- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Eap chaining with dot1x
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Eap chaining with dot1x
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2018 12:22 PM - edited 02-21-2020 10:55 AM
Dears,
- my eap chaining Is working perfect, whenever user logoff i m not able to remote desktop pc, when i enter a command sh auth see int gig1/0/2 detail there is no ip on the port, so what is the solution for this type of scenario's
- i want to setup dot1x with certificate authentication with eap-tls anybody can route me to the configuration example.
Please find the attached eap chaining conditions
- Labels:
-
Other NAC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2018 01:07 PM - edited 05-08-2018 01:10 PM
Hi Adamgibs7
1-my eap chaining Is working perfect, whenever user logoff i m not able to remote desktop pc, when i enter a command sh auth see int gig1/0/2 detail there is no ip on the port, so what is the solution for this type of scenario's.
What Authorization is being pushed under this state within Cisco ISE (one of the conditions checks should be EAP-Chaining result == User failed and machine succeeded ) so if he hit this authz rule for Machine only authentication what authorization permission are you pushing (DACL, Vlan assignment,...etc) and if pushing DACL does exist or created in Cisco ISE and if created how many ACEs are inside this DACL (some platform may not process more than 64 ACE in a DACL (platform dependent?. in your switch do you have Device tracking enabled?
Please share Show Auth sess int gix/0/x details and logs from Cisco ISE
2-i want to setup dot1x with certificate authentication with eap-tls anybody can route me to the configuration example.
for EAP-TLS assuming that you want server and client side TLS authentication, Then you would need the client to have its own certificate created by some Root CA that Cisco ISE has to trust and when Cisco ISE present its own EAP certificate to the client, the client has to trust the Root CA that signed that EAP certificate
The main concept for successful Certificate Authentication against Cisco ISE is that:
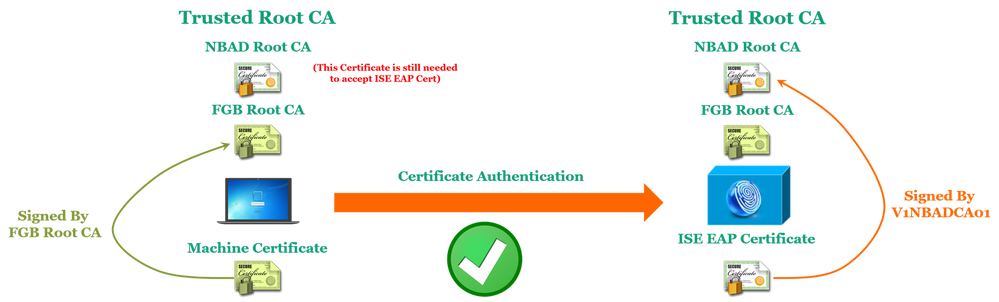
- The CA signer of the machines certificates has to be in the ISE Trusted Root Certificates.
- The CA signer of the ISE EAP Certificate has to be in the Machine Trusted Root Certificates.
So based on the above concept the following explains a successful authentication scenarios:
Both Machine and ISE certificates are signed by the same Root CA.
Machine and ISE certificates are signed by the different Root CAs
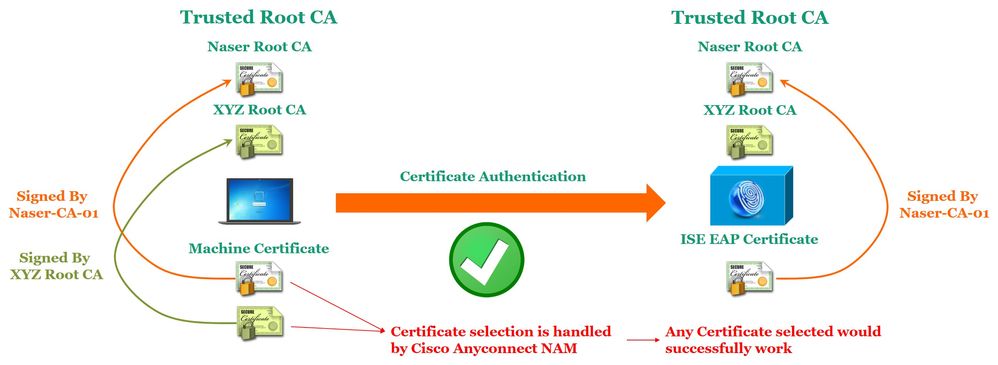
Machine have multiple certificates from same and different CA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2018 01:32 PM
Thanks for the reply
What Authorization is being pushed under this state within Cisco ISE (one of the conditions checks should be EAP-Chaining result == User failed and machine succeeded ) so if he hit this authz rule for Machine only authentication what authorization permission are you pushing (DACL, Vlan assignment,...etc) and if pushing DACL does exist or created in Cisco ISE and if created how many ACEs are inside this DACL (some platform may not process more than 64 ACE in a DACL (platform dependent?. in your switch do you have Device tracking enabled
i have 2 policies one is machine passed and user passed and the another is user failed machine passed, the top most is user passed machine passed and below that is machine passed user failed,
still i m not able to get the IP address,
there is no issue when the user is logged in
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: