- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Cisco ISE SNS-3655 deployment in DMZ as well as Internal NW
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2020 12:04 AM
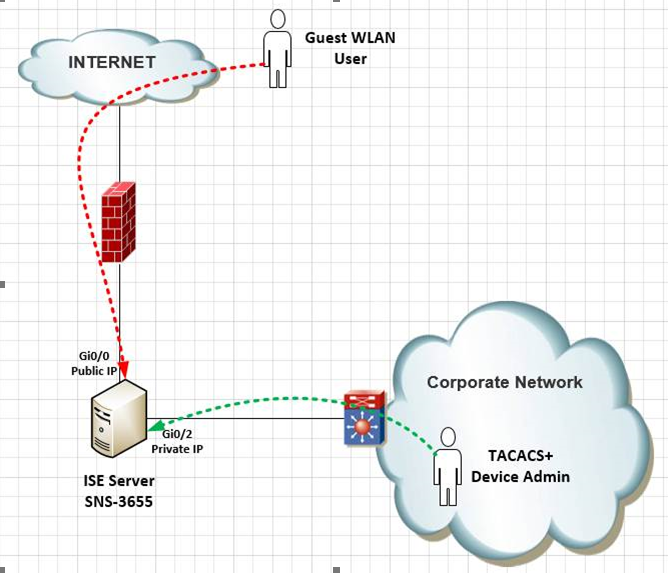
As you see above diagram, we would like to use the ISE server for multiple purposes, for example currently it is acting as authentication platform for providing access to our Guest WLAN users. And its port Gi0/0 is placed in DMZ and has public IP so Guest WLAN users can connect it over internet.
So in addition to that we would like to use the same ISE box as TACACS+ server for our internal corporate network devices as well.
Thus, my questions are:
- Is it possible to setup such thing?
- How safe it is to setup such case? Would the ISE box be compromised via its DMZ and attacker can enter our private network, or is the ISE box safe enough to handle such design?
- Is it possible to setup redundancy for the TACACS+ in above setup? As currently the guest portal is setup in redundancy, so can the same redundancy can be used to setup redundancy for TACACS+ functionality?
- We have existing ISE server running as VM on Cisco UCS chassis and we have there some base and device admin licenses. So is it possible to transfer those base and device admin licenses from the VM ISE to the physical SNS-3655 ISE box?
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-02-2020 09:02 PM
> Is it possible to setup such thing?
Yes. Please see the ISE Guest Access Prescriptive Deployment Guide > ISE Deployment Model Considerations for your options.
> How safe it is to setup such case? Would the ISE box be compromised via its DMZ and attacker can enter our private network, or is the ISE box safe enough to handle such design?
Depending on your firewall/DMZ configuration and the ports you open to ISE it is very possible. Known vulnerabilities can change at anytime.
> Is it possible to setup redundancy for the TACACS+ in above setup? As currently the guest portal is setup in redundancy, so can the same redundancy can be used to setup redundancy for TACACS+ functionality?
Redundancy would mean having 2 ISE nodes. You could have both ISE nodes in the DMZ, out of the DMZ or one in and one out. As long as both are reachable by your desired network devices, that is redundancy.
> We have existing ISE server running as VM on Cisco UCS chassis and we have there some base and device admin licenses. So is it possible to transfer those base and device admin licenses from the VM ISE to the physical SNS-3655 ISE box?
ISE Base/Plus/Apex licenses are done per deployment. You don't need to move the licenses unless the "physical SNS-3655" is a separate deployment from the other nodes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2020 01:20 AM
High level this solution is feasible - if you require to be based on the diagram.
DMZ is always exposed to the Internet, and Your FW only allowed required ports , but ISE has not patched as expected, and backhole hole vulnerable - attached / hacker get a chance, this is the case all public network also, so Security patching is a must and audit rquired when you hosting system in DMZ.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-02-2020 09:02 PM
> Is it possible to setup such thing?
Yes. Please see the ISE Guest Access Prescriptive Deployment Guide > ISE Deployment Model Considerations for your options.
> How safe it is to setup such case? Would the ISE box be compromised via its DMZ and attacker can enter our private network, or is the ISE box safe enough to handle such design?
Depending on your firewall/DMZ configuration and the ports you open to ISE it is very possible. Known vulnerabilities can change at anytime.
> Is it possible to setup redundancy for the TACACS+ in above setup? As currently the guest portal is setup in redundancy, so can the same redundancy can be used to setup redundancy for TACACS+ functionality?
Redundancy would mean having 2 ISE nodes. You could have both ISE nodes in the DMZ, out of the DMZ or one in and one out. As long as both are reachable by your desired network devices, that is redundancy.
> We have existing ISE server running as VM on Cisco UCS chassis and we have there some base and device admin licenses. So is it possible to transfer those base and device admin licenses from the VM ISE to the physical SNS-3655 ISE box?
ISE Base/Plus/Apex licenses are done per deployment. You don't need to move the licenses unless the "physical SNS-3655" is a separate deployment from the other nodes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-02-2020 11:32 PM
Thanks Thomas for your valuable inputs!
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: