- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Cisco ISE 2.4 LDAP Authorization Not Working as Expected
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-13-2019 04:22 AM
I am having some issues with a policy authorizing staff & students against our external identity source LDAP.
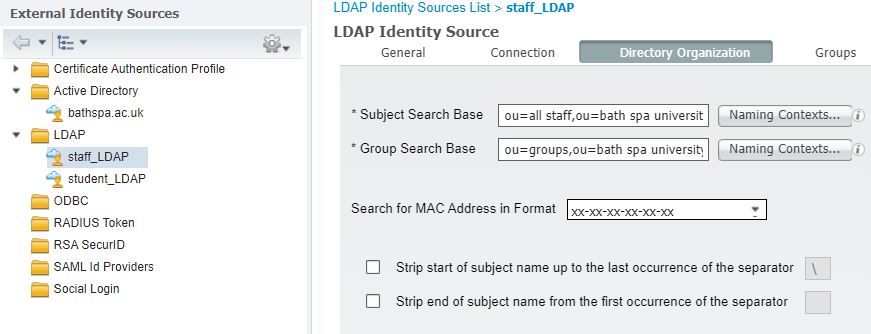
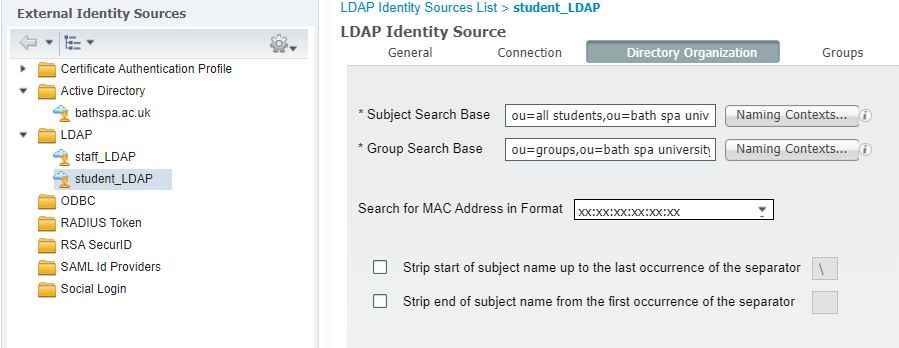
We have added two LDAP identity sources one that looks at the ou for all staff, the other looks at the ou for all students.
staff_LDAP
student_LDAP
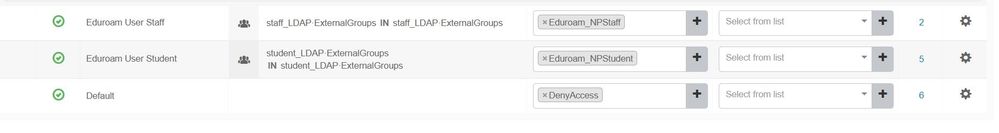
The authorization policies look at the ExternalGroups staff_LDAP & student_LDAP
Can anyone explain why all our staff are matching the student policy & students are matching the staff policy?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2019 08:26 AM
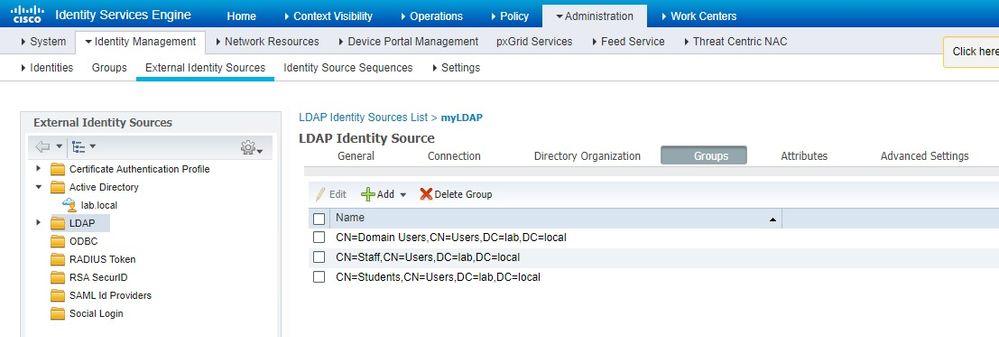
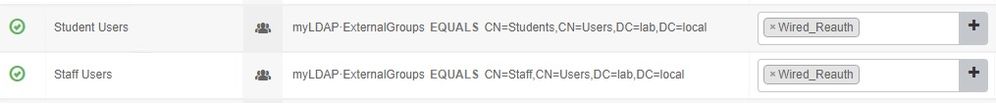
Now that I look closer at your authorization rules, you need to change how you are looking up groups. In your LDAP identity source configuration, there is a Groups tab. In there, hit the button to select groups from directory. Grab the groups that you want to be available in your authorization rules. Save that.
Now in your authorization rule, you would configure it similar to "myLDAP:ExternalGroups EQUALS StaffGroup" or whatever your group name is for Staff. Then same for the Student rule. You really don't need two different LDAP identity sources if it is the same server. And for your search base DN's, just make sure it is high enough up in the hierarchy to catch for both types of users. In other words, just move up one level for your search base DN's. Whatever is the common part of the full distinguishedName between a staff user and student user. Take a look at the screenshots below for examples:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2019 04:57 AM
Typically the step data on the detailed live log will show some hints. There are other settings in play such as identity sequence, LDAP external groups, and policy conditions not shown that could affect the decision.
However, it looks to be same LDAP server for both staff and students, have you considered just creating on LDAP for both use cases?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2019 07:01 AM
Your "Group Search Base" is the same on both servers and your authorization policy rules are looking for group membership. Your identity search base is unique but that would be for authenticating the user or looking for user-specific attributes. Since you are looking for group membership, either will match with the same "Group Search Base".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2019 05:06 AM
Thanks, that does kind of make sense, but how is it that ALL staff were matching the student profile & ALL students were matching the staff profile. If they could match either I would have expected them all to match the first policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2019 08:26 AM
Now that I look closer at your authorization rules, you need to change how you are looking up groups. In your LDAP identity source configuration, there is a Groups tab. In there, hit the button to select groups from directory. Grab the groups that you want to be available in your authorization rules. Save that.
Now in your authorization rule, you would configure it similar to "myLDAP:ExternalGroups EQUALS StaffGroup" or whatever your group name is for Staff. Then same for the Student rule. You really don't need two different LDAP identity sources if it is the same server. And for your search base DN's, just make sure it is high enough up in the hierarchy to catch for both types of users. In other words, just move up one level for your search base DN's. Whatever is the common part of the full distinguishedName between a staff user and student user. Take a look at the screenshots below for examples:
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide