- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ASA to FTD migration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA to FTD migration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2020 05:27 PM
I want to convert ASA configuration to Firepower as prefilter rules instead of ACEs. I do not see any option in the migration tool to do so.
- Labels:
-
Appliances
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2020 12:26 AM
I do not believe you have that option, you need to make some of the requirement manually and test it.
Since its only feature available ASA to FTD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-26-2020 01:46 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-26-2020 04:03 PM
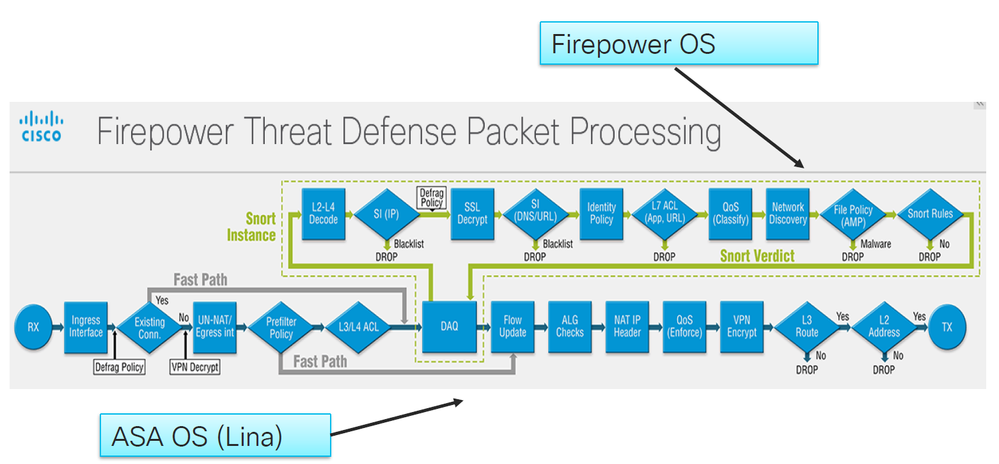
if that does not add an inspection policy just like any other ACP (in aka ACL).
here is traffic flow ( in case if you did not come across)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-26-2020 07:50 PM
I believe the old tool which required using an intermediate FMC instance had the option to select a prefilter policy. The current FMT does not.
Generally we use prefilter for traffic which is either a. explicitly trusted or b. does not lend itself to IPS inspection (e.g. encrypted traffic flowing through the appliance that does not require even the basic Security Intelligence (SI) scrub). I tend to put only things in the first category in prefilter since the SI action adds value even if you aren't able to inspect the unencrypted traffic.
FYI 6.7 will allow us to copy (or cut and paste) rules from an ACP into a prefilter policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2020 01:30 AM
I have migrated the rules manually now. Have some more basic questions.
1. In ASA lower security level traffic is automatically denied to higher security level and higher to lower is allowed. How can i replicate this after migrating to firepower ?
2. All my access policies are migrated with source zone and without any destination zone. Is destination zone necessary or optional? what happen to traffic without a destination zone ?
3. Have we any dates for 6.7 ? There are many rules that can reside in prefilter policy. If i set them as "trust" instead of allow will it help ?
4. How can i estimate that would there be any performance issued with the number of rules i have configured ? running FTD 4115 in HA with 6.6. Five contexts were migrated from ASA with total approx 3000 rules.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2020 02:31 AM
Q1. You can't replicate that in FTD. All interfaces have the same security
level which can't be changed. The concept of FTD is to use zones and
explicit rules to allow/deny. All interfaces within the same zone are
implicitly allowed to communicate. For different zones, the default action
is as per you ACP.
Q2. The need of the destination zone is subject to your policy. Just check
the use case if it's needed or not.
Q3. No idea about dates you can check that with your cisco AM. Trust and
allow are different. In prefilter trust will be processed by LINA (ASA
engine) without snort. Allow will pass the traffic to be examined against
ACP, snort, SI, etc.
Q4. 3000 rules are very low. I have used FPR1140 with 52k rules without
issues. The number of rules impacts the memory and can be verified using *show
memory detail*. Check the system free memory from the 1st section. The cpu
can be verified from *show cpu* and is impacted by connection per second.
**** please remember to rate useful posts
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide