- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Cisco ISE 2.4 -- Problem to segment G1 to PortalGuest only
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2020 08:07 AM
Hi Everyone
I have a task to create a new interface (G1) under Ise to attempt just for PortalGuest, and I have some problem.
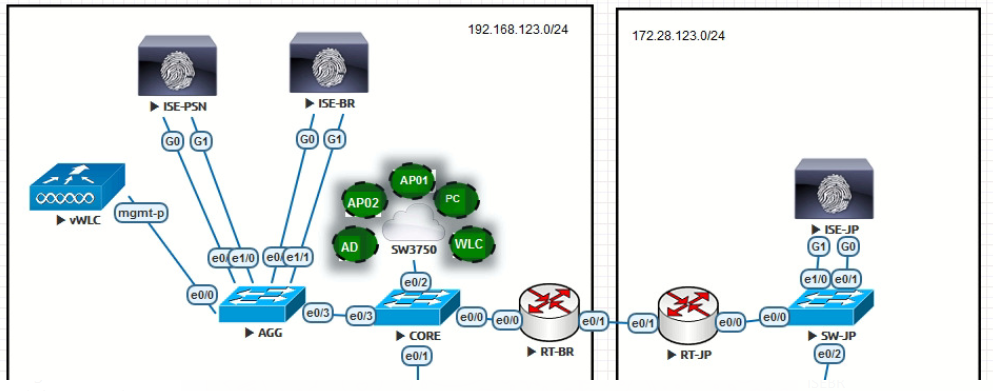
This is my Topology:
ISEBR
Gi0 192.168.123.25/24
Gi1 192.168.185.25/24 (PortalGuest)
ISEPSN
Gi0 192.168.123.26/24Gi1
192.168.185.26/24 (PortalGuest)
ISEJP
Gi0 172.28.123.25/24
Gi1 172.28.185.25/24 (PortalGuest)
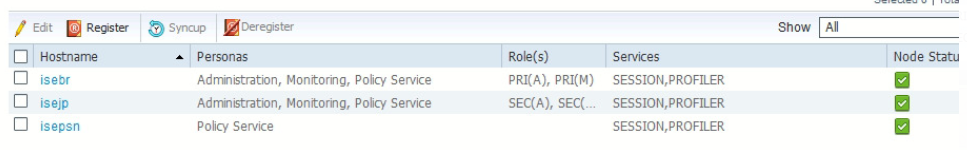
HA
ISEBR (Primary) and ISEJP (Secondary)
Both (PAN+MGT+PSN)
When I click under portal test, the URL just try push me Ise primary or ISE secondary G0 Interface only
Someone already have this problem?
Solved! Go to Solution.
- Labels:
-
Guest
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2021 09:50 PM
Hi,
Greg gave you a sample how to apply the ip host command I was talking about.
Just to clarify. In my deployments, i use 3 interfaces all the time:
- gig0 as default management
- gig1 for radius/tacacs
- gig2 for portals.
On gig1 and 2, i use anycast to avoid multiple fqdns (1 per host). If you have any load balancer solution you can achieve the same thing.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2020 08:50 PM
You mean when you click on portal test button, it opens a new page using your gig0 fqdn?
Have you configured the ip host command on cli to define a specific fqdn for the gig1 interface?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2021 12:40 PM
Hi Francesco,
I wanted to also try using other interfaces for data traffic meanwhile letting gig0 for management only, but I am not able to find guides on the required configuration steps.
Can u please help me find a guide on how to configure other interfaces other than gig0 to handle data traffic such as wired data traffic or wireless guest traffic, meanwhile leaving gig0 only for management traffic?
I don't think the official guide explains it as a straight forward UseCase and all tutorials I have seen use Gig0 only.
You advice would be highly appreciated.
Best,
L
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2021 07:44 PM
Hi
Other interfaces are configured on the CLI. Connect to ssh on your ISE, then go to conf t and under interface configuration using commands interface gig1 for example. You can assign an ip address. Then on conf t mode (not under interface config), you can add a default route pointing towards the gateway of this new interface.
In conf t mode, you'll need to configure a fqdn that ise will send out when users reaching this interface for services using the command ip host.
Be careful, you can have 1 fqdn per interface ip and by default it must be different on all your nodes as you'll have a different IP per node per interface.
To simplify this, you can have an anycast architecture, so same ip and same fqdn on all nodes. Users will access the closest ise node based on the routing.
What do you mean but 1 interface for wired, 1 for wireless? Usually, you have 1 interface for radius/tacacs authentication and 1 for portals. At least, this is the way i deploy them.
Not found a clear documentation, showing all this in 1 global doc. However if you search piece by piece, you'll have multiple documentation explaining each part separately.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2021 01:17 AM - edited 01-12-2021 01:35 AM
Hi Francesco,
Thank you for the information provided. Much appreciated.
Based on your information I am assuming the following:
Two ISE ports are connected to Switch that leads towards Internet. One of them, holding management traffic and Radius/TACACS+, meanwhile the other holding portals traffic.
For the Management, Radius/TACACS+ traffic, its the default port of Gig0 that we configure during the base setup.
Meanwhile for the Portals Interface, we check the port in the portals modification when we setup the portals, and that is when the portals traffic gets passed through that traffic.
Now, I am not sure I have seen how to add an FQDN to an interface somewhere so far, but I will be after that today. If you have something, please share that with me.
If you are a blogger and have something similar posted somewhere, I would be highly interested to read that.
Thank you and best wishes,
L
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2021 06:49 PM
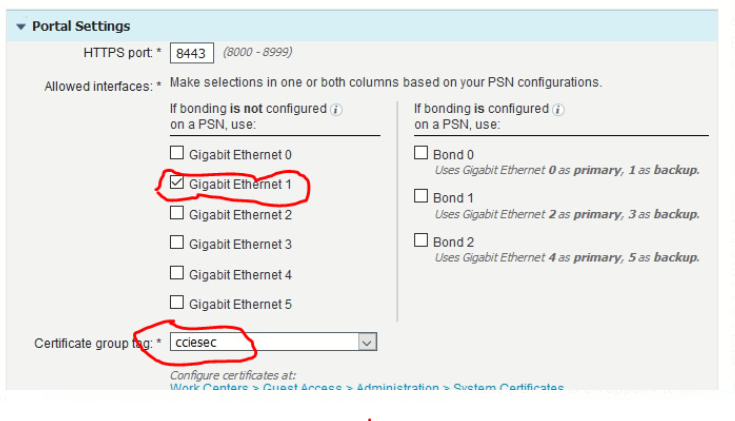
As @Francesco Molino mentioned, you need to create an FQDN alias using the 'ip host' command on the ISE node when using a separate interface for guest portal traffic. The FQDN configured is then the one that is presented to the client in the URL redirect sent by the PSN that handles the initial RADIUS session.
The syntax is as follows. A unique FQDN must be used on each PSN and restarting the app server service will be required.
(config)# ip host <gig1_ip_address> <portal hostname|FQDN>
For more information on traffic flows and best practices, see the following Cisco Live presentation.
Advanced ISE Architect, Design and Scale ISE for your production networks - BRKSEC-3432
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2021 11:44 PM
Hi Greg,
Thank you. Information provided is much appreciated.
Best,
L
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2021 09:50 PM
Hi,
Greg gave you a sample how to apply the ip host command I was talking about.
Just to clarify. In my deployments, i use 3 interfaces all the time:
- gig0 as default management
- gig1 for radius/tacacs
- gig2 for portals.
On gig1 and 2, i use anycast to avoid multiple fqdns (1 per host). If you have any load balancer solution you can achieve the same thing.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2021 11:45 PM
Hi Francesco,
Thank you. Information provided is much appreciated.
Best,
L
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: