- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: how to authorize switch port when ISE is down
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2016 02:08 PM
Hello,
i'm trying to implement how to authorize the switch port when ISE nodes are dead
i tried some commands but i see that only one endpoint can work ip phone or pc ?
authentication event server dead action authorize vlan x
authentication event server alive action authorize voice
authentication host-mode multi-domain
so is there a way to authorize both endpoints when ISE is dead ? can i use service policy for example ?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2016 04:12 AM
Kareem, run 'dot1x critical eapol' global command and try the test again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2016 05:43 PM
If not already done, please check out this how-to How To: Universal IOS Switch Config for ISE and the other guides on Cisco Switches might be of interest to you, too.
Your inquiry is actually more on the switch side so I would suggest to seek support from Cisco switch platform team if you have further questions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-31-2016 04:12 AM
Hello,
thanks a lot for the document but the PC is always stucked in dot1x authentication it is always running so PC never gets the critical vlan but ip phone worked perfectly . when i removed anyconnect from the PC it gets the critical vlan
so i guess the problem in timeouts maybe or something else and here is the switch command
interface GigabitEthernet1/0/15
switchport access vlan 15
switchport mode access
switchport voice vlan 248
authentication event fail action next-method
authentication event server dead action authorize vlan 15
authentication event server dead action authorize voice
authentication event server alive action reinitialize
authentication host-mode multi-domain
authentication order dot1x mab
authentication priority dot1x mab
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
authentication violation restrict
mab
mls qos trust device cisco-phone
mls qos trust cos
dot1x pae authenticator
dot1x timeout tx-period 10
spanning-tree portfast
spanning-tree bpduguard enable
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2016 07:14 AM
Are you seeing this issue with new authentications? If a DOT1X client already authorized, I do not think it would get put into critical VLAN. Also, it might depend on the AnyConnect NAM profile to allow DOT1X auth failures.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2016 10:51 PM
Hello,
yes i'm talking about new clients trying to connect when radius is dead and your suggestion is already enabled !!
the problem is that dot1x is keeping running it never fails in the switch !!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2016 04:12 AM
Kareem, run 'dot1x critical eapol' global command and try the test again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2016 02:21 AM
not working i should allow data before authentication from anyconnect and this is not acceptable
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2016 04:51 PM
Have you tried it with Windows native supplicant? I would expect the same result as your AnyConnect NAM tests.
Please detail which switch model and Cisco IOS release on the switch. As I mentioned before, this is a switch feature, it's best to seek support from the switch platform teams.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2018 03:29 AM
Hi Kareem,
Is there any luck on the issue. We do have the same issue with the PC's installed with Anyconnect. It is stuck in authentication. PC's without anyconnect works fine and getting the critical auth VLAN but no luck for anyconnect installed machines.
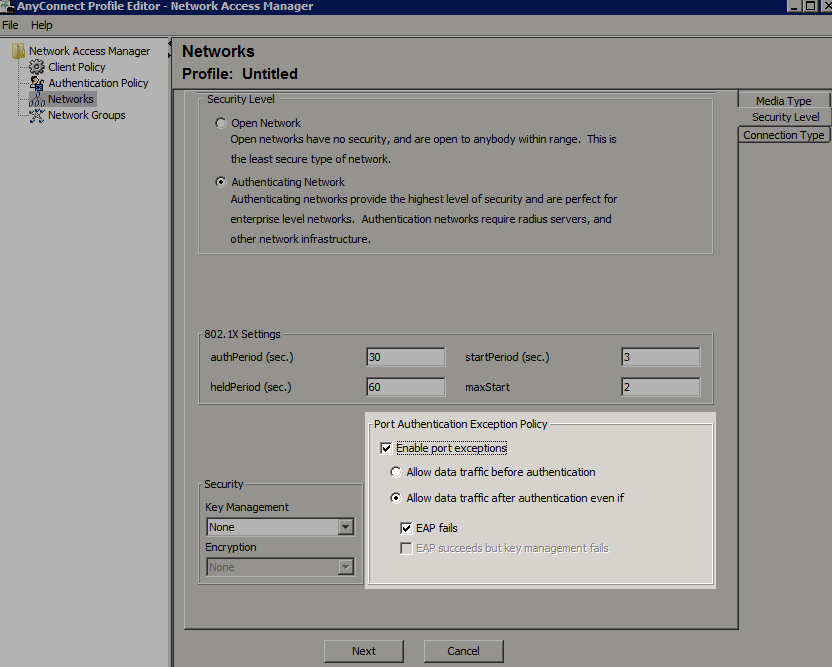
Tried the option Enable the port exception mentioned above but same result
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2018 03:41 AM
Hello Deepu,
i'm using the below switch template and it's working with anyconnect and without anyconnect
dot1x system-auth-control
dot1x critical eapol
interface GigabitEthernet w/x/y-z
switchport access vlan X
switchport voice vlan y
switchport mode access
authentication event fail action next-method
authentication event server dead action authorize vlan X
authentication event server dead action authorize voice
dot1x pae authenticator
dot1x port-control auto
authentication order dot1x mab
authentication priority dot1x mab
mab
dot1x timeout tx-period 10
authentication periodic
authentication timer reauthenticate server
authentication host-mode multi-domain
snmp trap mac-notification change added
spanning-tree portfast
exit
anyconnect configuration was allow data before authentication
i faced a disaster with a customer last month when all ISE nodes was down and AD was down but nobody complains because the critical VLAN applied to all interfaces.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2018 05:54 AM
Hi Karem,
Thank you for your quick reply. Much appreciated. I am using the same template on switches. But still the same problem. Could you please help how do you configure "anyconnect configuration was allow data before authentication" ?. Do you have the configuration.xml sample so that i can check the setting. My email ID is deepu.vargheset@gmail.com. Please send if possible.
Thanks,
Deepu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2018 08:54 AM
It seems like you are talking about anyconnect NAM to allow network access when dot1x fails? This has nothing to do with ISE or the switch
Please reference the anyconnect document
https://www.cisco.com/c/en/us/td/docs/security/vpn_client/anyconnect/anyconnect40/administration/guide/b_AnyConnect_Administrator_Guide_4-0/configure-nam.html#ID-1424-00000172
If more questions on anyconnect nam please move this to the anyconnect forum
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2018 01:55 AM
Kareem Ali wrote:
Hello Deepu,
i'm using the below switch template and it's working with anyconnect and without anyconnect
dot1x system-auth-control
dot1x critical eapol
interface GigabitEthernet w/x/y-z
switchport access vlan X
switchport voice vlan y
switchport mode access
authentication event fail action next-method
authentication event server dead action authorize vlan X
authentication event server dead action authorize voice
dot1x pae authenticator
dot1x port-control auto
authentication order dot1x mab
authentication priority dot1x mab
mab
dot1x timeout tx-period 10
authentication periodic
authentication timer reauthenticate server
authentication host-mode multi-domain
snmp trap mac-notification change added
spanning-tree portfast
exit
anyconnect configuration was allow data before authentication
i faced a disaster with a customer last month when all ISE nodes was down and AD was down but nobody complains because the critical VLAN applied to all interfaces.
Hello Kareem,
We have tried the option "data before authentication" in anyconnect configuration but the issue remains the same. Anyconnect is showing authenticating and on switch side dot1x is running and never fall back. We stopped the services of anyconnect and everything working fine as expected. So i believe we need some tweaking in anyconnect profile. Any idea ?. As below mentioned by Jason, do we need to post put discussion on anyconnect group ?
Are you using "authentication open" command on switch ports ?.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2018 02:10 AM
Hi,
I didn’t configure any special configuration for Anyconnect I just configured allow data before authentication and the remaining settings is the default settings .
From switch side the switch has to mark the ISE as dead in order to apply critical vlan . so do you see ISE dead ?
From switch configuration I do radius test every 5 minutes I believe this is important . here is the whole template I use in the switch
global configuration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2018 02:14 AM
Thanks Kareem for your reply. Could you please provide the global configuration for a reference.
Thanks
Deepu
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide





