- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Cisco ISE 3.0 as a NAC/NIC level settings.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2021 10:52 PM
Team,
We have been doing a PoC on the Cisco ISE as a NAC.
Our use case was identifying if the laptop is a corporate owned laptop and if yes allow it the default full access VLAN. If not, give it guest VLAN with limited access.
This has been achieve but the catch here is setting on the NIC card adapters had to be done additionally.
Is there any way we can achieve the same end goal without touching anything on the end users laptop, specifically in the NIC level?
What other mode of testing have you people done and implemented this?
Regards,
N!!
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2021 12:49 PM
Easy Connect or Passive Identity features can provide what you would like.
https://community.cisco.com/t5/security-documents/ise-easy-connect/ta-p/3638861
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2021 05:36 AM
Is there any way we can achieve the same end goal without touching anything on the end users laptop, specifically in the NIC level?
-I am not sure I follow what you mean. Can you elaborate so the community can better assist you? Do you mean supplicant configuration on the clients? NIC IPv4 config? You should not have to reconfigure the NIC when performing posturing or just simple onboarding.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2021 07:28 AM
Hello Mike,
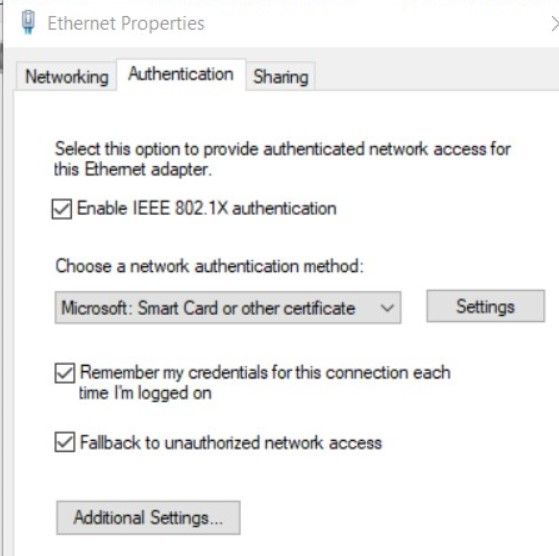
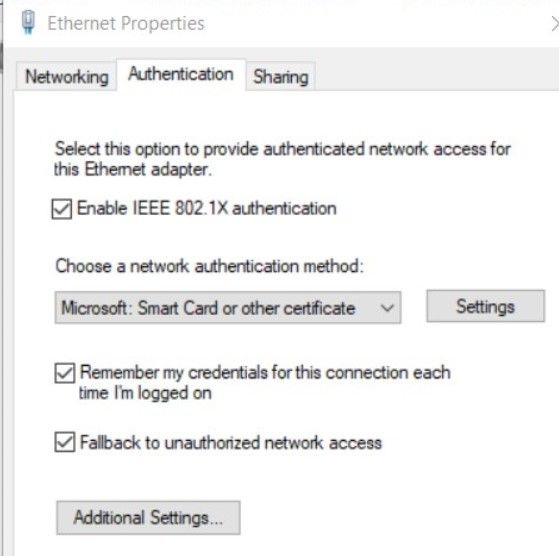
Sorry for responding late. The below setting is what we needed to make on the NIC adapter:
So what I meant was other than doing this there is no way we can do NAC. (This is not an issue for us but was trying to look at alternatives)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2021 07:26 AM
There are 3 components in a network access control solution:
1) endpoint : the client wanting network access. for 802.1X, it must authenticate using a "supplicant" which is a fancy word for client software which can either be part of the native OS or a separate software like AnyConnect NAM.
2) network device : acts as the authenticator of the endpoint with the 802.1X protocol (wired and wireless) and enforces network access policy from the authentication server
3) authentication server : this is ISE which both authenticates and authorizes the endpoint, assuming it has an 802.1X supplicant and it is configured properly.
Configuration of the 802.1X supplicants for corporate devices at scale should be done via Windows Active Directory Group Policy Objects (GPOs) or Mobile Device Management (MDM) software.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2021 07:36 AM
Hello,
thanks for the response.
Yes, agreed. I was just checking if there are alternate methods. e.g. on reading we found that for MAC books we can do a Jamf integration.
Anything similar for windows?
What I want to check if we can avid is the NIC level setting on every laptop. (no doubt they can be rolled out using AD)
The same picture I have pasted in the above post:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2021 05:08 PM
Q: Anything similar for windows?
A: If the computers are joined to the domain, the best way to push this configuration is via Group Policy. This is how 100% of the large enterprise customers I've worked with have deployed 802.1x on their fleet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2021 12:49 PM
Easy Connect or Passive Identity features can provide what you would like.
https://community.cisco.com/t5/security-documents/ise-easy-connect/ta-p/3638861
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide