- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: 12935 Supplicant stopped responding to ISE during EAP-TLS certific
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2022 06:49 AM
Hi,
We have a two-mode ISE 2.7 Patch6 deployed.
Recently we rolled out 802.1X to all our customers Windows10 laptops and desktops with EAP-TLS. The majority (98%) of the users can login to the network without any issues.
Some users get this error message “Can’t verify the server’s identity. If you’re trying to connect to your organisation’s Ethernet network, go ahead and connect. Continue connecting?” About 50% of users who get this error message can access the network without any issues.
For the remaining users, they cannot login to the network. In the ISE logs, they get the following.
Event 5411 Supplicant stopped responding to ISE
Failure Reason 12935 Supplicant stopped responding to ISE during EAP-TLS certificate exchange
I ran the following on the local access switch where one of the users is patched into:
- debug radius
- debug dot1x all
- debug epm all
- conf t
- no logging console
- no logging monitor
- Logging buffered 7
- logging buffered 10000000
- exit
- clear logging
- show logging
I was able to confirm that the MTU is 1500 so was able to rule jumbo frame out as a root cause.
802.1X settings on the wired adapter are delivered via GPO
For all Laptops and Desktops, dot1x authentication needs to be enabled using the following settings, this is completed by deploying a GPO for all desktops and laptops:
For the ethernet connections properties for their network connectivity, do the following:
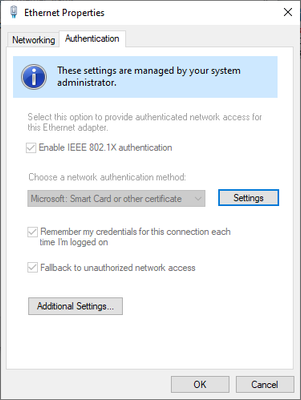
- Go to Properties
- Select Authentication
- Enable IEEE 802.1X authentication
- Select Microsoft Smart Card or Other Certificate:
- Select Remember my credentials for this connection each time I’m logged on
- Select Fallback to unauthorized network access
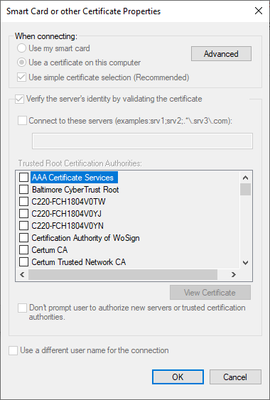
- For Microsoft Smart Card or Other Certificate, select Settings:
- Select “Use a certificate on this computer
- Select Use simple certificate selection (Recommended)
- Select Verify the server’s identity by validating the certificate
- The certificate COMPANY Trust 1 is selected.
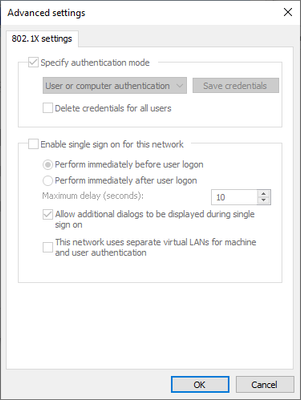
For Additional Settings in the Authentication tab, do the following
- Select specify authentication mode
- Select User or Computer authentication
- Do not select anything else.
Verify Certificates on COMPANY Device (Laptop or Desktop)
USER CERTIFICATE:
The user logging into the network should have a certificate issued by COMPANYTrust2
MACHINE CERTIFICATE:
The machine logging into the network should have a certificate issued by COMPANYTrust1
ISE is configured as follows:
Any ideas on what I can try to get them on the network
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2022 08:04 AM
The cert for the ISE appliance is on the endpoint's is in the client local trust store.
-So to clarify so we are in sync:
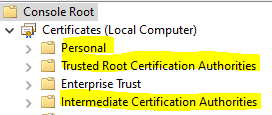
--User cert would be in 'Personal' store (User Certificates); Computer cert would be in personal store under Certificates(Local Computer)
--Intermediate and Root Certs in the chains should be placed in their respective stores: ex: intermediate certs go in Intermediate Certification Authorities trust store; root certs go in Trusted Root Certification Authorities store;
So essentially both chains for COMPANYTrust1 and 2 need to be in the stores on the local client including the chain (whichever CA has issued ISE its identity cert) this way clients trust ISE. Once this is confirmed test again to see if your result is different for the 'Can’t verify the server’s identity.' problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2022 06:58 AM
Some users get this error message “Can’t verify the server’s identity. If you’re trying to connect to your organisation’s Ethernet network, go ahead and connect. Continue connecting?” About 50% of users who get this error message can access the network without any issues.
-Do you have the certificate chain for the ISE identity cert presented in the client local trust store? On the supplicant configuration since you have 'The certificate COMPANY Trust 1 is selected' make sure this is in the trust store as I am assuming this a part of the hierarchy presented with ISE cert.
Event 5411 Supplicant stopped responding to ISE
-IMO usually this can indicate a misconfiguration on supplicant side.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2022 07:19 AM
Hi Mike,
The cert for the ISE appliance is on the endpoint's is in the client local trust store.
"The user logging into the network should have a certificate issued by COMPANYTrust2" In CertMgr, the users has a cert issued to them by COMPANYTrust2 in Certificates - Current User\Personal\Certificates.
"The machine logging into the network should have a certificate issued by COMPANYTrust1" In CertMgr, the machine has a cert issued to them by Certificates - Current User\Trusted Root Certificate Authorities\Certificates
Hope this help, I get lost when it comes to certificates sometimes.
Thanks
Anthony.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2022 08:04 AM
The cert for the ISE appliance is on the endpoint's is in the client local trust store.
-So to clarify so we are in sync:
--User cert would be in 'Personal' store (User Certificates); Computer cert would be in personal store under Certificates(Local Computer)
--Intermediate and Root Certs in the chains should be placed in their respective stores: ex: intermediate certs go in Intermediate Certification Authorities trust store; root certs go in Trusted Root Certification Authorities store;
So essentially both chains for COMPANYTrust1 and 2 need to be in the stores on the local client including the chain (whichever CA has issued ISE its identity cert) this way clients trust ISE. Once this is confirmed test again to see if your result is different for the 'Can’t verify the server’s identity.' problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2022 01:39 PM
You were right. I was missing the root cert. This was not getting deployed in the GPO.
Thanks for all your help.
Thanks
Anthony.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2023 07:57 AM
Hello Mike,
I have almost the same issue in my environment, partially some devices aren't authenticated some are, same certificates, same GPO for all of them. I've checked on those who didn't respond to EAP-TLS certificate exchange to see have those valid certificates stored intermediate and trusted root, all valid and all the same as on other endpoints which are successfully authenticated.
steps are as follows:
these one are repeating for some
12505 Prepared EAP-Request with another EAP-TLS challenge
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12504 Extracted EAP-Response containing EAP-TLS challenge-response
12571 ISE will continue to CRL verification if it is configured for specific CA - certificate for Berin.mbdom.rbbh
12571 ISE will continue to CRL verification if it is configured for specific CA - certificate for RBBH Issuing CA
12811 Extracted TLS Certificate message containing client certificate
12812 Extracted TLS ClientKeyExchange message
12813 Extracted TLS CertificateVerify message
12804 Extracted TLS Finished message
12801 Prepared TLS ChangeCipherSpec message
12802 Prepared TLS Finished message
12816 TLS handshake succeeded
12509 EAP-TLS full handshake finished successfully
12505 Prepared EAP-Request with another EAP-TLS challenge
11006 Returned RADIUS Access-Challenge
12935 Supplicant stopped responding to ISE during EAP-TLS certificate exchange (step latency=120001 ms Step latency=120001 ms)
61025 Open secure connection with TLS peer
5411 Supplicant stopped responding to ISE
any suggestions? everyhting happens under the appropriate policy set.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide