RIP6
redistribute ND
!
!
!
!
!
!
!
control-plane
!
!
line con 0
transport input none
stopbits 1
line vty 0 4
password ###########
!
ntp server 162.159.200.123 source Dialer1
!
!
!
!
!
end
Switch:
!
! Last configuration change at 22:17:49 UTC Mon Sep 21 2020
! NVRAM config last updated at 22:22:19 UTC Mon Sep 21 2020
!
version 16.12
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
service call-home
no platform punt-keepalive disable-kernel-core
!
hostname switch
!
!
vrf definition Mgmt-vrf
!
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
!
enable secret 9 ########################################
enable password ###########!$#!#
!
!
!
!
no aaa new-model
boot system switch all flash:packages.conf
clock timezone UTC 2 0
switch 1 provision c9200l-24t-4g
!
!
!
!
!
!
!
!
!
ip routing
!
ip name-server 8.8.8.8 1.1.1.1
ip domain name home.lan
!
!
!
login on-success log
ipv6 unicast-routing
call-home
! If contact email address in call-home is configured as sch-smart-licensing@cisco.com
! the email address configured in Cisco Smart License Portal will be used as contact email address to send SCH notifications.
contact-email-addr sch-smart-licensing@cisco.com
profile "CiscoTAC-1"
active
destination transport-method http
no destination transport-method email
no device-tracking logging theft
!
crypto pki trustpoint SLA-TrustPoint
enrollment terminal
revocation-check crl
!
crypto pki trustpoint TP-self-signed-765792206
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-765792206
revocation-check none
rsakeypair TP-self-signed-765792206
!
!
crypto pki certificate chain SLA-TrustPoint
certificate ca 01 nvram:CiscoLicensi#1CA.cer
crypto pki certificate chain TP-self-signed-765792206
certificate self-signed 01 nvram:IOS-Self-Sig#8.cer
!
crypto pki certificate pool
cabundle nvram:ios_core.p7b
!
!
!
diagnostic bootup level minimal
!
spanning-tree mode rapid-pvst
spanning-tree extend system-id
memory free low-watermark processor 10055
!
username cisco privilege 15 password 0 ###########!###########!#
username ########## privilege 15 password 0 #################################
!
redundancy
mode sso
!
!
!
class-map match-any system-cpp-police-ewlc-control
description EWLC Control
class-map match-any system-cpp-police-topology-control
description Topology control
class-map match-any system-cpp-police-sw-forward
description Sw forwarding, L2 LVX data packets, LOGGING, Transit Traffic
class-map match-any system-cpp-default
description EWLC data, Inter FED Traffic
class-map match-any system-cpp-police-sys-data
description Openflow, Exception, EGR Exception, NFL Sampled Data, RPF Failed
class-map match-any system-cpp-police-punt-webauth
description Punt Webauth
class-map match-any system-cpp-police-l2lvx-control
description L2 LVX control packets
class-map match-any system-cpp-police-forus
description Forus Address resolution and Forus traffic
class-map match-any system-cpp-police-multicast-end-station
description MCAST END STATION
class-map match-any system-cpp-police-high-rate-app
description High Rate Applications
class-map match-any system-cpp-police-multicast
description MCAST Data
class-map match-any system-cpp-police-l2-control
description L2 control
class-map match-any system-cpp-police-dot1x-auth
description DOT1X Auth
class-map match-any system-cpp-police-data
description ICMP redirect, ICMP_GEN and BROADCAST
class-map match-any system-cpp-police-stackwise-virt-control
description Stackwise Virtual OOB
class-map match-any non-client-nrt-class
class-map match-any system-cpp-police-routing-control
description Routing control and Low Latency
class-map match-any system-cpp-police-protocol-snooping
description Protocol snooping
class-map match-any system-cpp-police-dhcp-snooping
description DHCP snooping
class-map match-any system-cpp-police-ios-routing
description L2 control, Topology control, Routing control, Low Latency
class-map match-any system-cpp-police-system-critical
description System Critical and Gold Pkt
class-map match-any system-cpp-police-ios-feature
description ICMPGEN,BROADCAST,ICMP,L2LVXCntrl,ProtoSnoop,PuntWebauth,MCASTData,Transit,DOT1XAuth,Swfwd,LOGGING,L2LVXData,ForusTraffic,ForusARP,McastEndStn,Openflow,Exception,EGRExcption,NflSampled,RpfFailed
!
policy-map system-cpp-policy
!
!
!
!
!
!
!
!
!
!
!
!
!
interface Loopback0
ip address 172.16.2.1 255.255.255.255
!
interface Port-channel1
switchport access vlan 50
switchport mode access
!
interface Port-channel2
switchport access vlan 50
!
interface GigabitEthernet0/0
vrf forwarding Mgmt-vrf
ip address 10.0.0.1 255.255.255.0
negotiation auto
!
interface GigabitEthernet1/0/1
switchport access vlan 30
!
interface GigabitEthernet1/0/2
switchport access vlan 30
!
interface GigabitEthernet1/0/3
switchport access vlan 30
switchport mode access
!
interface GigabitEthernet1/0/4
switchport access vlan 30
!
interface GigabitEthernet1/0/5
switchport access vlan 30
!
interface GigabitEthernet1/0/6
switchport access vlan 30
!
interface GigabitEthernet1/0/7
switchport access vlan 30
!
interface GigabitEthernet1/0/8
switchport access vlan 30
!
interface GigabitEthernet1/0/9
switchport access vlan 30
!
interface GigabitEthernet1/0/10
switchport access vlan 30
!
interface GigabitEthernet1/0/11
switchport access vlan 30
!
interface GigabitEthernet1/0/12
switchport access vlan 20
!
interface GigabitEthernet1/0/13
switchport access vlan 10
!
interface GigabitEthernet1/0/14
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet1/0/15
switchport access vlan 30
switchport mode access
!
interface GigabitEthernet1/0/16
switchport access vlan 50
switchport mode access
channel-group 1 mode active
!
interface GigabitEthernet1/0/17
switchport access vlan 50
switchport mode access
channel-group 1 mode active
!
interface GigabitEthernet1/0/18
switchport access vlan 50
switchport mode access
channel-group 1 mode active
!
interface GigabitEthernet1/0/19
switchport access vlan 50
switchport mode access
channel-group 1 mode active
!
interface GigabitEthernet1/0/20
switchport access vlan 90
switchport mode access
!
interface GigabitEthernet1/0/21
switchport access vlan 50
channel-group 2 mode active
!
interface GigabitEthernet1/0/22
switchport access vlan 50
channel-group 2 mode active
!
interface GigabitEthernet1/0/23
switchport access vlan 50
channel-group 2 mode active
!
interface GigabitEthernet1/0/24
switchport access vlan 50
channel-group 2 mode active
!
interface GigabitEthernet1/1/1
switchport access vlan 30
switchport mode trunk
!
interface GigabitEthernet1/1/2
switchport access vlan 30
switchport mode trunk
!
interface GigabitEthernet1/1/3
switchport access vlan 30
switchport mode trunk
!
interface GigabitEthernet1/1/4
description To Router
no switchport
ip address 192.168.1.2 255.255.255.252
ipv6 address 2001:16A2:5F38:DF11::/64 eui-64
ipv6 enable
ipv6 rip RIP6 enable
!
interface Vlan1
no ip address
shutdown
!
interface Vlan10
ip address 192.168.10.1 255.255.255.0
ip helper-address 192.168.50.10
ipv6 address 2001:16A2:5F38:DF40::/64 eui-64
ipv6 enable
ipv6 rip RIP6 enable
!
interface Vlan20
ip address 192.168.20.1 255.255.255.0
ip helper-address 192.168.50.10
ipv6 address 2001:16A2:5F38:DF20::/64 eui-64
ipv6 enable
ipv6 rip RIP6 enable
!
interface Vlan30
ip address 192.168.30.1 255.255.255.0
ip helper-address 192.168.50.10
ipv6 address 2001:16A2:5F38:DF30::/64 eui-64
ipv6 enable
ipv6 rip RIP6 enable
!
interface Vlan50
ip address 192.168.50.1 255.255.255.0
!
interface Vlan90
ip address 192.168.90.1 255.255.255.0
ip helper-address 192.168.50.10
!
!
router eigrp 1
network 192.168.1.0 0.0.0.3
network 192.168.10.0
network 192.168.20.0
network 192.168.30.0
network 192.168.50.0
network 192.168.90.0
eigrp stub connected summary
!
ip forward-protocol nd
no ip http server
no ip http secure-server
ip ssh version 2
!
!
ipv6 router rip RIP6
!
!
!
control-plane
service-policy input system-cpp-policy
!
!
line con 0
stopbits 1
line aux 0
stopbits 1
line vty 0 4
password ##########
login
length 0
line vty 5 15
password ##########
login
!
ntp server 162.159.200.123
!
!
!
!
!
end
Switch Output:
switch#show ipv6 route
IPv6 Routing Table - default - 13 entries
Codes: C - Connected, L - Local, S - Static, U - Per-user Static route
R - RIP, D - EIGRP, EX - EIGRP external, ND - ND Default
NDp - ND Prefix, DCE - Destination, NDr - Redirect, O - OSPF Intra
OI - OSPF Inter, OE1 - OSPF ext 1, OE2 - OSPF ext 2, ON1 - OSPF NSSA ext 1
ON2 - OSPF NSSA ext 2
R ::/0 [120/2]
via FE80::7E21:EFF:FE20:DFF4, GigabitEthernet1/1/4
R 2001:16A2:401C:4E3C::/64 [120/2]
via FE80::7E21:EFF:FE20:DFF4, GigabitEthernet1/1/4
R 2001:16A2:5F38:DF00::/64 [120/2]
via FE80::7E21:EFF:FE20:DFF4, GigabitEthernet1/1/4
R 2001:16A2:5F38:DF10::/64 [120/2]
via FE80::7E21:EFF:FE20:DFF4, GigabitEthernet1/1/4
C 2001:16A2:5F38:DF11::/64 [0/0]
via GigabitEthernet1/1/4, directly connected
L 2001:16A2:5F38:DF11:72B3:17FF:FECA:6BF4/128 [0/0]
via GigabitEthernet1/1/4, receive
C 2001:16A2:5F38:DF20::/64 [0/0]
via Vlan20, directly connected
L 2001:16A2:5F38:DF20:72B3:17FF:FECA:6BD6/128 [0/0]
via Vlan20, receive
C 2001:16A2:5F38:DF30::/64 [0/0]
via Vlan30, directly connected
L 2001:16A2:5F38:DF30:72B3:17FF:FECA:6BE5/128 [0/0]
via Vlan30, receive
C 2001:16A2:5F38:DF40::/64 [0/0]
via Vlan10, directly connected
L 2001:16A2:5F38:DF40:72B3:17FF:FECA:6BC6/128 [0/0]
via Vlan10, receive
L FF00::/8 [0/0]
via Null0, receive
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2020 11:04 PM
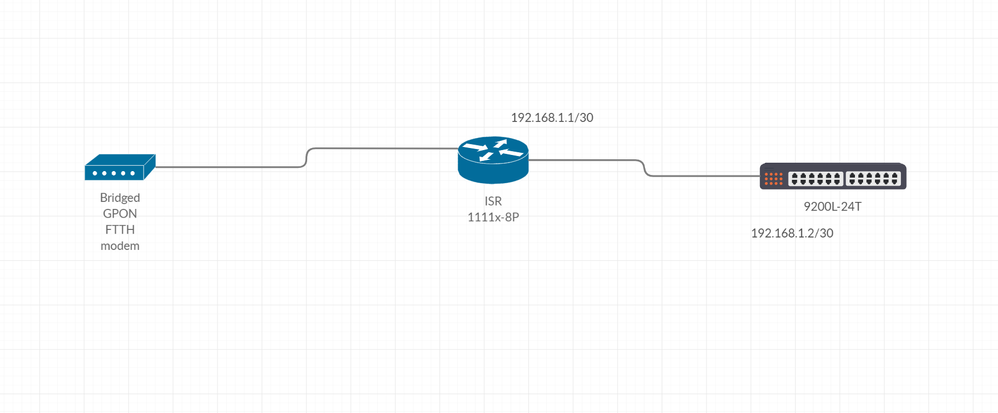
Here is the deal, router is connected to the internet via PPPOE and the received IPV6 prefix changes periodically (every 2 - 3 days) by the ISP rendering the previously delegated prefix useless, I need to use the switch as L3 for intervlan routing, and I can not figure out how to use the changing delegated prefix (except manually assigning the IPV6 addresses to switch SVIs with every change)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2020 10:02 AM
New to this community forum, and am very interested in deep dives into some into subject matters. Rfc 4862 5.4 and networkworld.com setting up Dhcpv6 to dynamically issue ipv6 addreses in a network has. Hope this was helpful.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide