- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Fortigate authorization with ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2016 06:36 AM
Hi,
Anyone has done Fortigate firewall radius authorization with ISE ?
What are the Radius attributes ? I tried with
Fortinet-Group-Name
Fortinet-Access-Profile ; but not successful
Regards
Nimmi
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2016 09:33 AM
Nimmi,
You will need to consult the Fortinet Firewall documentation for the required attributes for a successful authorization.
We have not done any explicit testing with Fortinet products but because ISE supports any standard RADIUS communications with Vendor Specific Attributes (VSAs) it should work. I searched for "fortinet radius authorization attributes" and found the Fortinet Knowledge Base article Fortinet RADIUS vendor-specific attributes (VSAs) which lists the following VSAs:
#
# Fortinet VSAs
#
VENDOR Fortinet 12356
BEGIN-VENDOR Fortinet
ATTRIBUTE Fortinet-Group-Name 1 string
ATTRIBUTE Fortinet-Client-IP-Address 2 ipaddr
ATTRIBUTE Fortinet-Vdom-Name 3 string
ATTRIBUTE Fortinet-Access-Profile 6 string
#
# Integer Translations
#
END-VENDOR Fortinet
I have also attached the above text as a plain text file named Fortinet_VSAs.txt for you to import into ISE.
To import these attributes into ISE:
1) Navigate to Policy > Policy Elements > Dictionaries
2) In the Dictionaries left panel, choose System > RADIUS > RADIUS Vendors
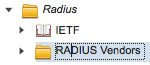
3) You should see a list of RADIUS Vendors that does not include Fortinet
4) Select Import
5) Browse... for the Fortinet_VSAs.txt file then click the Import button and acknowledge the dialog to import the file.
6) You should now see Fortinet in the RADIUS Vendors list:

and all of the Fortinet attributes listed under the Dictionary Attributes tab:
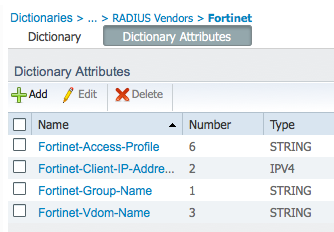
So you can use these attributes in your ISE Authorization Profiles per the Fortinet requirements / recommendations.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2016 09:33 AM
Nimmi,
You will need to consult the Fortinet Firewall documentation for the required attributes for a successful authorization.
We have not done any explicit testing with Fortinet products but because ISE supports any standard RADIUS communications with Vendor Specific Attributes (VSAs) it should work. I searched for "fortinet radius authorization attributes" and found the Fortinet Knowledge Base article Fortinet RADIUS vendor-specific attributes (VSAs) which lists the following VSAs:
#
# Fortinet VSAs
#
VENDOR Fortinet 12356
BEGIN-VENDOR Fortinet
ATTRIBUTE Fortinet-Group-Name 1 string
ATTRIBUTE Fortinet-Client-IP-Address 2 ipaddr
ATTRIBUTE Fortinet-Vdom-Name 3 string
ATTRIBUTE Fortinet-Access-Profile 6 string
#
# Integer Translations
#
END-VENDOR Fortinet
I have also attached the above text as a plain text file named Fortinet_VSAs.txt for you to import into ISE.
To import these attributes into ISE:
1) Navigate to Policy > Policy Elements > Dictionaries
2) In the Dictionaries left panel, choose System > RADIUS > RADIUS Vendors

3) You should see a list of RADIUS Vendors that does not include Fortinet
4) Select Import
5) Browse... for the Fortinet_VSAs.txt file then click the Import button and acknowledge the dialog to import the file.
6) You should now see Fortinet in the RADIUS Vendors list:

and all of the Fortinet attributes listed under the Dictionary Attributes tab:

So you can use these attributes in your ISE Authorization Profiles per the Fortinet requirements / recommendations.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2017 10:33 AM
Hi Thomas,
I know this is an old post but I wonder if you can provide me with the rest of the configuration on ISE so I can Authenticate admin login to Fortigate.
Regards
Gamal Mohamed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2017 10:42 AM
Fortigate is not our product so you are best to consult Fortigate support, as Thomas suggested.
SSL VPN with RADIUS authentication from the Fortinet Cookbook might help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2017 10:52 AM
Hi Hslai,
Many thanks for your reply.
But can you help me configure the ISE part like authentication and authorization rules and any necessary configuration?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2017 11:46 AM
Have you tried configuring authentication and authorization without success? If so, maybe you can share your configuration and logs so the community can try to help you.
George
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2017 12:12 PM
We do not test this 3rd party device so can't tell how it working exactly.
Remote Admin login with Radius selecting admin access account profile looks like it allows using RADIUS to perform device admin so ...
- Import or define the RADIUS vendor dictionary for Fortigate, as Thomas showed
- Define an allowed-protocol set or use the existing one to match what configured in Fortigate
- Define an authorization profile that returns the required vendor attributes. An example shown in the screenshot
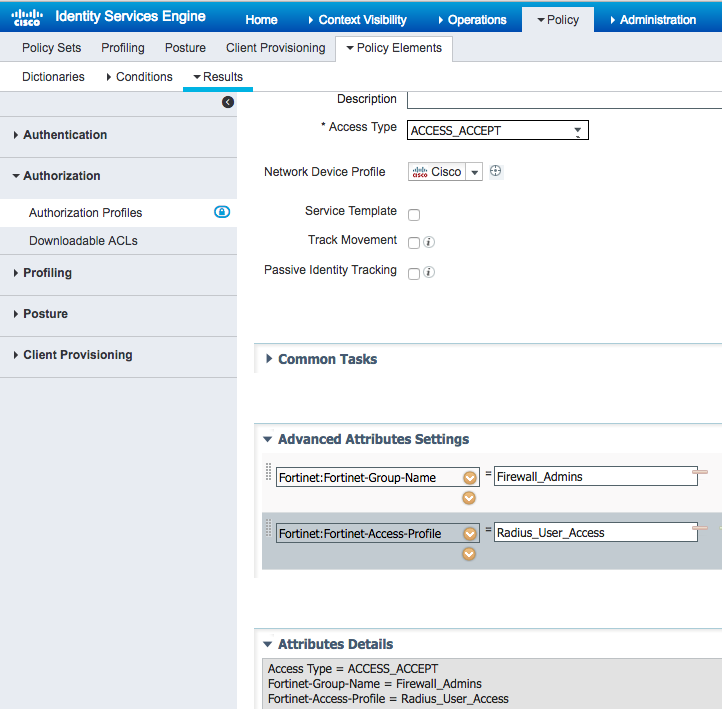
- Define a Network Device group for Fortigate
- Define a Network Device for Fortigate and specify (4) as its group
- Define some internal users or add external ID sources and/or define an ID source sequence
- Create a policy set to condition on (4)
- In the default authentication policy rule, use (6) as the ID source. Or, you may create additional rules as needed.
- In the default authorization policy rule, use (3) as the result. Or, you may create additional rules as needed.
Good luck!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2017 03:40 AM
Hi Hslai,
I really appreciate your help.
It works ![]()
Regards
Gamal Mohamed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2017 10:20 AM
I am glad that you are able to get it working. If you have some time, please contribute it as a how-to doc in our community and provide details, such as the product versions you tested.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2018 02:03 PM
Hola Gamal Mohamed,
Tienes algun documento de el proceso que realizaste para integrar fortinet?
Podrias compartilo?
Gracias.
Saludos.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2018 12:08 PM
Hi Hslai
Can you help with the attributes for the authorization profile, these attributes where they were obtained? because i configure the similar situation.
Thanks for your help.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2018 12:43 PM
Please follow Comment 1. and then Comment 6.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide