- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE 2.2 - Permanently hide false negatives in ISE Live Logs / Logs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE 2.2 - Permanently hide false negatives in ISE Live Logs / Logs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-26-2018 08:30 AM
Hi
I am using split authentication / authorization in a ravpn setup (ASA used to terminated the VPNs). Authentication is done by a third party software using SAML and Authorization done by ISE. The SAML IdP in question has no RADIUS interface.
As in RADIUS we cannot separate the authentication session from the authorization and as the SAML authentication is a two factor one, for each stage of authentication
we get a failed authentication log in ISE (two failed authentications for each ravpn session authentication).
Are you aware of a way / filter that could allow us to permanently filter out and hide the 'false negative' failed authentications so that we can only keep the authorization related session logs /data?
Many thanks
Istvan
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-26-2018 12:46 PM
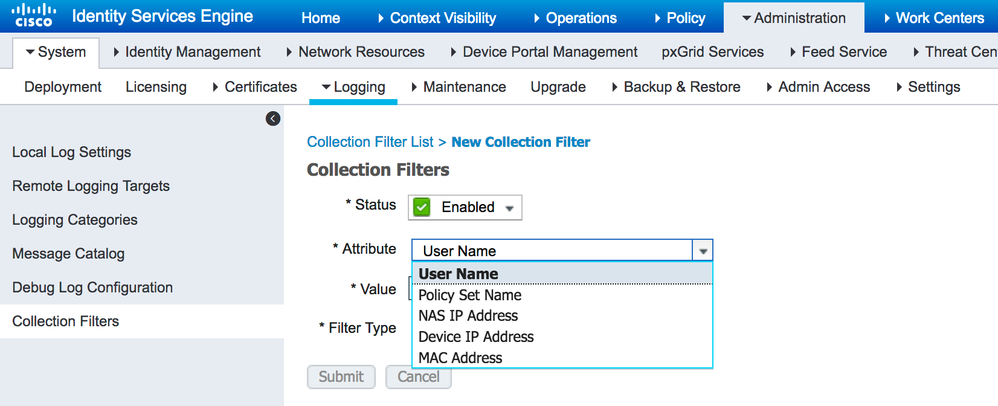
Please explain why you are getting two failed auths for each session. The authentication usually continue with authorization. You might want to try a collection filter.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2018 03:08 AM
Hi,
Thank you, I will try the suggestion.
I am getting two failed authentications for each RAVPN session due to the following:
- ASA is configured to use a SAML IdP for authentication and ISE for authorization
- SAML : authentication is a two factor one in the solution I am working on, i.e. first session is a user and pass based authentication, then if this succeeds an SMS is sent to the user with an access code, once the access code has been entered the second session completes and the user is fully authenticated.
- RADIUS : For each of the two authentication sessions mentioned above in the context of SAML, the ASA will send a RADIUS Access-Request to the ISE and will get an Access-Reject from ISE, which is normal, hence the reason i was referring to these as false negatives. Same RADIUS sessions will be used for authorization, specifically the second one will be the one which will send sufficient attributes to ISE (Cisco AnyConnect Identity Extensions (ACIDex)).
Thank you
Istvan
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: