- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: CDP does not carry the correct voice VLAN downloaded from ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
CDP does not carry the correct voice VLAN downloaded from ISE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2022 12:52 AM
Hi all,
i'm trying to understand a very strange behaviuor of a Catalyst 3650. The switch authenticates user by using ISE 2.7. I configured some authorization profile, on of which is dedicated for IP phones. This profile contains a voice VLAN assignments. For completness i'm using Polycom VVX 201. This polycom is CDP and LLDP capable.
When i attach the phone to the switch, it gest assign to a "welcome" vlan (voice vlan 201). This vlan is just an empty container, it does not have a L3 interface or DHCP relay config. At this point, the phone gets correct bauthenticated. ISE sends all the authorization profile informaztion within the Access-Accept packets. From now on the phone will be stuck in the welcome vlan besides been assign to the vlan associated to the authorization profile (707).
I've captured some packets with wireshark and i've seen that if CDP is enabled (on the switch interface or within the Polycom), switch send a CDP packet in which there is the "VoIP Vlan Reply" field set to 201 (instead of 707).
While turning off CDP (at the interface side with "no cdp enable" interface command or at the Polycom side) switch send an LLDP packets in which there is the corrct VLAN information (707).
Have you ever seen a scenario like this one?
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2022 10:35 AM
So ISE is configured with the "Voice Domain Permission" Attribute on the AuthZ profile? The "normal" way to do this to include only "Voice Domain Permission" in the AuthZ result and not any other dynamic VLAN assignments. Then the switch should allow the phone to join whatever vlan is configured in the switchport. What is your use-case for even using a "welcome" VLAN at all?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2022 11:52 PM
In my case there is a vlan voice configured in the interface (with the switchport voice vlan 201 command). However, this is only a welcome voice. I therefore need, using ISE, to pass the correct VLAN (701) once the phone has authenticated
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2022 12:59 AM
Voice VLAN cannot be overriden by AAA. You can do AAA VLAN override in the DATA domain only.
Potentiall a dynamic interface template could be used. ISE can return an Interface Template that contains commands that will overwrite what's already on the ports. We use this for cases like Cisco APs running Flex Connect, where the port starts out as an Access Port, and then ISE returns an Interface Template to make that port become a trunk, wth allowed VLANs, Native VLAN etc. Perhaps you can steer the port to use a dynamic voice VLAN using that method. The config only stays on the port for the duration of the session. You might have to use the command "show derived int xxx" instead of "show run int xxx" to see the currently active config.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2022 01:20 AM - edited 07-12-2022 01:26 AM
So if I dont't want to use the template method how can i achieve my objective? Can i statically configure on switch interface only Data vlan and then ISE sends the voice vlan?
I searched some info on interface tamplates and, as far as i understood this templates have to be defined inside the switch and not in ISE. So if this is true this is not a scalable architecture beacuse you can not globally manage this config from a central node (ISE). Am i wrong?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2022 03:10 AM
Hi Marco,
Sending any VLAN ID/Name in an ISE Authorization Profile will never achieve the goal of overriding the voice vlan. The voice vlan on a Cisco switch is a bit of a special thing (called "Auxilliary vlan" amongst other things) - it's like doing trunking without explicitly setting up trunking on the port. Or like trunking, but with only one allowed vlan that can be tagged (the voice vlan) and then the native vlan is the untagged traffic (e.g the PC attached to the phone).
Regarding Interface Templates - I believe this will solve your problem. But as you mentioned, the name returned by ISE refers to an existing Interface Template on the switch. I am not aware of a way to download those Interface Templates via ISE (like we do with dACLs).
What's the reason/purpose of VLAN 201 in your config? Should any phone ever use that VLAN?
Why can't you set the voice VLAN per interface? Why does it have to be overridden by AAA? I'm just asking, to try and understand the use case better.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2022 05:24 AM
First of all thank you for all the precious information that you are giving to me. I'm an associate figure so i don't know as much you do.
1) You said that "Sending any VLAN ID/Name in an ISE Authorization Profile will never achieve the goal of overriding the voice vlan".
I configured the voice vlan 707 in ISE (with Voice Domain Permission coption enabled) and the Polycom device is able to take that VLAN ID sometimes. The previous cases are particoular cases which represents the 30% of the cases. For the 70% case the Polycom can obtain a VLAN from ISE. So why doy you claim that this shouldn't work?
2) VLAN 201 has the same purpose of DATA VLAN 200. When IP phone is attached to the switch it is assigned to a parking vlan voice. This vlan can be considered as fictitious because traffic will not be forwarded anywhere. I just created this vlan by using
vlan 201
name WELCOME_VLANand then using it with the command
switchport voice vlan 201In order to allow an IP phone to generates traffic on the network it has first to gets authenticated. By assigning it to this vlan, the phone cannot interact with anyone.
Once the IP phone gets authenticated it is assigned to the correct vlan (707) and then can send/receive traffic to/from other IP phones.
Do you suggest other metods?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2022 01:34 PM - edited 07-12-2022 01:45 PM
Hello Marco,
There are others who have asked the same question - e.g this posting from last year.
I tried this in the lab for a long time until I also realised that dynamic voice VLAN assignment doesn't work. Perhaps it's due to the way that the VLAN ID is conveyed to the phone via CDP/LLDP - and if the first CDP gets to the phone to say "hey phone, use VLAN 201" and then the phone tags frames with 201, whilst the port has been set to vlan 700. Subsequent CDP messages are potentially still sending 201 because that is what is hard coded on the switch config. I don't know why.
Suggestion is to set the voice vlan according to the VLAN designation for that switch and authenticate the voice devices in the best manner that you can (e.g. 802.1X or MAB+Profiling). It doesn't harm having a voice vlan configured on a port where there are no phones connected. In Multi-domain mode each domain MUST be authenticated - therefore someone trying to hack their way into the voice VLAN will have just as hard a time as with any other VLAN. And since you have segmented the network using DATA and VOICE VLANs, you should have some security that keeps devices in their respective domains (firewall, ACL, etc.)
If you really want that Welcome voice VLAN concept, then you could achieve your goals perhaps with the interface template. Just try it. Create one template on the switch that contains only the command "switchport voice vlan 707" and have ISE return this template in the AuthZ. With any luck the switch will generate the corresponding CDP that will then inform the phone to use this VLAN, and not the welcome VLAN hard coded in the show run. You would then use a "show derived int xxx" to view the dynamic interface config.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2022 04:24 AM
Thanks Arne, i'll try to implement your solution. I hope it will work. Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2022 08:59 AM
So i configured a simple template like you said. I used the following commands:
template TEST_NAC
switchport voice vlan 707Thein in ISE (in AuthZ profile page) i turned off the VLAN option while i leaved checked Voice Domain Permission and Interface Template options. After gest authenticated, using "show deriv int g1/0/46" i saw that the voice vlan was replaced with the one defined within the template. All the rest of the interface config hasn't been modified. When i unplugged the phone i saw however that the "show deriv int g1/0/46" command showed again the vlan configured in the template (and not the original one which is 201).
So now i'm a bit confused. I want that the template is attached to an interface for the session time period. When the device disconnect, it should be removed from that interface.
Also i tried to unbind manually the template from the interface but i didn't make it.
Could you please help me with these two doubts? Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2022 03:21 PM
To expand on what @ahollifield stated, the dynamic VLAN assignment pushed from ISE only applies to the Data VLAN. The Voice VLAN works differently due to the separation of the DATA and VOICE domains on the switch. When enabled for NAC, the RADIUS server is configured to return the "Voice Domain Permission" (device-traffic-class=voice) attribute to allow the phone to use the Voice VLAN configured on the switchport.
I would suggest having a look at the Multi-Domain Auth overview in the following document to understand this separation.
IP Telephony for 802.1X Design Guide
While the content is quite old and based on the legacy IBNS model, the concept of the DATA/VOICE domain function is still valid for current Cisco Catalyst switch models. The current recommendation (and default) for Multi-Auth host mode also works in a similar fashion to MDA while allowing more than one endpoint on the DATA domain.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2022 09:19 PM
I recently learned a thing about the voice-permission AV attribute that we always push via ISE. It's how we "always do it" and how it's always documented. When we push this attribute during Authorization for the Endpoint, then it tells the switch port to allow traffic on the voice VLAN only, and to not allow that same MAC address to communicate in the DATA domain. Seems odd to say this - but what I really learned, is that you can happily operate voice handsets without the use of the voice-permission attribute. In other words, phones can operate quite adequately and correctly without the voice permission attribute.
Case in point - Avaya handets. You can boot them with DHCP options that tell them which 802.1Q tag to use for the phone comms. And when using NAC, you'll see the phone's MAC in the DATA domain, as well as the attached PC in the DATA domain (in this case using multi-auth, and not multi-domain host mode). PC is in VLAN A and phone is in VLAN B. Happy days.
Although this might be a special case, it highlights the fact that the switchport "voice vlan xxx" is independent of this magical VOICE Domain concept. The "voice vlan xxx" command simply maps the correct 802.1X tag sent my the phone (if the phone is configured accordingly) to create a separate session. The voice permission attribute then "jails" the MAC address to ensure that the MAC address cannot be used on untagged traffic.
I've never seen it described this way, but this has been my recent experience after two days of customer deep dive on the issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2022 01:16 AM
Thanks for your detailed reply. I will show below what i've foun in the meanwhile.
First i reply to MHM. I tried to cut the "authentication open" from the config but the behaviour didn't change.
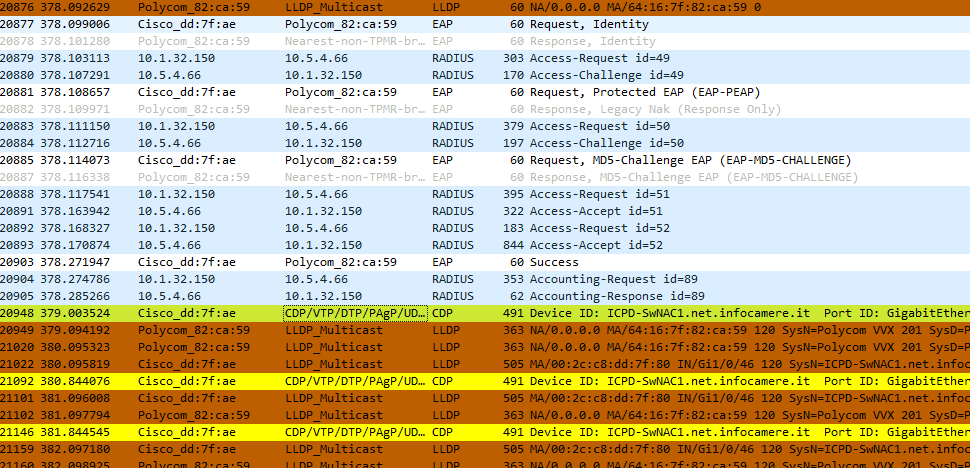
Let's consider first scenario in which both the interface and the Polycom have CDP enabled. The config of the interface on which Polycom is attached to is the following:
switchport access vlan 200
switchport mode access
switchport voice vlan 201
device-tracking attach-policy DeviceTrackingPolicy
ip access-group WELCOMEACL in
authentication event fail retry 3 action next-method
authentication host-mode multi-auth
authentication open
authentication order dot1x mab
authentication priority dot1x mab
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
authentication timer restart 10
authentication timer inactivity server
mab
dot1x pae authenticator
dot1x timeout quiet-period 18
dot1x timeout tx-period 1
dot1x max-reauth-req 3
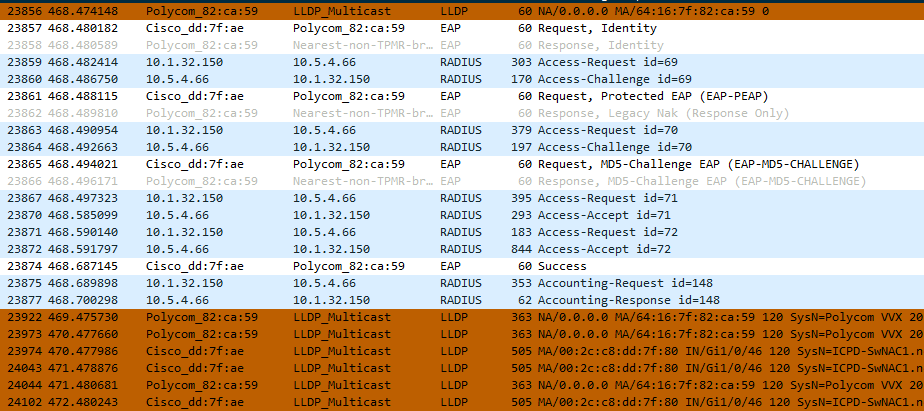
spanning-tree portfastThe traffic capture is the following
After packet n. 20903 the device is authenticated. At this point i expect to see that the packet n. 20948 (CDP packet) contains vlan 707. Instead, field (Voice Vlan Reply" contains vlan 201 (so the welcome VLAN). For me this has no sense because the switch should send tha vlan jnust downloaded from ISE (707). Btw i verified that ISE sends the corrects parameters of AuthZ profile. Note that before Polycom gets authenticated (so before packet n. 20903) the switch didn't sends any CDP/LLDP packet to Polycom to inform it that it belongs to VLAN 201.
In the second scenario i disabled CDP only on switch interface. Also in this case i started to see the seame behaviour like the previous one, ie switch send thhrough LLDP voice vlan 201 insted of 707.
In this case, like the previous one there no packet sent by the switch that inform Polycom to stay in VLAN 201 before the authentication is successful.
So both CDP and LLDP didn't assign the corret AuthZ VLAN to IP phone. In my opinion this is due to the fact that the switch does not send any voice vlan information (vVLAN 201) prior the authentication. In this way, even if the switch receive the correct VLAN from ISE, it send to Polycom the VLAN configured on the interface.
What do you think?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2022 10:28 AM
I see lldp before cdp?
Disbale lldp and check again, with and without auth open.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2022 04:23 AM
I could disabled LLDP, however lldp cannot be turne off in a production environment. SO iven if it would works, it could not be possibile to implement this solution. I will try with the template solution.
Thanks for you reply
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide