- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Firewall ports to open for Guest WebAuth with ISE 2.3 Inside
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Firewall ports to open for Guest WebAuth with ISE 2.3 Inside
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2017 11:53 AM - edited 02-21-2020 10:40 AM
I am setting up a Guest Sponsor Portal, with ISE 2.3 which is hosted on the Internal network.
I am dropping my guest wireless users in the DMZ and need to open the appropiate firewall ports on the firewall to make this work.
Can anyone point me to any good resources or advise what ports need to be opened each way?
Thanks
Roger
- Labels:
-
Other NAC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2017 12:37 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2017 12:42 PM
I only have one ISE instance and that is running all personas and is hosted on the Internal network.
I have guest wireless users being dropped into the DMZ
So what ports need to be opened to allow this guest user to hit the web portal and get authenticated?
i assume they get dropped into DMZ and hit the WebAuth ACL and can only see ISE
Just a bit confused about that being internal and client in DMZ
I do not plan to put a PSN in the DMZ
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2017 01:54 PM - edited 11-22-2017 02:02 PM
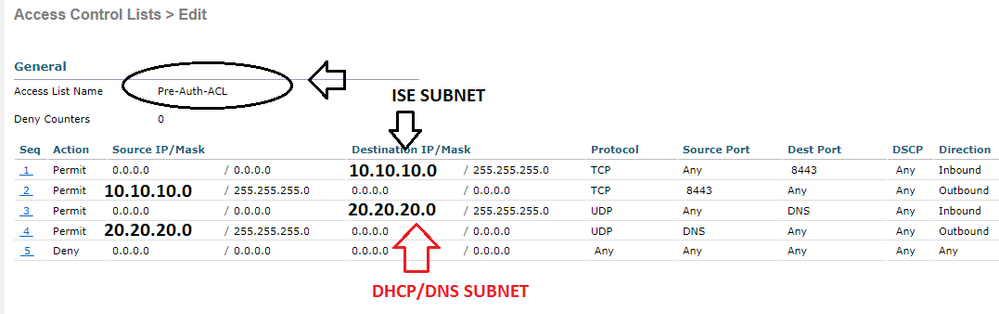
Based on your WLC Preauth ACL, check if you are allowing traffic from Enduser/WLC to DHCP/DNS/ISE:8443 subnets on your FW.
On my case I am just allowing the following but under your scenario looks like you need to adjust accordingly the FW because you are using DMZ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2017 02:04 PM
So is all I need to allow from a guest user in the DMZ is access to ISE:8443 ?
Surely it must need more?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2017 02:13 PM - edited 11-22-2017 02:14 PM
Check first if your device on guest ssid is getting a VALID IP from the wlc interface. If that part is ok, then the only thing you need is allow traffic from Guest subnet/WLC to ISE on port 8443. IMPORTANT to mention that the WLC Guest SSID requires an URL Redirect to the ISE Login portal for Guest like this: (you have to copy this link from ISE directly and change the IP by the FQDN of ISE)
https://guest.domain:8443/portal/PortalSetup.action?portal=10be2e90-8001-11e5-b027-3440b5d4e810
On the other hand, are you allowing traffic from the WLC subnet to the ISE server for Authentication on port 1812 and 1813?. If not, check this part as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2017 02:18 PM
I have currently got a 3504 with one interface dropping guest wireless users in a DMZ
They get their IP from the firewall interface and get access to the internet
SSID auth is via PSK
I now want to use an internal ISE server to implement Guest Portal
So need to work through the flow
So wireless client connects to open SSID and gets dropped into DMZ
Gets an IP but can only talk to ISE
That client will need
ISE:8443
1812 and 1813 open to ISE for authentication.
What needs to be open from ISE to guest user?
This seems very logical but I can't find a simple step by step design of how this works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2017 02:35 PM - edited 11-22-2017 02:40 PM
Try CWA for your guest authentication.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2017 02:55 PM
Perfect, that is just what I was looking for but didn't know what it was called!
So in terms of firewall rules
Do I need to allow these both ways or just DMZ to ISE
As I don't think there is any traffic initiated from ISE in this process?
- UDP:1645, 1812 (RADIUS Authentication)
- UDP:1646, 1813 (RADIUS Accounting)
- UDP:1700 (RADIUS CoA)
- TCP:8443 Guest Portal or 8905 if you have Posturing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-23-2017 07:16 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-23-2017 07:18 AM
Thanks and are these both ways? Or just DMZ to ISE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-23-2017 07:19 AM
Make it both ways.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: