- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Access rights in ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2022 04:00 AM
Hi,
I have a two node ISE deployment, version 3.0 Patch 4.
I have a requirement where a team needs to have Identity Admin access and read only for all other components.
I have been trying to add a user to the Identity Admin group plus System Admin Menu Access in the hope that they can continue to do the Identity Admin function and see everything else (read-only, for troubleshooting) but it gives the user Full Access.
Is this possible to do in ISE.
Thanks
Anthony.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2022 09:49 AM
I don't think this bug is applicable to my issue.
I have an issue where if I have given a user super admin menu access with identity admin data access, the user can see everything and edit everything.
If I make a copy of super admin data access and only select the same data access as Identity admin, the user can still edit everything.
Maybe I have read it wrong or don't understand.
As far as I can see, the user will have two accounts: Identity Admin to do his job and a Read Only a/c to do his troubleshooting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2022 06:59 PM
Anthony O'Reilly is correct. See CSCvm01451
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2022 04:31 AM
You can do this. Best is to prepare your own Access-Permission as needed and use them in a new RBAC policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2022 04:33 AM
I believe you need to do some tweaking to achieve this and testing: below document can help you :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2022 05:12 AM
I have been trying to add a user to the Identity Admin group plus System Admin Menu Access in the hope that they can continue to do the Identity Admin function and see everything else (read-only, for troubleshooting) but it gives the user Full Access.
-Your best bet is to create duplicates of the default menu/data access types then tweak the copied policies to meet your need and tie the two together. This may better fit your desire and is something you will have to test.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2022 06:58 AM
Hi @Mike.Cifelli @balaji.bandi @Karsten Iwen
I really don't think this is possible.
I tried the following:
1. Super Admin Menu access with Identity Admin Data, the result is I can edit everything.
2. Copied Identity Admin Data, called it Test and changed Data Access Privileges for Admin and Network Device Groups to Read Only, the result is I can edit everything.
My test was to see if I could update any Policy Sets, I should only be able to read them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2022 03:26 PM
Hi @Anthony O'Reilly ,
it's a BUG !!! : )
Note: please take a look at CSCvw90961 RBAC rules not enforced in 2.7 and CSCvb55884 ISE RBAC Network Device Type/Location View not working. for similar references.
Hope this helps !!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2022 09:49 AM
I don't think this bug is applicable to my issue.
I have an issue where if I have given a user super admin menu access with identity admin data access, the user can see everything and edit everything.
If I make a copy of super admin data access and only select the same data access as Identity admin, the user can still edit everything.
Maybe I have read it wrong or don't understand.
As far as I can see, the user will have two accounts: Identity Admin to do his job and a Read Only a/c to do his troubleshooting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2022 06:59 PM
Anthony O'Reilly is correct. See CSCvm01451
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2022 12:33 AM
Hi @hslai
Yes, this does look like a bug that explains my issue.
My solution is to have a user_ro account and a user_identity account for the customer.
Thanks everyone for your help and advice, much appreciated.
Thanks
Anthony.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2022 03:32 PM
Sounds like you want SuperAdmin Menu Access (read everything) but Identity Admin Data Access (only change identities). OK.
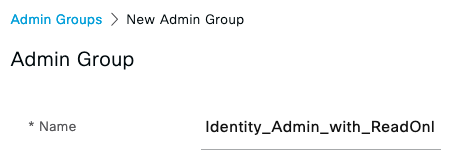
Navigate to Administration > System > Admin Access > Administrators > Admin Groups and create a new Admin Group "Identity_Admin_with_ReadOnly"
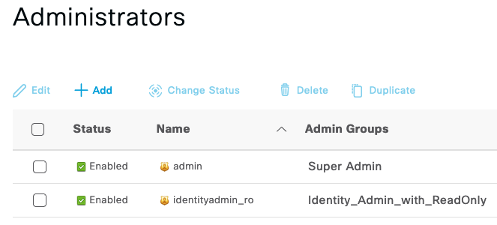
Navigate to Administration > System > Admin Access > Administrators > Admin Users and create a new Admin Users "Identity_admin_ro" in the "Identity_Admin_with_ReadOnly" group :
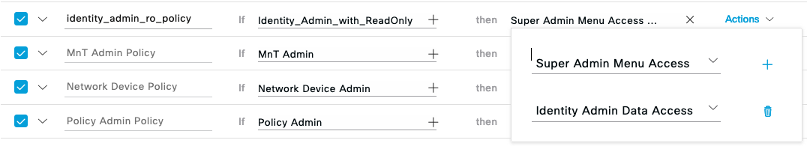
Navigate to Administration > System > Admin Access > Authorization > RBAC Policy
and use Actions > Insert a New Policy to add your SuperAdmin menus with Identity Admin Data:
Don't forget to Save.
Logout and login as identityadmin_ro
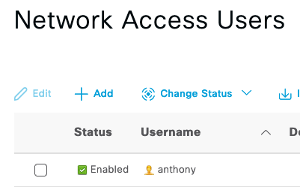
Go add a new Identity (Network Access User):
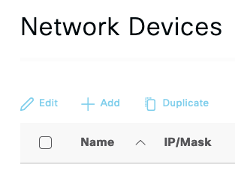
Then try to change anything else like adding a Network Device and it should be DISABLED (+Add is disabled and cannot be changed):
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2022 12:31 AM
Hi @thomas
Thanks for your details response with screen shot, I was doing exactly as you stated and the result is full-access for the user.
I did exactly as you said with the same naming conventions and I can edit policies. I only want the user to have read-only to all.
Thanks
Anthony.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2022 05:54 AM
Hello Anthony,
Did you find a solution?
T&R
Arjun
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-21-2022 02:25 AM
Hi,
It is not possiuble to do under one account due to the read-only setup within ISE.
I had to create two account, one with read-only and the other one with Identity Admin.
Thanks
Anthony.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide