- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: eap-mschapv2/peap profile issue with Apple iOS11 and ISE 2.0.0.306
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2017 12:46 AM
Morning All,
Hoping you can help I have raised this with Apple but without paying for cross platform support they are unwilling to help.
In our network we use Cisco ISE and as as part of this we register our iPads with the BYOD functions which downloads and installs a WiFi profile containing the network SSID, PEAP protocol, auto join setting and a certificate in order to perform machine authentication using eap-mschapv2 .
Since upgrading to iOS11 (currently running iOS 11.1 bata) when users change their Active Directory password the iPad are kicked of the network and on the iPad request for a password to be entered however the box presented has Username & Identity. The identity looks for a device identity certificate as if you use eap-tls not eap-mschapv2.
Currently the only work around we have is to remove the WiFi profile and enter a password each time it is changed but this defeats the purpose of machine level authentication.
Our iPads on iOS10* work as expected when a users changes their AD password the iPad remains connected and users not prompted to change it on the iPad.
ISE Details: Vesion - 2.0.0.306, nstalled Patches: 4
Also attached logs from ISE
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2017 07:53 AM
Hello, I had the same issue after upgrading from 1.4 to 2.0.0.306, installing patch-5 last night fixed the IOS issue, and windows 10 issues as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2017 07:00 AM
Hi James,
Have you considered migrating towards certificate based authentication? Using certificates would mitigate this problem as well as provide a higher level of security. You could leverage the CA in ISE so you wouldn't have to integrate with a 3rd party PKI system.
Regards,
-Tim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2017 12:06 PM
Good evening Tim thank you for the reply,
It may be a misunderstanding from my part but currently with devices running iOS10 if a user changes their password they don't need to re-enter a new password on the iPad which I though was because of a certificate when using EAP-MSCHAPv2 ?
Although i'm unable to determine it look like iOS11 has an issue with EAP-MSCHAPv2 and tries to use EAP-TLS as when a user changes their password the authentication fails and the iPads look for a device identity certificate.
If we were to change the authentication method would you recommend EAP-TLS ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2017 07:55 AM
Does the mode give you an option for username and password? Maybe automatic is assuming certificate.
Warning: I either dictated this to my device, or typed it with my thumbs. Erroneous words are a feature, not a typo.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2017 12:18 PM
Good evening George,
The only options under mode are Automatic and EAP-TLS which is what lead me to believe it may be an issue with iOS11 as we don't need to re-enter AD password once it changed in iOS10.
Not sure if the issue is iOS 11 can no longer determine the payload sent within the Wi-Fi profile or if iOS11 can no longer support EAP-MSCHAPv2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2017 01:02 PM
Are you still needing any help on this?
If so, please elaborate what credentials entered in the configuration profile to effect the machine level authentication.
Microsoft Windows operating systems are ones that have a separate auth for computer and user accounts, but not most of other client operating systems, such as Apple iOS devices.
From your iselog.txt, it seems you are using an AD user and password to perform the authentication. So, I am guessing that is the one which has password changed/reset and so the device prompting to enter a new info. In the past, we've seen Apple client OS has some not intuitive user interactions. Your Apple iOS 10 experience seems odd to me. While Microsoft AD usually allows the users to use the old passwords for a while, eventually it should allow only the new ones.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2017 07:51 AM
Afternoon Hslai,
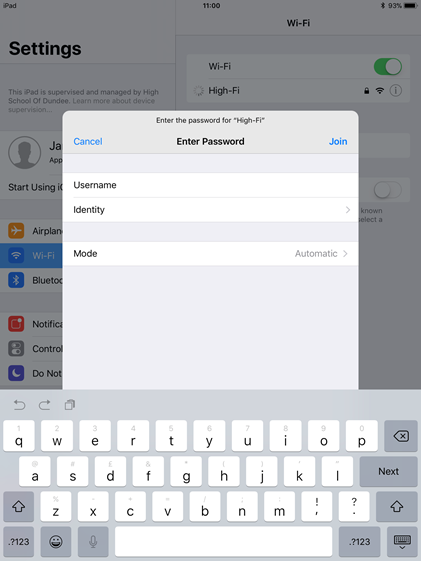
Just as a bit of an update on my description above iOS10 does request the user to enter new password when it changed however it look like this issue may be an apple problem as on ipads running iOS10 when a user changes their password they get the following screen which is current:
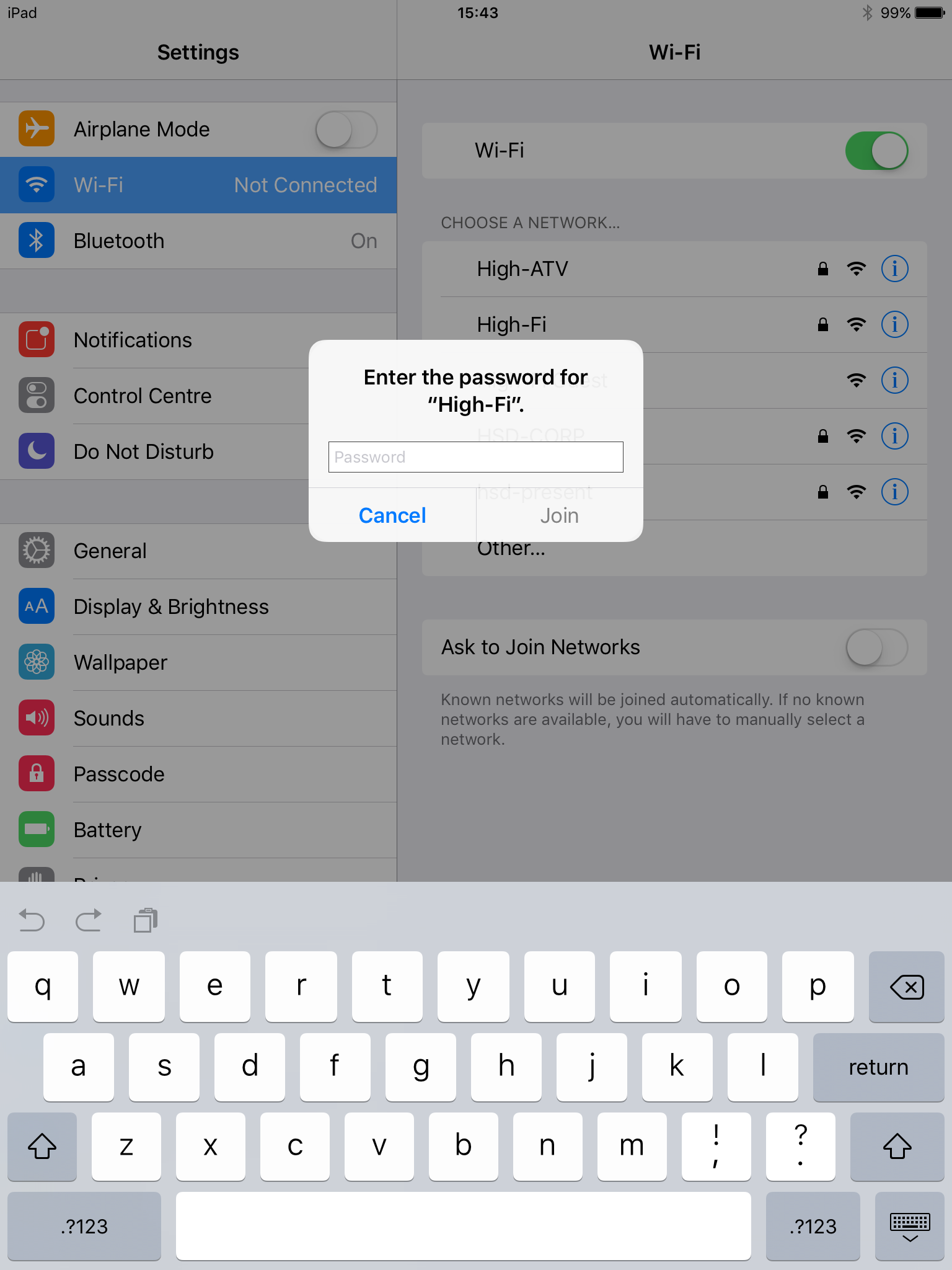
in iOS 11.0.3 they get this screen asking for identity:
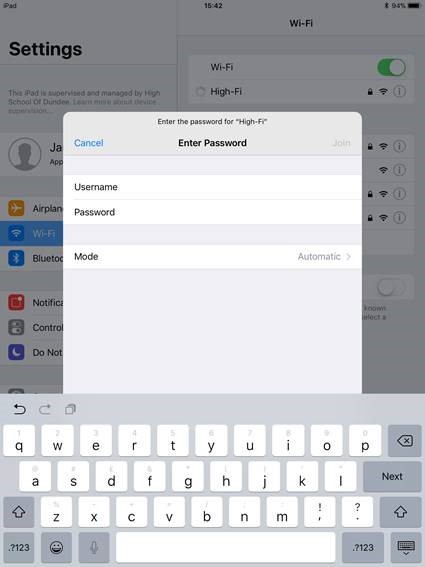
and now since iOS11.1 bata 3 some progress has been made and the following screen is displayed:
Issue back with apple and im waiting on a reply from support
Will keep the post updated when I hear back from Apple
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-02-2017 09:28 AM
Any reply yet?
I have the same issue I think...
IOS 11 came out and now devices can't connect to my 802.1X SSID when they were working prior. It appears they're trying to do EAP-TLS when they should be doing EAP-MSCHAPv2. It just says "can't connect" when I try. Uname/Pword are pushed down from an MDM policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-02-2017 09:58 AM
Afternoon Adam,
Sound like the same issue to me, although the ticket with Cisco TAC still open they believe it an Apple problem. The last update I got from the Apple Enterprise Support Team on the 27th October was that their engineers have had this behavior reported to them and it being worked on however they cannot confirm a patch date.
I have asked them for a bug number in the hope to track it better however i'm hoping by the reply I got Apple have taken ownership of the fault.
Currently the only work around I have is for the users on iOS11 to upgrade to iOS11.1 and remove any WiFi profiles that may be on the devices. for us our ISE pushed out the WiFi profile with a CA certificate.
The issue still remains however that the iPads try to connect a number of times each time the password authentication fails as seen in the the radius logs but it seems to me that the ipads are unable to recognize an incorrect password. eventually after pressing to connect to the wifi a few times the incorrect password notification appears and allows you to enter username and password.
It would be worth you raising the fault with the Apple Enterprise Support Team and reference my call to put some more pressure on Apple our case id is 20000002095460
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-02-2017 10:51 AM
Unfortunately some supplicants don’t be have that well
Have you considered using certificate authentication instead?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2017 07:53 AM
Hello, I had the same issue after upgrading from 1.4 to 2.0.0.306, installing patch-5 last night fixed the IOS issue, and windows 10 issues as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2017 08:35 AM
If ISE 2.0 Patch 5 also fixes Windows 10, then it seems you are hitting CSCuw88770. And, that might not be the same discussed here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2017 08:39 AM
Agreed, I was working on Win10 issues related to CSCuw88770, but in our case, it also happened to fix IOS devices running IOS 11..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2017 08:43 AM
Apple iOS 11 negotiates to use TLSv1.2 when connecting to an ISE running 2.0+ so CSCuw88770 applies.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2017 01:35 PM
Will give the patches a go, can I confirm 1 thing CSCuw88770 is part of patch 1 should I have ISE2.0.0.306 patches 1,2,3,4 and 5 installed as currently only have 4
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide