- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Cisco ACS Migration to ISE - Identity policy
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2022 02:30 PM
Hello,
Im planning on migrating from ACS to ISE and i cant find the same feature in ISE as i've used in ACS.
My devices is using tacacs for authentication, and most of the users is mostly authenticated using external ad groups or local users in ACS. But i have a special case were i need to forward the request to an external radius server.
In ACS i've been able to do this with a identity policy's that checks if a username starts with xxx_, then identity equals my radius server.
Im trying to do the same in Cisco ISE, but i cant figure it out. Is this feature missing, or how am i going about implementing it?
Traffic flow:
Device -> Tacacs+ -> Cisco ISE -> Radius -> External Radius server
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2022 03:23 PM
Those return attributes are only used as matching conditions in the AuthZ Policies to provide differentiated access (T+ Command Sets, Shell Profiles, etc).
The connection between the NAD and ISE (and vice-versa) is using TACACS+ which is a different protocol than RADIUS and does not support the same attributes. RADIUS attributes returned by the external RADIUS server to ISE cannot be sent to the NAD via TACACS+. This would be no different between ACS and ISE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2022 04:03 PM
TACACS+ and RADIUS are different protocols that handle Authentication and Authorization in different ways. ISE cannot translate TACACS+ to RADIUS (I doubt ACS can either), so you cannot configure a RADIUS Proxy service in a Device Admin Policy Set. I suspect you are simply using the external server as a RADIUS Token server.
If this is what you are doing in ACS, you should be able to achieve the same in ISE using these steps:
- Configure the RADIUS Token server
- In your Device Admin Policy Set, create an Authentication Policy that matches on something like 'Network Access·UserName Starts with xxx_' and Uses your RADIUS Token server
- Create your Authorization Policies with matching conditions based on the attribute_name that is returned by the RADIUS Token server (e.g. RADIUS_Token·CiscoSecure-Group-Id Equals GroupA)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2022 03:57 PM - edited 06-26-2022 04:31 PM
Hello,
Thanks for the reply,
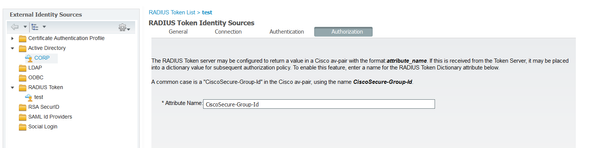
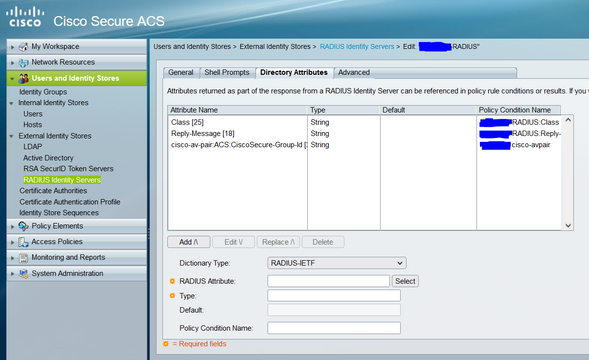
Ive tried to set up the Radius Token Server, but it only seems that i can add one attribute the standard ciscosecure-group-id
While in Cisco ACS i have the possibility to add multiple attributes:
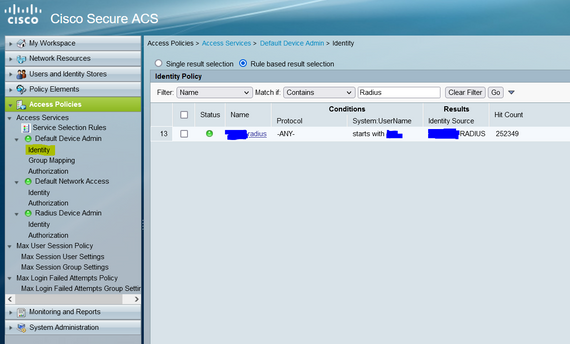
I then access this server trough an identity policy:
I need to return the class, and reply-message also including the cisco-av-pair.
If i have set up the a rule to match on the cisco av pair sent from the external radius server, will other attributes also be contained, and reaching the network device?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2022 07:18 PM
I'm not sure I understand what you are trying to do here.
Are you saying that the external RADIUS server returns specific attribute-value pairs for RADIUS Class [25] and Reply-Message [18] based on some policy logic and ACS uses these returned RADIUS values as matching conditions in the Device Admin policies (Authentication and/or Authorization) to provide different TACACS+ responses (Shell Profile, Command Sets, etc) for different users?
If that's the case, then there is no way to do this with ISE AFAIK. The RADIUS Token response only provides the configuration of one attribute and the Device Admin policy sets do not provide the ability to match on any RADIUS attributes except the one configured in the RADIUS Token server section.
If you need to match on those RADIUS attributes for differentiated access, you might instead need to use RADIUS between the NAD and ISE and use the External RADIUS Servers and normal Policy Sets (RADIUS-based) instead of Device Admin (TACACS+).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2022 07:32 AM - edited 06-27-2022 07:35 AM
Hello, i think i probably have not understood correctly how the attributes works.
Its fine to only match the policy on ciscosecure-group-id, i dont need more granulary controll than this.
I just thought i needed the class and reply-message attribute added for the NAD to recieve the attributes from the radius server. But as i understand it now, the attributes we add here, is just to help make policies, correct?
So if i make a policy that matches on the correct group-id, the other attributes should be sent to the device also?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2022 03:23 PM
Those return attributes are only used as matching conditions in the AuthZ Policies to provide differentiated access (T+ Command Sets, Shell Profiles, etc).
The connection between the NAD and ISE (and vice-versa) is using TACACS+ which is a different protocol than RADIUS and does not support the same attributes. RADIUS attributes returned by the external RADIUS server to ISE cannot be sent to the NAD via TACACS+. This would be no different between ACS and ISE.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide